Notorious Carbank Hackers Embed Visual Basic Code in RTF and Exploit Google Services
A group of hackers known as Carbank, who in 2015 stole an incredible $1 billion USD from banks, have been again using RTF documents with embedded OLE objects to plant malware on computers. They send these documents in emails using phishing attacks. Then they use Google services on the machine to plant further instructions.
OLE is an object (Object Linking and Embedding) in old Microsoft technology, still in use, that lets programmers create objects with relative ease, like push buttons, drop box lists, or to execute code that they wrote themselves in Visual Basic.
Visual Basic has been in Microsoft Windows and DOS since Bill Gates and some other people wrote that when Gates was in Harvard. Visual Basic is one of the easiest languages to code. But it is dangerous, since it can access low level functions, like copying files.
VB in a spreadsheet is similar to a Macro, except VB is a full programming language. Macros just do simple steps. For example, with OLE, users of any Microsoft Office product can put buttons on screens in Microsoft Excel or Microsoft Access and then they can write their own VB code and attach it to those buttons or kick it off automatically when those docs are loaded.
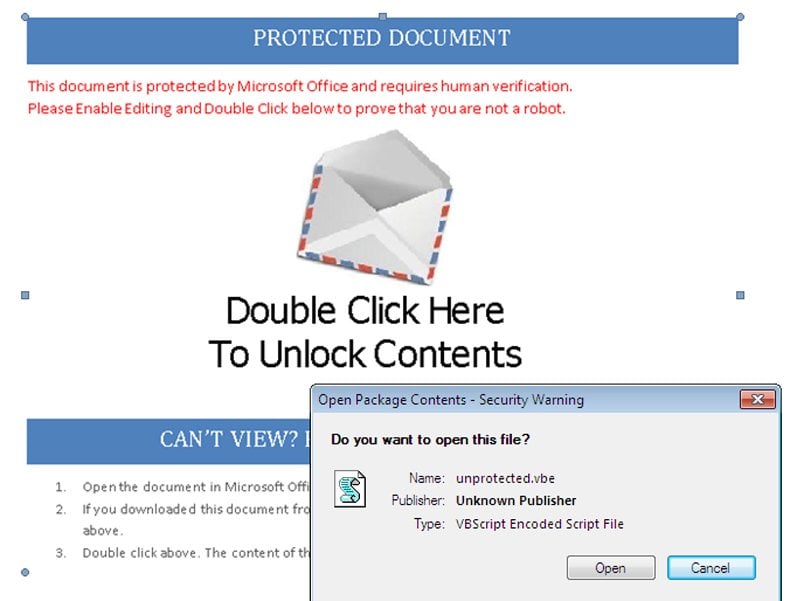
The RTF (rich text format) document format lets a user embed objects in the file. That is unfortunate. When the user opens the file the computer extracts the object from the RTF and executes it using the default handler for the file type. In this case the embedded object is a VBE, Visual Basic executable.
This issue can be blocked by adequate security training. When you run Visual Basic code on a computer, the computer throws up a warning. But people do not pay attention to the warning.
The warning is that the computer wants to execute the file unprotected.vbe. The warning screen is shown below.
Graphic Source The Hacker News
Then the malware takes over. It obfuscates its activities by connecting to Google Services. These include Google Sheets, Google Forms, and Google Apps Script. Once it attaches to those it can execute further commands on the victim's computer, because Google Sheets and Forms supports scripting just as Microsoft Office does. The scripting language is JavaScript. These scripts also have access to low-level functions on the computer as well as the ability to program unlimited logic in the spreadsheet and forms.
A call to Google Apps Script creates a Google Form and Google Sheet using the user’s stolen Google userid. So these do not raise the suspicion of any kind of anti-virus or anti-malware check, since those apps are whitelisted by Windows and Google and the user’s Google id is trusted by Google.
This Forcepoint article that describes this exploit does not explain how the VB script attaches to the Google Forms or Sheets function or executes Google Scripts. Those functions are only available in the browser, so the VB script must request to open a URL and then the default browser launches.
Links at the bottom of the Forcepoint article show the links to the command and control center in case you want to block those or search your web logs to see if any of your employee’s have been victims. Fortinet has contacted Google about the issue.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion