News Archive August 2013
![]() Written by Karolis Liucveikis on (updated)
Written by Karolis Liucveikis on (updated)
Table of contents:
- Online Banking and E-Commerce May Not Be Secure Thanks to BREACH
- Fake CNN Spam Run Making the Rounds
- FBI Uses Hacking Techniques to Spy on Citizens
- Home and Small Business Wi-Fi Router Vulnerabilities
- The NSA Continues to Intercept Confidential Communications
- A Zero Day Exploit Used for Good?
- Joomla Vulnerability Opens Door to Malware Injection
- Email Collection Tools on Craigslist
- DDoS – More Than Just an Inconvenience
- Another Craigslist Scam
Online Banking and E-Commerce May Not Be Secure Thanks to BREACH
05.08.13
Secure Sockets Layers (SSL) is a security protocol that was originally developed by Netscape for transmitting private information via the Internet. The system works by using two keys to encrypt data – a public key and a private or secret key known only to the recipient of the message. Most online banking websites and e-commerce sites rely on SSL to protect customer payment information or sensitive login details during a session. For years this has been considered a relatively secure method of transmitting data. Although hackable, SSL is very difficult to crack.
That is, until the introduction of a new technique known as BREACH. This technique stands for Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext (BREACH). It is a targeted technique that does not encrypt the entire secure channel. Researchers recently demonstrated the effectiveness of the technique and were able to compromise a SSL session in 30 seconds. The technique works by manipulating data compression techniques to extract small bits of information from HTTPS protected data that include email addresses, security tokens, and other plain text strings.Most websites use a compression algorithm known as Deflate to conserve bandwidth. BREACH exploits this algorithm to extract pieces of encrypt information without having to decrypt the entire string.

The technique has not been perfected just yet and does require embedding an iframe tag in a page frequented by the target user. This ensures that the victim accesses a malicious link that allows the exploit to eavesdrop on encrypted traffic between the victim and a Web server.
Since the technique is capable of recovering secret authentication cookies, attackers could pose as their victims and hijack authenticated web sessions.
This is especially bad news for online banking or e-commerce sessions where account information is freely transmitted within the SSL session. BREACH is an improvement on an earlier design known as Compression Ratio Info- Leak Made Easy (CRIME), another technique that relied on turning compression methods of encrypted Web requests against users.

All current versions of TLS/SSL are at risk from BREACH regardless of the encryption algorithm or cipher being used. Although the demonstration took only 30 seconds, it’s important to note that the technique takes various lengths of time depending on the amount of data being retrieved. Because the embedded malicious link sends thousands of requests to another website where traffic is monitored by BREACH, it could take much longer depending on the type and size of the data being extracted. Either way, hijacking an authenticated session is a hacker’s dream in the world of e-commerce and online banking. Without changes to the SSL format and the Deflate compression algorithm, we are likely to see some significant financial losses imposed by this hacking technique.
Fake CNN Spam Run Making the Rounds
07.08.13
Forbes recently declared Angelina Jolie at the top of their Hollywood’s Highest Paid Actresses of 2013 list and hackers have been quick to take notice. A new rash of fake CNN emails has been unleashed. The spam emails, that are designed to look like CNN news notifications, talk about Jolie’s recognition and try to convince recipients to click on a variety of links that supposedly lead to more detailed articles about Angelina Jolie and her accolade from Forbes.
The contents of the email are pretty convincing and read as follows:
Subject: CNN: Forbes: Angelina Jolie tops list of highest paid actresses
Message body:
(EW.com) – She might not get paid as much as “Iron Man,” but there’s no doubt that celestial beauty Angelina Jolie is smiling all the way to the bank.
This year, Jolie topped Forbes’s annual list of the highest-paid actresses in Hollywood with an incredibly robust $33 million.
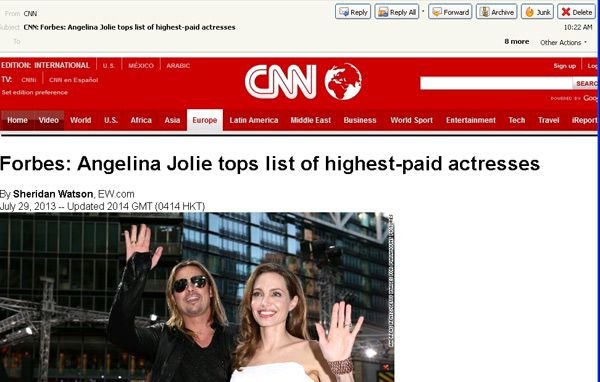
When a recipient clicks on any of the links within the email they are directed to a malicious Adobe Flash Player download which carries a payload of the Zeus banking Trojan. A very similar technique has been used to send out spam emails about the Royal Baby, Harrison Ford, Obama’s Economic Speech, and The Walking Dead recently.
The Zeus banking Trojan steals banking information using man in the browser keystroke logging and form grabbing techniques.
Spread primarily through drive-by downloads and phishing schemes, the Trojan was first identified in 2007 when it was used to steal information from the US DOT.
 In 2010, a major cybercrime network used Zeus to hack into US-based computers and steal approximately $70 million.
In 2010, a major cybercrime network used Zeus to hack into US-based computers and steal approximately $70 million.
Arrests were made in the United States, the UK, and Ukraine as a result of this crime spree. More recently, the current version of Zeus’s source code was leaked and spawned the creation of the Citadel banking Trojan which is very difficult to detect and capable of stealing online banking information while operating undetected. The malicious URLs where the fake Flash Player download originate include:
gbheatings(dot)com/thou/index.html
casa-dor(dot)com/bookstore/index.html
deltadazeresort(dot)net/topic/able_disturb_planning.php
deltadazeresort(dot)net/adobe/update_flash_player.exe
All these domains have been hijacked and you should not visit these sites without a properly setup sandbox environment.
Basically, any time a famous person makes headlines, spammers are right there to capitalize. Even going back to 2008, Angelina Jolie topped the list of “celebrity spammers” with some reports even crowning her as the “Queen of Spam.” Most updated antivirus programs will detect the attempted installation of update_flash_player.exe. Regardless, be suspicious of any unsolicited emails pertaining to celebrity topics to avoid drive-by download infection.
FBI Uses Hacking Techniques to Spy on Citizens
10.08.13
In light of information divulged by world famous whistleblower Eric Snowden, the National Security Agency has been taking most of the heat for spying on American citizens and foreign countries. According to a report by the Wall Street Journal, the FBI has been developing its own set of surveillance tools primarily under the radar. These tools work very similarly to tools used by hackers to collect information including Trojans, spyware, and malware. The FBI creates some of these tools in-house while others are purchased from hacking groups around the world. One of the most alarming of these malware programs is a tool that allegedly allows the FBI to remotely activate the microphones in Android-powered smart phones.
Once the microphone has been activated, the FBI can record conversations without the knowledge or consent of the device owner.
A similar tool has also been developed that can activate the microphone of most laptop computers. Although these techniques are concerning, this is nothing new. The FBI has supposedly been working on tools like this for over 10 years. In 2006, CNET reported on a very similar tool known as a “roving bug.” This software was also capable of remotely activating mobile phone microphones, but wasn’t as alarming or widespread because there were very few unified smart phone platforms at the time. In addition to mobile malware, the FBI and NSA have been attempting to increase surveillance efforts even further. Recently, the US government attempted to obtain the master encryption keys that Internet companies use to shield millions of users’ private web communications from eavesdropping.

These SSL keys would allow the government to decrypt the contents of all communications intercepted through a wiretap or under hazy Foreign Intelligence Surveillance Act regulations. So far, large Internet providers have resisted requests from the government on the grounds that they are illegal. The concern lies more with smaller, localized ISPs who may not have fully staffed legal departments willing to put up a fight against the government. The problem is that it is not entirely clear whether surveillance laws give the government the authority to demand master encryption keys from Internet companies.
Of course, the US government claims that the information obtained from having these master encryption keys would only be used during ongoing criminal investigations, but as history has proven time and again, that is hard to believe.
No matter how you look at it, the FBI and other government entities have certainly taken on an almost criminal persona when it comes to electronic surveillance methods. From custom-built malware to repeat attempts to compromise the integrity of encrypted web traffic, it seems that hackers are not the only online threat anymore.
Home and Small Business Wi-Fi Router Vulnerabilities
12.08.13
A research team recently released information about many consumer Wi-Fi routers that is troubling to say the least. Originally, the team noted that over a dozen home routers had serious security flaws that could easily be exploited by hackers. At Defcon 21, a hacking conference, the team released more devices that are vulnerable and have yet to be patched by manufacturers. The problem is that many people have been trained to think of routers as “set it and forget it” pieces of equipment. After hooking up the Ethernet connection and doing some basic configuration, most consumers do not think about their Wi-Fi router again.
These vulnerabilities seem to affect most consumer grade routers and are difficult to fix. Anyone who connects to these routers is at risk. Small business and home Wi-Fi router administration often relies on weak passwords or static passwords that are the same across multiple stores, like Starbucks or McDonald’s. All a hacker has to do is go to one of these stores, get the Wi-Fi password and use one of the exploits that the research team has discovered. The router would be compromised, as would web traffic flowing through it.

One way to fix this problem would be automatic updates of routers, similar to automatic Windows updates.
However, most people don’t log into their routers or even know how, making automatic updates a difficult road at best.
This means that even if a router manufacturer were to implement an automatic update plan, many users would be unlikely to reap the benefits. On top of that, many of the major router manufacturers are reluctant to address the problems that have been uncovered. This means that these serious exploits could go unpatched for years to come. Three of the affected routers are manufactured by Asus, D-Link, and TrendNet. The Asus router can easily be controlled using a buffer overflow exploit. The D-Link router can be compromised using a web-based and symlink directory traversal exploit and the TrendNet router using a cross site scripting forgery and command injection exploit.

All three of these exploits result in the hacker having a root shell; access to the routers lowest levels of code.
From this vantage point, a criminal has complete control of any and all traffic going through the router and full administrative access to the information contained within the packet data.
Whether the router is at home or at a business, this threat serves as a reminder of how important VPN technology can be while surfing the web. Especially in public Wi-Fi hotspots, which have been known for “man in the middle” and packet sniffing attacks, a VPN can protect against most of these exploits. Even home routers are not safe as they suffer from the same exploits. Many people mistakenly confuse a Wi-Fi router for a firewall appliance and it simply does not have the capability to protect against many attacks. In addition to using secure passwords, a hardware firewall is probably the best way to secure your Wi-Fi network from potential threats.
The NSA Continues to Intercept Confidential Communications
15.08.13
New reports suggest that the NSA is collecting emails and other text communications that are sent internationally or that have been received from outside the United States. It’s no secret that the NSA has been tracking communications of foreigners that it deems threatening to the United States for quite some time. However, the official acknowledgment to the New York Times means that innocent communications with people overseas are being collected by the government. Not only do these email collection efforts include communications with potential overseas targets, but also with anyone who might mention a particular individual or even something partially related to that person. It seems to be one more far-reaching step that the government is taking to monitor Internet traffic; whether legal or not.
The report states that the NSA is acting within the legal framework provided by the FISA Amendments Act of 2008. This legislation allows intelligence officials to monitor domestic communications without a warrant as long as the targeted individual is not a US citizen. Text communications sent overseas or arriving from overseas are run through a computer system within the NSA. The computer system analyzes the messages for specific keywords. If any of these keywords are detected, the message is sent to a human analyst for further evaluation. According to the report, any communications that do not contain these keywords are immediately deleted from NSA computer systems. Unfortunately, the exact extent of data collection is unclear at this time. The keyword system is designed to limit the number of American citizens who inadvertently have their communications caught up in the agency’s data collection efforts.
![]()
The report also suggests that when communications are accidentally obtained, government officials are alerted. As usual, statements given by the government and the actual actions they take seem to very greatly depending on whom you ask. This news comes only weeks after the NSA came under scrutiny after whistleblower Edward Snowden, a former NSA contractor, revealed just how in-depth government spying efforts have become. The report in the New York Times does not offer any clues as to the point of all this data collection. According to officials, the data gathered by these email programs hasn’t directly prevented any terror plots.
The NSA claims that it only comes into contact with approximately 1.6% of all Internet traffic.
Although this figure is difficult to prove one way or the other, recent reports confirm that the NSA has actively been pressuring major ISPs to provide master keys to their encryption algorithms. If granted access to these keys, the NSA would be able to decrypt all web traffic including secure shopping sites and banking information. The fact is that the government is reaching ever further into the lives of private citizens. Whether you are communicating with family and friends overseas or conducting business in a global marketplace, those communications are no longer safe from prying eyes and government programs that work behind the veil of legality in a post-9/11 world.
A Zero Day Exploit Used for Good?
18.08.13
Recently, a zero day vulnerability in Firefox 17 was released that has actually been used by United States law enforcement to track some Internet criminals. Although Firefox is currently on version 22, the Tor Browser is powered by Firefox 17. This could become a concern for criminals who rely on the Tor Browser for anonymity while committing various online activities. The Tor Browser protects users by bouncing Internet requests across a large network of relays run by volunteers around the world. Some of the benefits include preventing anyone from learning what sites you visit, preventing visited sites from accessing your physical location, and allowing users to access sites typically blocked by Internet censors. Some of the sites commonly visited using the Tor Browser include the Silk Road and thousands of sites that sell child pornography.
The Silk Road is only available by using the Tor Browser and has often been referred to as the “eBay of hard drugs” because drug dealers around the world can sell their wares without fear of prosecution.
The vulnerability in Firefox 17 allows law enforcement to discover the true Internet addresses (and physical locations) of people who are browsing child pornography sites or participating in other illicit Internet activities.
On August 3, 2013, US authorities were seeking to extradite Eric Eoin Marques. The 28-year-old has been called the “largest facilitator of child porn on the planet” by the FBI. His capture has resulted in the disappearance of a large number of hidden service addresses from the Tor Network. In this case, the exploit in Firefox 17 was only used to figure out the physical locations of Tor Browser users involved in child pornography trading via the Internet. However, the exploit could also be used to download and run malicious code on the user’s computer.

Security experts believe that this attack is being operated by a law enforcement agency due to the lack of malware being injected onto a user’s machine. Typically, an exploit like this would be open season for hackers looking to profit using the Citadel banking Trojan or similar malware. Although no agency has taken credit for masterminding the exploit, research has traced the IP address used by the malicious script’s controllers back to a Verizon address space that is managed by Science Applications International Corp.; an American defense contractor headquartered in Virginia. An invasion of privacy is still an invasion of privacy no matter how you slice it, but at least in this case it is helping to capture criminals who have long since enjoyed the anonymity provided by the Tor Browser.
It is worth noting that the vulnerability being exploited by this attack was fixed in Firefox 22 and Firefox ESR 17.0.7.
In other words, people who are running the latest supported versions of Firefox are not at risk from this exploit. This event does go to show that even law enforcement agencies are beginning to adopt techniques commonly employed by hackers to track down criminals around the world.
Joomla Vulnerability Opens Door to Malware Injection
20.08.13
Joomla! is a content management system that has gained popularity as an open source platform for blogs and other information sites. Approximately 2 weeks ago, a critical software update was released patching a vulnerability in the CMS. The exploit could allow hackers to inject malicious content into websites and turn it into a phishing or malware trap for legitimate visitors. Originally created in 2005, Joomla! is a free CMS for publishing web content. It is built on a model – view – controller web application framework that can also be used independently.
Written in PHP, Joomla! relies on object-oriented programming techniques and software design patterns. It stores data in a MySQL database and includes features that include page caching, RSS feeds, news flashes, and support for multiple languages. The patch applies to Joomla! 2.5.13 and earlier 2.5.x versions. The bug was originally discovered by a web security firm, Versafe, which has confirmed that a simple exploit targeting the vulnerability is already being used. The bug allows users to upload PHP files to the site simply by adding a “.” to the end of the PHP file name. On older, no longer supported versions of Joomla! such as 1.5.x, users do not even need an account on the Joomla! server for this hack to work.
Security experts have seen a significant increase in the use of compromised Joomla! pages as launch pads for drive-by download attacks.
Specifically, banking Trojans, such as the Citadel Trojan, have been disseminated using this technique. This automates the infection process for criminals and makes widespread botnets appear much more rapidly. The increased popularity of blogs has made these types of attacks especially dangerous. Earlier this year, a web security firm reported that it had tracked more than 90,000 websites powered by WordPress (another CMS) that had been injected with malicious code.

More recently, a website botnet named “Fort Disco” is being tracked. This botnet is made up entirely of hacked Joomla! and WordPress sites. The sheer number of CMS-based content pages makes widespread infection extremely likely. When you take into account the fact that many blog owners operating Joomla! and WordPress sites are security illiterate, it makes exploiting these sites especially easy. Joomla! does have security plug-ins that help to strengthen the built-in security features of the PHP-based system, but these have to be installed separately from the main installation and configured properly. This is not always done correctly, especially when sites are created by amateur designers. If you currently use Joomla! as a web platform, make sure it is updated to the latest version to avoid malware injection from this simple hack. Website owners currently operating unsupported versions of Joomla! should be especially careful as the security risks are even greater for these sites.
Consider updating to a supported version (2.5.x) to receive the security update.
From a user perspective, making sure your antivirus software is up-to-date may be the only way to protect yourself from potentially malicious downloads if you stumble upon infected site. Even this is not a guarantee as some malware, like the Citadel Trojan, are notoriously good at circumventing antivirus detection software.
Email Collection Tools on Craigslist
21.08.13
Email harvesting is something that has been done by spammers for years. By collecting fresh sources of valid email addresses, spammers always have a constant supply of potential targets for ad campaigns or more malicious purposes such as phishing scams. In 2009, there was a rash of email harvesting on Twitter. These email addresses were pulled in real time and used for a variety of spam related purposes. Although Twitter has made changes and users have been warned of the dangers, these tools are still in use today. Craigslist has taken off in recent years as the “go to” place for purchasing a variety of new and used items. Bartering has also become extremely popular on the site and stories such as “One Red Paperclip” highlight how powerful the bartering trade can be on craigslist.
Attracted by the popularity of the website, spammers regularly harvest valid email addresses from the multi-national website.
To aid these criminals, DIY email collection tools are commercially available that make email harvesting extremely simple for anyone.
These tools offer a high level of customization and special feature sets that are tailor-made for craigslist email harvesting. Some of these features include the introduction of proxy support, outsourcing the captcha solving process, quality assurance (avoiding the collection of anonymous email addresses), and functions that allow users to tailor the process based on keywords or specific time periods. Often these email addresses are used for legal, albeit annoying, purposes. For instance, there are many forum discussions about the use of harvesting tools to obtain email addresses. Advocates swear by them as a marketing tool that can deliver targeted results.

Those against these harvesting practices consider email harvesting a “black hat” practice that should be avoided. Either way, these programs can be purchased for as little as $20 per license online and the obtained email addresses can be used for any purpose. Most reputable email providers are relatively good at blocking spam, but the real danger comes from phishing emails that could be related to these email harvesting tools. For example, a hacker could search for email addresses in the electronics section of craigslist only. This means that every email address obtained is from a person selling a TV, stereo, or other electronic device. Although not guaranteed, there is a good chance that this person recently purchased another electronic device to replace the one they are selling. Armed with this information, a hacker could easily send a phishing email “from” Best Buy or another electronics retailer hoping to draw potential victims into a phishing scheme that ultimately leads to malicious software downloads or hijacked information.
Craigslist offers an email anonymization feature that protects your email address from harvesting tools.
It is recommended to use these tools whenever posting something on craigslist to avoid having your email address compromised and possibly falling victim to a malicious email scam. Similarly, avoid putting your phone number into craigslist ads directly as some of these tools will also harvest phone numbers subjecting you to phone phishing scams or at the very least, annoying marketing calls.
DDoS – More Than Just an Inconvenience
25.08.13
Distributed Denial of Service attacks (DDoS) have been used for years to undermine services provided by large corporations including banks. Often, these attacks are designed to shut down or at least significantly slow down websites operated by targeted companies. It appears that these attacks have another use as hackers have begun to use “low powered” DDoS attacks to mask massive fraudulent wire transfers from moderate to large banks. Although the banks that have encountered this new wave of DDoS attacks have not been publicly named, major banks such as J.P. Morgan, Wells Fargo, Bank of America, Chase, Citigroup, and HSBC have all fallen victim to DDoS related assaults in recent months. Many of the attacks on the aforementioned banks were politically motivated and perpetrated by groups who had no interest in stealing money; rather, they simply wanted to disrupt normal operations for these financial conglomerates.
These new attacks use much weaker DDoS attacks to mask the takeover of the “payment switch” – a program that controls the wire transfer application. A privileged user account for the payment switch is used to control as much money from as many accounts as possible until stopped by bank security. This can be a much more profitable venture for criminals than standard techniques that involve phishing to get control of a single account and moving that money to bank accounts controlled by the hackers. The DDoS attack simply distracts security employees from the primary objective.
Although it is unclear how these criminals gained access to a privileged user account in the first place, banks have been instructed to slow down the money transfer system while undergoing a DDoS attack.
This allows security employees and automated security systems more time to catch the exploited user account and prevent wire transfers from being initiated. Recently, a major payment processing company in California went completely out of business unexpectedly after falling victim to a massive wire fraud attack that left them unable to repay millions of dollars in lost funds to customers.

On a large enough scale, this could happen to even large banks that may be unable to cover the expenses associated with repaying customers for lost funds. The three affected banks are only the latest victims of these DDoS distraction attacks. The Dell SecureWorks Counter Threat Unit issued a report in April warning of a DDoS toolkit known as Dirt Jumper that has been used to distract bank employees while fraudulent wire transfers are attempted. Once a wire transfer has been approved, it cannot be reversed. This is what makes fraudulent wire transfers especially dangerous and particularly costly to both consumers and banks alike.
Normally, a fraudulent transfer is spotted relatively quickly by employees and stopped immediately.
The DDoS element confuses employees and slows down the system enough to allow millions of dollars to funnel out of the bank without the immediate knowledge of bank employees or security personnel. The only way banks can successfully mitigate losses from these attacks is to increase security efforts to minimize damage caused by DDoS attacks and possibly even stop wire transfers during an attack altogether.
Another Craigslist Scam
29.08.13
The faltering economy has driven many people to look for alternative purchasing avenues. One of the most popular has become craigslist; an online marketplace that can be used for everything from bartering to selling old appliances and even finding new employment. As more people rely on craigslist on a daily basis, so have hackers who realize the potential money to be made by exploiting vulnerable users unaware of the many online dangers associated with craigslist and similar sites. Bartering on craigslist has become especially popular and is the avenue exploited in this dangerous attack. People are able to put up items that they no longer need in the hope of trading it for a different, useful item with other users. For the most part the system works exceptionally well, but criminals have discovered a new tactic that can trick even more adept users. In this case, a text message is sent as a reply to the craigslist ad offering to trade undisclosed items that can be viewed at a specific URL.
In this example, the URL used is hxxp://pixsend.org, although similar sites have also been found that work in the same fashion. When an unsuspecting user visits the website and attempts to view the pictures, they are prompted to download a version of GIMP (an open source image manipulation program similar to Photoshop) in order to view the pictures. The site claims the photos are in a .gmp file format. GIMP images are actually stored as .xcf files and should be a red flag for those experienced with the program. Everyone else will download GIMP along with a host of other unwanted programs including the notorious Citadel Trojan.
Citadel is designed to circumvent most antivirus software and run secretly in the background without most users realizing they have been infected.
When these users attempt to bank online or enter sensitive information into a web form, the Trojan records the keystrokes and sends them to the hacker at a remote location. Bank accounts, PayPal accounts, and credit accounts at major retailers can quickly be wiped out once a hacker has access to this information.

Needless to say, the pictures are not real and cannot be viewed. The hackers do add a nice touch by including bogus file names for other pictures such as “christmas-moms-dsc1022.JPG.gmp” which help add to the legitimacy of the Pixsend “file sharing” site. Although no drive-by downloads were detected at the Pixsend URL, this tactic could also be employed depending on the type of browser being used or operating system of the user’s machine. In any event, the Trojan is mixed in with approximately 100 other malicious files that range from annoying browser toolbars to other programs with unclear purposes.
As a final note about this threat, it is not limited to programs that scrape data from craigslist.
In many cases, a person actually combs through listings and manually contacts individuals. This has been proven by craigslist posters who randomize their phone number as a series of digits and words. These people have received text messages in addition to those who input their phone number in a format that is easily scraped using a variety of automated tools. There is nothing wrong with using craigslist as a tool to reach others in your community; just make sure to protect your information and your computer by being especially vigilant and not following any links given to you by a prospective buyer.

▼ Show Discussion