New Ransomware Threat Targets Websites
One of the more common types of malware to threaten PC users over the last several years has been ransomware. Covered extensively on this blog, ransomware is malicious code that secretly encrypts the files and folders of an infected computer using state-of-the-art encryption techniques. Once encryption of all files and folders has been completed, the victim is presented with a message that demands a ransom (typically paid in Bitcoin) be paid to receive the key required to unlock these files. In some of the most extreme ransomware variants, there was absolutely no way to retrieve these files without paying the ransom and often, victims were “punished” for not paying up right away because the amount of ransom due in exchange for the decryption key would increase after a set period of time had elapsed. While these types of malware are still a serious threat to PC users around the world, most antivirus software programs have become adept at detecting and blocking the installation of these programs before any damage can be done. As is usually the case when one malware variant is neutralized, hackers have recently devised a new way to leverage the power of ransomware: targeting websites. Rather than hold a single PC for ransom, hackers have created a way to hold the files, pages, and images of a website for ransom – essentially making that website inaccessible until the ransom is paid. The latest threat, originally discovered by the Russian security firm Dr. Web, has been dubbed Linux.Encoder.1. This malware variant specifically targets websites that are powered by the Linux operating system (a common platform used by websites around the world). Popular Web hosting platforms based on Linux include Apache and Nginx and both of these platforms are vulnerable to infection by Linux.Encoder.1. This malware variant is especially dangerous because it is almost impossible to detect using standard antivirus tools.
When scanned by Virus Total, almost no modern security tools or detection algorithms were able to detect Linux.Encoder.1 before it was too late. This malware is typically injected into a Website using known vulnerabilities in site plugins and third-party software including popular shopping cart programs. Once this malware variant has infiltrated a host machine, Linix.Encoder.1 quickly begins creating havoc by encrypting all files in the websites home directory. Once the home directory (where most of the website content is stored) has been encrypted, the malware moves on to the backup directories and other system folders associated with a typical website installation. This includes most of the files, images, code libraries, scripts, and pages that comprise a typical website.
By infecting the home and backup directories, it makes it impossible for a webmaster to recreate the website from the content stored on the infected host machine.
Ransomware is a growing problem and just a few months ago, the FBI released a report that described ransomware-related losses in 2014 that exceeded $18 million. The report also detailed nearly 1,000 CryptoWall-related complaints in 2014 (CryptoWall is one of the most dangerous and powerful ransomware variants to date). Last week, a server used by a professional Web site designer was infected with Linux.Encoder.1. The Web designer found a plain text file called “instructions to decrypt” in every file directory affected by the malware. This file read: “To obtain the private key and PHP script for this computer, which will automatically decrypt files, you need to pay 1 Bitcoin (~420 USD). Without this key, you will never be able to get your original files back.”
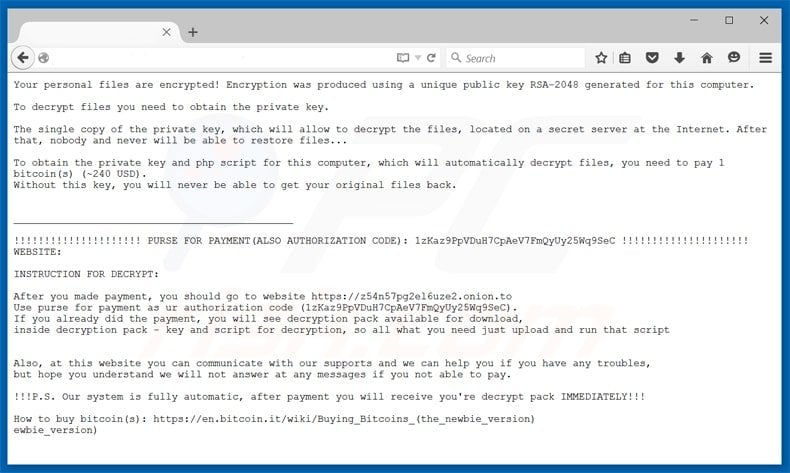
Here's the full text of the ransom demanding note:
Your personal files are encrypted! Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key. The single copy of the private key, which will allow to decrypt the files, located on a secret server at the Internet. After that, nobody and never will be able to restore files... To obtain the private key and php script for this computer, which will automatically decrypt files, you need to pay 1 bitcoin(s) (~240 USD). Without this key, you will never be able to get your original files back. INSTRUCTION FOR DECRYPT: After you made payment, you should go to website https://z54n57pg2el6uze2.onion.to Use purse for payment as ur authorization code. If you already did the payment, you will see decryption pack available for download, inside decryption pack - key and script for decryption, so all what you need just upload and run that script. Also, at this website you can communicate with our supports and we can help you if you have any troubles, but hope you understand we will not answer at any messages if you not able to pay. !!!P.S. Our system is fully automatic, after payment you will receive you're decrypt pack IMMEDIATELY!!! How to buy bitcoin(s): https://en.bitcoin.it/wiki/Buying_Bitcoins_(the_newbie_version).
The malware infection occurred on a development Web server but unfortunately for the victim, the Web server also hosted a few websites that hadn’t been backed up in quite some time. The encryption attack rendered those sites unusable, forcing the victim to pay the ransom just to get access to these websites again. After setting up a Bitcoin wallet for the first time, the victim in this case did receive the decryption key from the hackers as promised although he noted that the PHP script used to decrypt the infected Web server has some glitches due to the appearance of some random commas and extra spaces in some of the newly decrypted files. In this instance, the malware was able to gain access to the Web server by exploiting a vulnerability in Magento, a popular shopping cart software solution used by numerous websites to handle ecommerce payments.
It’s important to note that Magento isn’t the only third-party Web service vulnerable to attack and that smaller e-commerce sites are especially vulnerable to exploitation because these sites are less likely to install critical security updates in a timely manner. Linux.Encoder.1 is only one of the new ransomware threats to emerge in recent weeks. The Romanian security firm Bitdefender recently discovered a new iteration of the notorious CryptoWall malware (aptly named CryptoWall 4.0 by the hackers behind its release). This new version boasts a redesigned ransom page as well as a new feature that actually encrypts the names of the files on the infected machine as well as each file’s data. Another recently discovered threat, known as Power Worm, was brought to light by BleepingComputer.com, a website and blog that has been at the forefront of computer security for years. What’s especially concerning about Power Worm is that the code for the malware is defective to the point that even if a victim pays the ransom, the encrypted files are unrecoverable.
According to Lawrence Abrams, a blogger from BleepingComputer.com, a coding mistake is responsible for this ransomware snafu. Protecting your PC and any Web properties you own is as simple as keeping your OS, hosting platform, and all third-party applications up-to-date. Linux.Encoder.1, CryptoWall, and other ransomware variants target known vulnerabilities in Windows, Linux, and popular Web hosting platforms. These malware variants also target third-party applications and Web services which should be updated regularly to prevent infection.
If a website is hosted by a third-party hosting provider, make sure that hosting provider is performing regular updates to the hosting platform and if that company fails to do so, look for another hosting provider as soon as possible. Also, make sure to perform regular backups of all PCs and hosting servers as this is one of the only ways to combat a ransomware infection once it has already occurred. The backup must be on a separate machine (or VM) to protect the backup from encryption after infection as most modern ransomware variants attempt to encrypt and files or systems they can access once a system breach has occurred. Webmaster who have fallen victim for this ransomware can use a free tool developed by BitDefender Labs to decrypt the compromised data for free.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion