Undetected Malware Targeting North Korea
Last week Cisco’s research arm Talos confirmed that it had detected a Remote Access Trojan (RAT), which they have termed KONNI, that has attacked organizations associated with the Hermit Kingdom. It has also been confirmed that by Talos that the earliest of these attacks using the above-mentioned malware occurred as early as 2014. Meaning it has evaded detection for nearly three years. The most recent attacks which started towards the end of April this year targeted UNICEF, the UN, and other embassies linked to North Korea.
The malware has evolved since the first of an estimated four campaigns. It has evolved from merely stealing information without any form of remote administration to the most recent iteration which uses two binaries which include a dynamic library. Thus the new version, boasting much better code than the previous version, can search for files generated by earlier versions on compromised machines. This means that it is safe to assume the creators of the earlier versions are deploying newer versions against similar, if not the same, targets as the previous ones. In this attack, KONNI was designed to be executed only one and could steal information from the infected machine including keystrokes, clipboard content, screenshot capture, executing arbitrary code, and data from installed web browsers.
KONNI Evolved
Previous versions of the attack have utilized phishing emails to lure victims which would contain an attachment that would consist of a decoy image or file that when opened would execute the malware. The first of these possible attacks used an image of a temple in Myanmar which was combined with a fake svchost.exe which once installed contained had two domains which it used to receive orders.
The 2016 campaign also utilized a phishing email with a decoy .scr file entitled “HOW CAN NORTH KOREAN HYDROGEN BOMB WIPE OUT MANHATTAN.SCR” which contained two documents, one in English the other in Russian. This version was changed by the author to now have two binaries, conhote.dll, and winnit.exe but only a single domain dowhelsitjs[.]netau[.]net for orders. The architecture of this attack could have been detected in 2015 leaving some experts to conclude that there was potentially four attacks targeting North Korean interests.
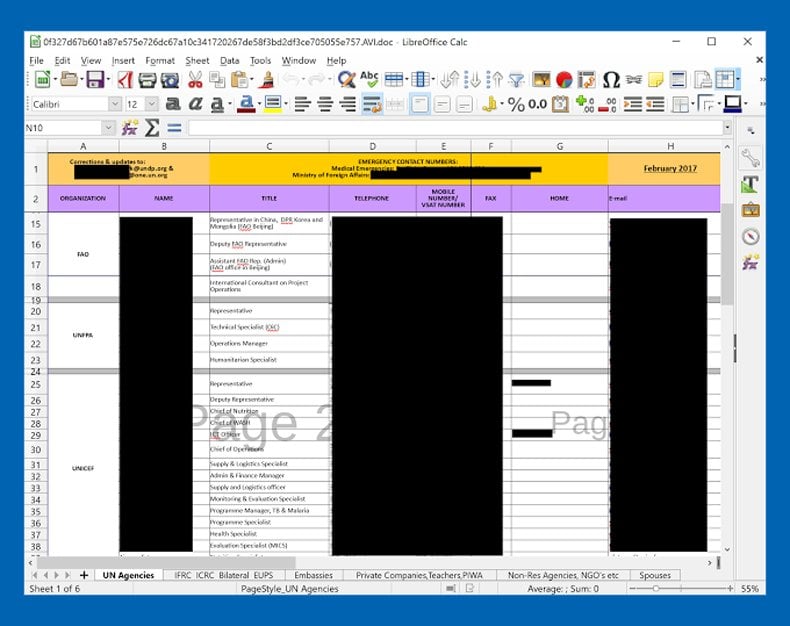
The latest campaign yet again utilized phishing emails this time titled, “Pyongyang Directory Group email April 2017 RC_Office_Coordination_Associate.scr”. The document appears to contain email addresses, phone numbers, and other contacts of members of official organizations in the UN, UNICEF, and North Korean-linked Embassies. In this version, both an executable and a library are dropped with the core code of the malware been found in the library, unlike the previous versions. The latest version can perform more instructions than the previous ones including file deletion and the ability to execute commands. It also appears that the author has created a 64-bit version as well.
From comparing the above-mentioned code and the intended targets it is safe to assume that the author has a discernible interest in North Korea. The code itself has become more sophisticated as well as the use of decoy documents been of a higher quality. It appears the latest campaign is still active and the overall aims of the campaign are anyone’s guess currently. As to whether the author is acting independently or with state sponsorship is also a guess. Talos has been unwilling to assume the nature of the author. Why then did it take nearly three years to detect when experts agree the code is not particularly advanced?
Targeted Attacks
Part of the reason that this particular instance of malware has been so hard to detect is that it has been an extremely focused attack, attacking only organizations with links to North Korea. It follows logically that any attack intended to affect as many devices as possible will be easier to detect as it casts its web far larger. Although KONNI is evolving to essentially be able to do more it still seems to be primarily used to steal information. The information has been stolen does not seem intended to be used for any immediately discernible financial gain. This means that the RAT was designed to intentionally fly under the radar in order for it to gain information over a period of time and in the case of KONNI to be used multiple times. Basic statistics will say the more focused the attack, or put differently the fewer amount of targets intended, the harder detection will be.
Prevention better than Cure
While the above attack is directed at international and state organizations far removed from daily life cyber espionage is a global problem needing to be addressed by an informed public. Whether it is in the form of corporate espionage or unwarranted invasions of your privacy certain steps can be taken to prevent similar attacks.
As the above example is dependent on the user opening an email for execution private individuals and company workforces can be taught how to better detect suspicious emails. That malware authors are still heavily reliant on phishing as a means of infecting devices means that the public at large is not sufficiently educated as to the potential threats or how to detect them. Going hand in hand with education is understanding either your own threat landscape or the organization you form part of. While different types of malware are intended for different purposes understanding what information cyber-criminals and cyber-spies could be after is vitally important. In your personal capacity passwords, banking details, and other account information is what would need to be protected. In an organization that deals with sensitive government contracts, for example, the details of those contracts could be wanted for corporate espionage or even state-sponsored espionage.
While the rise of KONNI as an effective piece of malware was eventually detected many lessons can be learned by private individuals and organizations in how sensitive information is stolen. Once you are aware how it can be stolen measures can be taken to prevent its theft.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion