MySQL Database Servers Could Become New DDoS Attack Vector
MySQL database servers, which millions of organizations worldwide rely on for backend database services, could soon be leveraged in massive DDoS attacks because of a dangerous malware variant known as Chikdos. Chikdos was first discovered by Polish cybersecurity experts over two years ago. Chikdos, an extremely dangerous Trojan originally developed to target the Linux operating system, is typically installed through an SSH dictionary attack. By downloading and executing a simple .bot file upon logging into a compromised server, Chikdos is installed primarily as a means to launch DDoS attacks using DNS amplification. Although the original version of Chikdos specifically targeted Linux systems, a more recent version has also been discovered that is capable of infecting the Windows operating system as well. MySQL database servers can be run on either the Linux or the Windows platform. This makes Chikdos especially dangerous as it is capable of affecting practically every MySQL server connected to the Internet (either directly or through an intermediary machine that has already been compromised). When originally analyzed by security researchers, it was determined that Chikdos was created solely for the purpose of launching DDoS attacks against a variety of Web targets. Although DNS amplification is the malware’s attack vector of choice, there are three other attacks possible after a Chikdos infection has occurred. For those unfamiliar with the term, a DNS amplification attack spawns from a request containing 256 random or previously defined queries to the backend database is transmitted to a DNS server.
Researchers have also found other functions, many of which were not implemented at the time of analysis, that could be used to leverage the HTTP protocol during a DDoS attack. While Chikdos has been deployed against targets many times since being discovered in 2013, a recent discovery by security researchers at Symantec indicates that a new variant of Chikdos is circulating the Internet. Unlike the previous version of this malicious program, the new version of Chikdos attempts to exploit the user-defined function (UDF) capabilities inherent to the MySQL database engine. The UDF function was created as a way for developers to use compiled code to extend the functionality inherent to the MySQL platform.
By exploiting known SQL injection vulnerabilities, the cybercriminals behind this latest threat are able to inject malicious UDF code into the backend databases of websites relying on MySQL.
Once these malicious codes have been injected into a database table, hackers execute the DUMP SQL command, effectively saving the injected code as a library file. This rogue library file is then executed by the primary MySQL process and ultimately, Chikdos is installed on the target machine. Once successfully installed on a system, Chikdos can leverage the bandwidth of the machine to execute massive DDoS attacks. Since the only purpose of this malware is to create powerful DDoS attacks against targets of the hackers behind this campaign’s choosing, the primary targets for Chikdos infection include servers and other connected devices with access to large amounts of bandwidth.
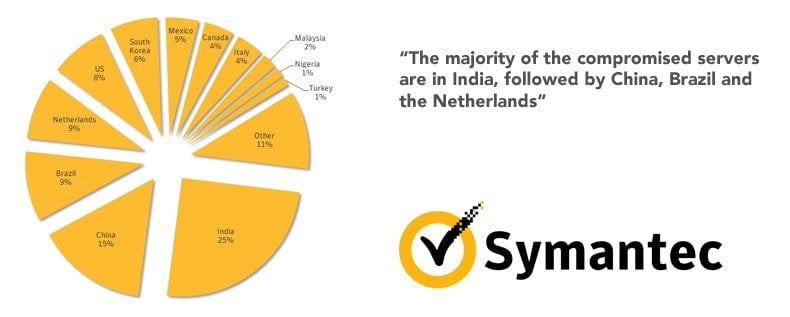
The researchers at Symantec have discovered MySQL servers already infected with Chikdos in numerous countries around the world. As of this writing, Chikdos has been positively identified in China, Brazil, the U.S., Netherlands, Mexico, South Korea, Italy, Canada, Nigeria, Turkey, and Malaysia. Of the countries affected by this malware variant thus far, it appears that the largest concentrations of infections were present in India and China. While the malicious actors behind this attack have yet to be identified, security researchers have noted that during the research phase of this threat, Chikdos was successfully used to launch DDoS attacks against a popular U.S. hosting provider as well as an unidentified IP address based in China. Creating botnets for the purpose of launching devastating DDoS attacks against targets of the hackers’ choosing is nothing new but the use of MySQL servers to accomplish this task is a fresh technique that could have grave consequences for any business targeted by a Chikdos botnet DDoS campaign.
This threat is especially dangerous for two reasons: 1. MySQL is an extremely popular database application for backend Web services. Millions of websites around the world use this platform and this means that the number of potential Chikdos targets is enormous compared to more specialized malware campaigns that target a small subset of Internet-connected devices. 2. MySQL servers are typically afforded access to large amounts of bandwidth on a given network – much more bandwidth than is typically allotted to regular PCs and even most application servers.
This makes MySQL servers an ideal candidate for use in large-scale DDoS campaigns with enough power to take out practically any Web-based service despite the proper implementation of DDoS countermeasures on the target side.
In other words, if enough bandwidth is available for a DDoS attack, there is no security solution (hardware or software) capable of protecting the targeted service from becoming overloaded with DNS amplification requests. The best way to avoid a Chikdos infection is to ensure that administrative privileges for any MySQL server installations on the network are locked down following security best practices for preventing exploitation via SQL injection attack vectors. System administrators managing MySQL databases should verify the absence of a Chikdos infection by checking in commonly used folders including \Lib\, \Lib\plugin\ and \Bin\. When searching through these folders, look for any .DLL files with random names that appear suspicious or out of place.
The presence of these random .DLL files could indicate a Chikdos infection on the server and immediate steps should be taken to isolate and remove the threat. Although it’s worth noting that the new version of Chikdos specifically targets MySQL servers by exploiting SQL injection vulnerabilities, the hackers behind the latest Chikdos campaign could modify the code to target a wider range of devices operating on Windows at any time. If your PC or network uses database services accessible via the Internet, ensure that all precautions to prevent SQL injection vulnerabilities from being exploited have been implemented to protect against this dangerous threat.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion