Hacking Self Driving Cars
Recently the American government issued guidelines for driverless vehicles. This creates national standards so that car manufacturers do not have to figure out how to follow 50 different laws in 50 different states. Analysts have said these rules seek to make this market grow without imposing a heavy regulatory burden. Many of the details are left up to the manufacturers to design and implement.
Google has long been operating self-driving cars. Uber has self-driving taxis operating in Pittsburgh, Pennsylvania. And Tesla has self-driving electric cars. All of these let the driver take control when needed. Ford announced it is building Fusion Hybrid driverless vehicles that do not even have a steering wheel. So there will be no way that passengers can take control of the vehicle.
The fear is that a hacker can take control of a car and drive it into a wall.
In issuing their regulations, the Americans stressed the need to make these cars secure against hackers. That is probably not going to be 100% possible as hackers have shown they can hack whatever they want. But at least the car makers can put in safety measures that take control away from the hacker when they have managed to hack that. Obviously the safe thing to do if there is any perceived threat is to stop the car then have it radio the manufacturer for a security scan.

The problem is that while self driving cars are new, they are built with components that have been around a long time that are subject to hacking, like Wi-Fi and networks. These cars use radar, lasers, and cameras to track their location. Already a Tesla crashed and killed the driver when the camera could not distinguish between the sun and the white side of a truck. So could a hacker use a mirror and the sun to run a car off the road?
These are some of the problems that the startup find Karamba Security hopes to solve. TechCrunch reports that the Israeli security firm has raised $2.5 million in seed money to look for ways to improve self driving car security.
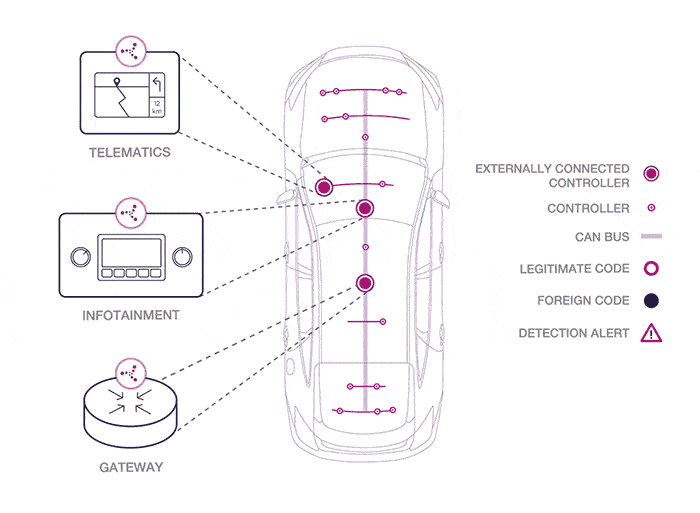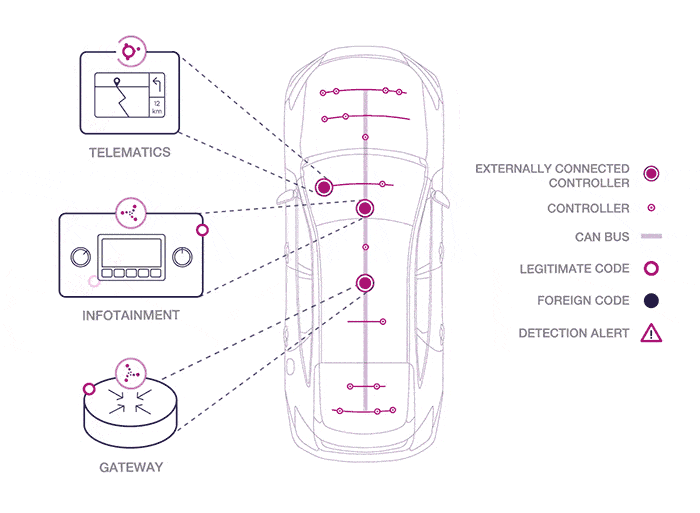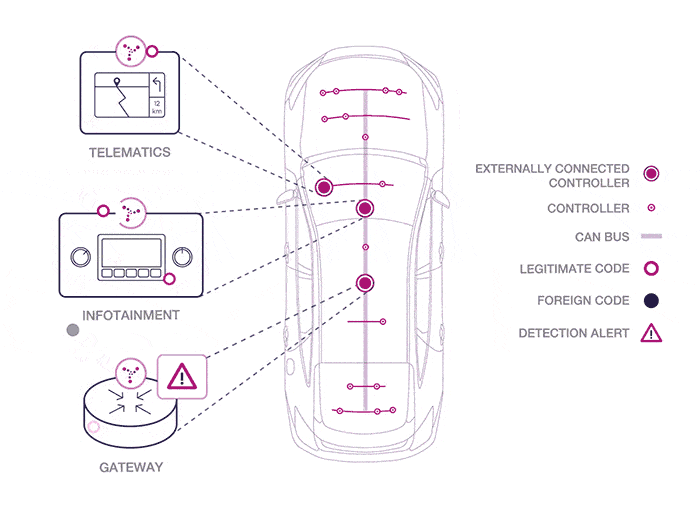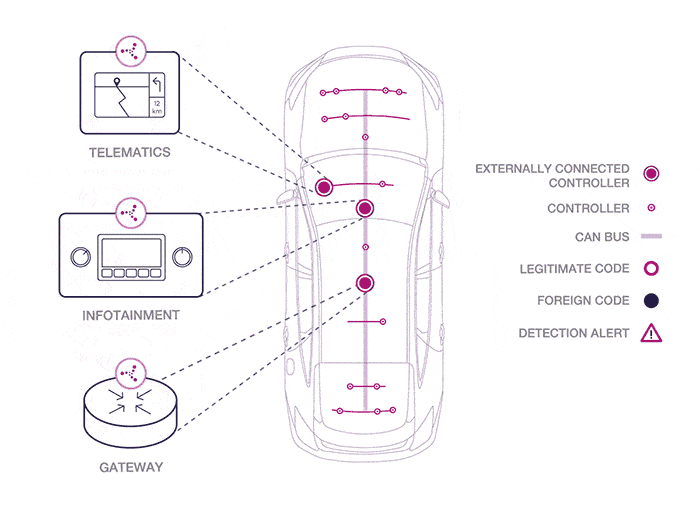
Graphic source Karamba Security.
As you can see from the graphic above, Karamba hopes to harden the weak spots in a car’s security, which are mainly network access points attached to the public internet and cellular networks, like the entertainment system, the system that sends and receives data from the manufacturer, plus systems that gather data on traffic and weather conditions.
The Karamba intrusion detection software would apply analytics and other techniques to detect and block malware. But a car is not a desktop computer. Their antivirus software cannot always do what antivirus software on a PC does, which is to block file access. Because the software could make the situation worse if they turn off a system needed to operate the vehicle safely.
More companies will turn their attention to this market as the fleet, and thus the risk, grows. Already Chinese researchers have shown that they can hack a Tesla model S from a distance of several kilometers. This let them take control of the vehicle’s brakes. Other hackers have gained access to the Tesla network, but this is the first time that hackers have shown they can take over a vehicle. The Chinese were also able to open the trunk, turn off the lights, and rotate the mirrors as the car was driving. Obviously all of this would present a great danger to the passengers and other drivers on the road and pedestrians.
And since the car is a physical object not locked in a data center, hackers can attack the car just by walking up to it and attaching some kind of device.
The vision of proponents of self-driving cars is they will bring lots of benefits to society. One would be to reduce the enormous number of deaths due to traffic accidents. The other would to reduce car ownership. After all, why should someone pay for an expensive car when they can call one from their iPhone? But security is an issue that has to be addressed so that some foreign government cannot run them off the road.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion