Pegasus Spyware Targets iOS
An activist in the Middle East in August of this year noticed odd text messages coming to his phone. It turns out that those were instructions coming from the command and control center for Pegasus Spyware telling the Spyware what actions to take.
The activist alerted Citizen Lab who contacted the Lookout security firm. What they found was spyware. Lookout wrote this technical analysis giving details of how the spyware works.
State-level Hackers for Hire
NSO Group is an Israeli firm that wrote Pegasus. It affects iOS up to version 9.3.5. Pegasus lets whoever is using it bypass iOS security and gain access to virtually all data on the phone including audio, video, contacts, GPS location, passwords, Wi-Fi router password, text messages, and messages and email from from Gmail, Facebook, Skype, WhatsApp, and other programs.
Pegasus is Spyware that NSO Groups sells to governments and anyone else who can pay $25,000 to deploy it to one victim’s phone. One organization bought 300 licenses for $8 million. It is not clear how someone found that out. Yet NGO has a LinkedIn page.
How to Detect and Get Rid of It
So far mobile device management and antivirus software cannot detect Pegasus.
One disables iOS updates. So to get rid of it you would need to wipe your phone. There is no indication that your phone is hacked except suspicious text messages that look like two-factor authentication codes coming from Google, Facebook, and others. Or you could connect your phone to a Mac and look for the different files listed in Appendix B of the Lookout report.
The average person is not going to know how to look for hidden system files. So if you can you should just erase your phone and assume you have been hacked. But at $25,000 per victim unless you are a celebrity, criminal, or activist you probably have not. Still you should erase your phone completely anyway every so often. That will both make it work faster and remove any hacks that are there.
Zero Day Exploits
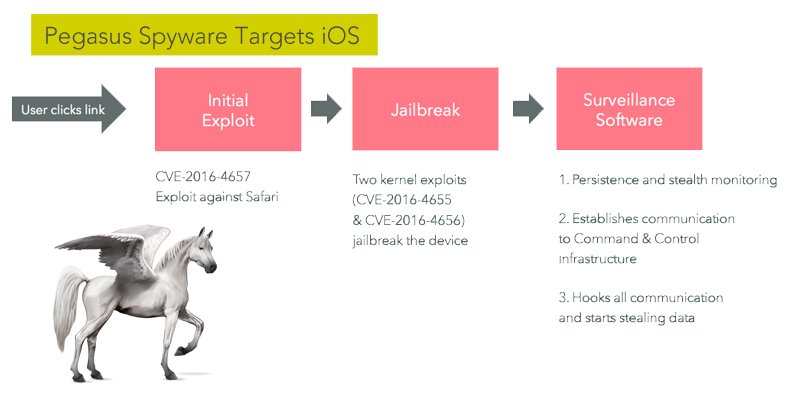
Pegasus exploits these zero-day vulnerabilities:
CVE-2016-4657: weakness in Safari that lets attacker execute code, meaning direct the iPhone to run the code the hacker wants.
CVE-2016-4655: lets hacker find the address of the kernel in memory. Operating systems put that in random places to defeat hackers. Hackers need to know where subroutines are located in memory so they can exploit them.
CVE-2016-4656: lets hackers jailbreak the device, meaning gain root access. Then they can turn off security features and install software.
How it Works
Lookout says that when a victim opens a URL it exploits a weakness in Safari. But while the Lookout analysis shows the software that the Spyware downloads later, they do not have a sample of what the HTML and JavaScript code on the poisoned webpage looks like. So we do not know how that part works.
Having exploited the browser, the Spyware then downloads a zipped file and does the following.
● Install a root TLS certificate. That would cause iOS to trust data encrypted by the hacker.
● Install JavaScript that runs at reboot that runs unsigned code to jailbreak the device. Normally iOS will not run code that is not signed, meaning verified by a third-party, meaning someone other than the hacker.
● Adds a subroutine that lets Pegasus inject code into a running process. So, for example, they can then run undetected in the memory occupied by WhatsApp or other program and operate from there. This part used code freely available on the internet called Cydia Mobile Substrate.
● Installed sniffers for Viber, WhatsApp, and other programs. A sniffer is software that listens to and records traffic.
● Install a process (daemon) to send files to the hackers Command and Control center.
● Mounts its own system partition, meaning boot up instructions, bypassing what Apple wrote.
● Turns off the phone’s Deep Sleep mechanism.
● Removes any other jailbreak software.
● Installs a self-destruct feature, to erase any traces of itself as needed.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion