The Android Stagefright Virus
Stagefright is an Android vulnerability that some have called the worst Android security problem ever. A hacker can use this to gain root access to an Android device simply by calling a phone and sending it a specially constructed MP4 media file in an MMS (multimedia message). MMS messages are processed by WhatsApp, Google Hangouts, or the ordinary Android messenger app. The exploit works by causing an error in the media player which a hacker can use to gain access to memory. This bug impacts Android versions between 2.2 and 5.1. There are patches available. Plus users can turn off the automatic downloading of videos in those apps. But not all Android devices are patched yet even though the bug was discovered some months ago in 2015. This is because patches are pushed out at different schedules by the phone manufacturers and cellular carriers.

For example, we tested a Nexus 4 smartphone running Android version 4.2.1. That phone had not been patched. We used the Stategright Detector app which is available on Google Play here to run the test.
The app gave this result:
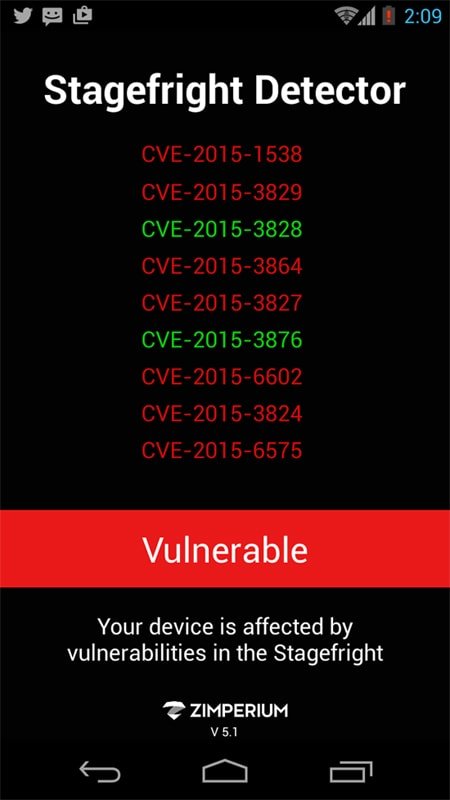
The CVE (common vulnerabilities) numbers shown in the app shown above are assigned by the nonprofit firm MITRE who tracks these items based on data provided by security researchers. For example one Stagefright weakness is documented here. There are several.
Security researcher Joshua Drake found the problem and wrote the fix here.
You can see a video demonstration of the bug here.
It is not know how many people have been affected by this vulnerability but all unpatched Android devices have this problem. Since the vulnerability is well-documented on the Android opensource code project site a hacker could certainly write an exploit. They could even use the code written Mr Drake himself.
The Android bug is assigned the number ANDROID-20139950.
Responsibility for patching the Nexus 4 device we mentioned above lies with Google since the Nexus device are manufactured for Google by another company. If it had been, for example, a Galax then Samsung would have been responsible for compiling the fix into their version of Android. The mobile carrier would then push that out.
How the Exploit Works?
The bug works by overflowing the memory of the Stagefright player. Here we explain briefly what that means.
An Android programming running on the Android operating system does not have access to memory outside of the Java Virtual Machine, called Dalvik. That is by design. But Stagefright would have been written in C++, a much lower-level language. With that programming language the programmer is responsible for assigning memory to the program themselves unlike normal Android apps.
In the case of the Stagefright the hacker sends a media message that causes a buffer overflow. That means more data is added to a data field than it is designed to contain thus causing the data sent there to spill over into random memory. The hacker would put instructions and not data into that data field and redirect the running program to execute those. These instructions are assembly language commands which is an even lower level language than C++. In particular the hacker can execute these instructions as demonstrated by Mr Drake in the code excerpt below.
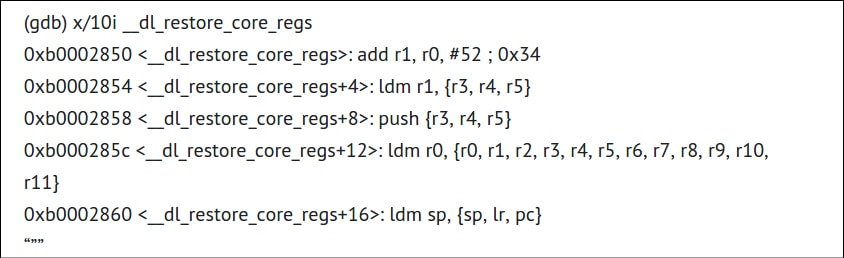
All of that will look like Chinese to the normal person. Just know that those instructions give the player access to command line, meaning root access. That means a hacker could bypass any Android security and install whatever malware they wish.
So download the app to test for the bug then search for the patch provided by your phone manufacturer. And install antivirus software to block the exploit.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion