Zeus Isn’t Dead, New Version Evades All Antivirus Detection Tools
The venerable Zeus banking Trojan has been killed off many times; disappearing from the global Internet time and time again only to reappear with new modifications designed to improve the powerful malware’s features while avoiding modern detection software. Zeus has been used by cybercriminals around the world to orchestrate massive malware campaigns that have been responsible for millions of dollars in stolen funds over the last several years.
The largest of these campaigns was known as the Gameover Zeus botnet and it was taken down as part of a Global Task Force led by the FBI approximately one year ago. Aside from a few variants that have been spotted and quickly disappeared, the Zeus banking Trojan hasn’t been much of a threat to PC users in recent months. That is, of course, until researchers from PricewaterhouseCoopers recently discovered a new version of this dangerous Trojan that cannot be detected by any modern antivirus security measures. This discovery could signal the start of an entirely new Zeus malware campaign that could rival – or even exceed – the financial losses associated with the original Zeus botnet.
For those readers who are unfamiliar with the Zeus banking Trojan, it is a form of malware that is primarily used by hackers to steal banking information by using a combination of form grabbing and man-in-the-browser keystroke logging tactics. First discovered in 2007 when it was used to steal data from the US Department of Transportation, it only began to catch the attention of Internet security experts in 2009 when it was learned that Zeus had already infected over 75,000 FTP accounts used by large companies including Bank of America, Oracle, Amazon, and NASA.
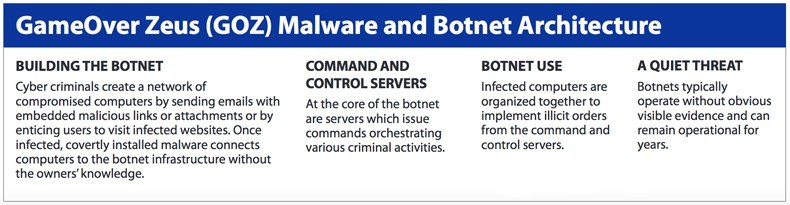
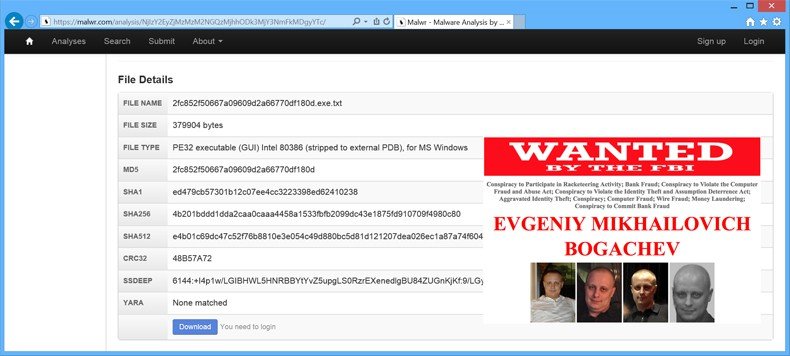
Zeus became even more notorious in late 2011 when the Gameover Zeus botnet first began intercepting online banking transactions. At one point, it was estimated that over 4 million PCs were infected with Gameover just in the United States. Around the same time, the botnet was also used to distribute the Cryptolocker, one of the most dangerous ransomware variants ever released. Some security experts believe that even though the Gameover Zeus botnet was dismantled last year, many PCs may still be infected with the malware even as of this writing – waiting for a new infrastructure to be put in place that can once again control these infected PCs. Some even believe that the person behind Gameover (Evgeniy Mikhailovich Bogachev) is already building a replacement infrastructure capable of controlling all the machines already infected. There’s even some speculation that the newly discovered version of Zeus is Bogachev’s attempt to get the botnet going again using new tactics learned from the takedown of the original botnet. At this time, Bogachev is still at large and the FBI is offering a $3 million bounty for his capture. He is believed to be hiding out somewhere in Russia.
In any event, Zeus hasn’t been used by hackers for any major malware campaigns since last year (although a variant of Zeus known as Citadel has also been used with success by hackers primarily located in Russia). While various iterations of Zeus have relied on different exploits for distribution, the latest version of Zeus uses a new set of techniques based on the Neutrino exploit kit. This exploit kit is a specialized web-based attack tool that targets unpatched vulnerabilities in the Flash player plugin used in all modern Web browsers. Detected as JAVA_EXPLOIT.NEU, Neutrino takes advantage of multiple Flash vulnerabilities and can be purchased or even rented from the hackers responsible for creating the exploit kit.
As previously mentioned, what makes this version of Zeus so concerning is that it cannot be detected using modern antivirus detection tools. When Stephen Ramage (the researcher from PricewaterhouseCooper who first discovered the new variation) ran a sample of suspicious code through the Malwr.com analysis platform, mutations resembling the Zeus banking Trojan were discovered. Unfortunately, when Ramage uploaded the same sample to VirusTotal (a well-known and powerful malware analysis tool used by security researchers), none of the antivirus products used by the program analysis program were able to detect the malicious code as a threat. In other words, this new threat cannot be detected even if antivirus software is updated regularly (at least not until researchers learn more about this dangerous malware variant). Another problem is the fact that the domains used by Neutrino were just registered one week ago meaning that this campaign is just getting started. It’s possible that hundreds of thousands of PCs could already be infected with this new and dangerous banking Trojan.
The only way to protect your PC from this threat is to ensure that all Web browser plugins are disabled if not needed and updated regularly if those plugins are necessary for day-to-day use. Ensuring that automatic updating is turned on for Adobe Flash player is especially important as this is the primary means by which the Neutrino exploit kit drops its malicious payload. As always, ensure that the OS and all third-party applications are regularly updated. Once more information is available about exactly how this threat avoids detection, antivirus signature updates should be able to detect this new version before it can cause any damage.
It’s also worth noting that although the Neutrino exploit kit relies on drive-by download techniques to infect PCs with Zeus, other distribution methods can also be used by the hackers behind this campaign. For this reason, always make sure to only visit websites you trust and never open any emails from unsolicited and/or unknown sources (especially those with attachments). Until more is known about this new and highly dangerous threat, remain vigilant while using the Internet to avoid possible infection by this stealthy form of malware.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion