Hackers Steal NSA Exploit Kit and Put it up for Auction
In what is a truly embarrassing event for America’s signal intelligence service, hackers got their hands on a massive set of hacking tools belonging to of the NSA. The hacking group, called the Shadow Brokers, put part of this online for free to show that it was genuine. Now they are selling the rest.
These files are the kind of industrial-strength hacking tools that espionage firms would have sold to the NSA, those that the NSA bought on the black market, and those that the NSA might have developed themselves and with contractors.
Cisco Firewall Exposed
The set of tools include rather common tools for everything from sniffing TCP traffic to far more advanced tools that exploit zero-day defects. To recall, “zero-day defect” means software vulnerabilities that the software or hardware vendor does not yet know about. So they can be exploited by hackers.
ARS Technica said that the NSA software exploits holes in a Cisco firewall. Cisco said the weakness and exploit has been out there since 2013. After the news broke, Cisco rushed out a patch to its Adaptive Security Appliance. Fortinet also was exposed.

And there are many other exploits in the tool kit as well.
NSA Might have Broken the Law
The NSA might have been caught violating the law again. (Various books and news stories have detailed how the Bush administration violated the Patriot Act and then after-the-fact issued orders and legal opinions to give legal basis to what they did.)
But what we are talking about here are new laws. After the Edward Snowden situation, President Obama issued an executive order that said that government agencies could only hang onto zero-day exploits—meaning not inform the software or hardware vendor of their weakness—given specific situations. This might have been one of those cases that was permitted. Or it might have been prohibited.
The MIT Technology Review said, “They also suggest that the agency may have gone against White House policy on when it is reasonable to keep flaws secret.”
After the Snowden revelations, Microsoft and other tech companies were very angry that their own government had been stockpiling zero-day exploits. That is when President Obama issued his executive order, to regulate such behavior.
How Did Hackers Steal or Obtain the NSA Exploit Kit?
News reports do not say where the hackers obtained the hacked spyware toolkit. Some speculated that a system administrator might have exposed it by mistake. Obviously, given the theft of data by Edward Snowden, one might think there could be another person working on the inside. We might never know, as the NSA is certain to try to keep all of this secret. Of course the hackers know where the data came from. Maybe someday we will read about that.
After Edward Snowden took flight with his data, the NSA put in place many internal controls, like requiring two different people to login to access a computer. And they would have moved their data into isolated segments of their network and not put everything in one place to make it harder to steal all the best stuff from one place. They would too have taken away blanket access that system administrators with root access had, which is what Edward Snowden exploited.
If hackers had penetrated any of the NSA network they would have done what hackers usually do and send that data out using http, sftp, ftp, or https. But you would assume that the NSA would be carefully looking at what data was flowing out of its network. That data is encrypted and firewalls usually do not block outbound traffic. But you can assume that the NSA would be using the man-in-the-middle approach to read traffic going out. While that does not work across the wider internet, but it does work inside the firewall inside the same domain.
Physical theft is also possible. This is where a technician physically removes a disk drive. A failover disk array will keep working even when someone removes one disk. That’s why they call it failover. Given that the Russians have hacked the Democratic Party and Senator Clinton’s campaign there could have been someone brave enough and clever enough to have done that. Remember that the NSA has offices around the world.
Where can Researchers download these Files and Study Them?
The hackers put the stolen exploit kits on bittorrent. That by definition causes it to spread around the world. That would put it beyond the reach of the NSA, who would want to try to get it back.
That means anyone who wanted to study this material could use any of the torrent search tools and a bittorrent client to download that and read what is where.
But at the time we wrote this we could not find these files at any of the well-known torrent sites. We did find part of it on Github. See below. We also found it on Dropbox, but Dropbox said so many people were trying to download it that it was temporarily unavailable.
Hackers Taunt the NSA and Announce their Sale
An announcement of the sale of the exploit kit is on this site and others. (It might be taken down by the time you read this.) The announcement includes a press-release of sorts and link to sites where the torrent files can be found and instructions for unzipping the exploit kits.
Their press release reads:
!!! Attention government sponsors of cyber warfare and those who profit from it !!!!
“How much you pay for enemies cyber weapons? Not malware you find in networks. Both sides, RAT + LP, full state sponsor tool set? We find cyber weapons made by creators of stuxnet, duqu, flame. Kaspersky calls Equation Group. We follow Equation Group traffic. We find Equation Group source range. We hack Equation Group. We find many many Equation Group cyber weapons. You see pictures. We give you some Equation Group files free, you see. This is good proof no? You enjoy!!! You break many things. You find many intrusions. You write many words. But not all, we are auction the best files.:
The free hacker file is eqgrp-free-file.tar.xz.gpg. The sites reference another name too: EQGRP-Auction-Files.zip.
They publish this checksum, so that people who download it can prove that it has not been tampered with:
sha256sum = b5961eee7cb3eca209b92436ed7bdd74e025bf615b90c408829156d128c7a169
Then they give this command to decrypt the file, along with the password:
- gpg --decrypt --output eqgrp-free-file.tar.xz eqgrp-free-file.tar.xz.gpg
Password = theequationgroup
Of course they do not give away the password for the file they want to sell. It is:
- eqgrp_auction_file.tar.xz.asc
With checksum:
- sha256sum = af1dabd8eceec79409742cc9d9a20b9651058bbb8d2ce60a0edcfa568d91dbea
The press release too is broadcast by torrent. Here is the magnet, which is the file you put into bittorrent software to start the download:
- magnet:?xt=urn:btih:40a5f1514514fb67943f137f7fde0a7b5e991f76&tr=http://diftracker.i2p/announce.php
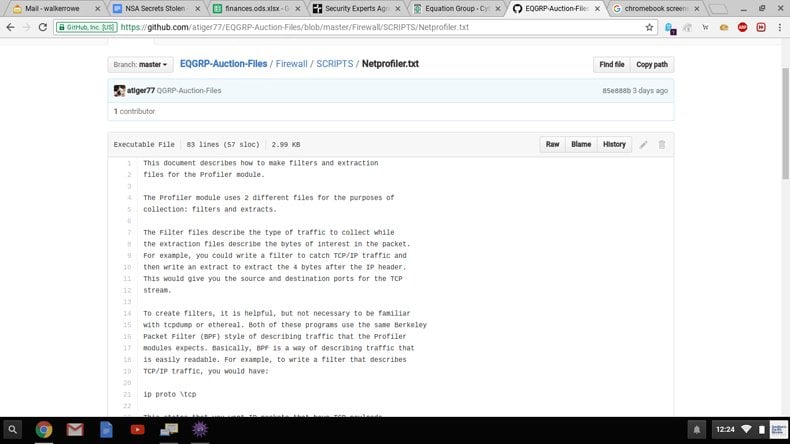
Below are some screen prints from different sites showing parts of the software and the directory file structure. One of these even came from Github here. We imagine the NSA will be contacting that company to ask them to remove that. Github is a platform where programming teams and open source projects keep their software.
And here is a screen print of part of one of the many scripts. It looks like a packet sniffer (used to read packets of data as they travel across a network). So it does not look like anything sophisticated.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion