Fileless Ransomware Emerges
Researchers and analysts at Trend Labs have discovered a new fileless ransomware which they have termed Sorebrect. Although fileless ransomware is by no means new, this latest variant displays some cunning features intended for it to evade detection and frustrate forensic audits. The variant was first discovered infecting systems in Lebanon and Kuwait, however, it has recently been seen infecting systems as far afield as Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S. Sorebrect seems to be specifically targeting companies within the manufacturing, technology, and telecommunications industries. Experts further believe that this new variant will in all likelihood appear in more countries or even peddled as a Ransomware as a Service (RaaS) on the Dark Web to serve criminal organizations in extorting money from victims.
Put simply Sorebrect utilizes code injection to inject malicious code into a legitimate system process, in this case, it utilizes the svchost.exe on the targeted system. Then it deletes itself in order to evade detection. It is clear, particularly when compared to recent ransomware attacks, that this can potentially signal an escalation in the cyber arms race security experts are struggling to contain.
Sorebrect’s Attack Chain
As was mentioned above Sorbrect abuses the legitimate svchost.exe. However, it first abuses the PsExec, a legitimate, Windows command-line utility that lets system administrators execute commands or run executable files on remote systems, in order to install Sorbrect. Thus allowing the malicious code to be installed remotely. This is similar to how SamSam and Petya abused legitimate processes to install malicious code. Then the malicious code is injected into the svchost.exe, after that it deletes itself, essentially making it fileless. Once this has occurred it then relies on the svchost, a Windows service hosting system process, to execute the payload by encrypting the relevant files.
Sorebrect ransomware appends ".pr0tect" extension to encrypted files:
The analysts who discovered Sorbrect wondered why the creators of the ransomware decided to use PsExec rather than use Remote Desktop Protocol (RDP) to install. It became apparent that in order to both inject code and become fileless the use of PsExec was simpler and far more effective. PsExec also came with another advantage in that it allowed attackers to remotely execute commands. In order to delete itself and the logs, making detection and forensic audits tough, Sorbrect utilizes wevtutil.exe and vssadmin respectively. Further, the ransomware uses a Tor network protocol in order to remain anonymous when communicating with its command-and-control server. Lastly, but in no mean least, Sorbrect can encrypt files shared via a local network, thus encrypting files used by other systems connected to a network. For large organizations infected with the ransomware, this could make important daily tasks nearly impossible to complete.
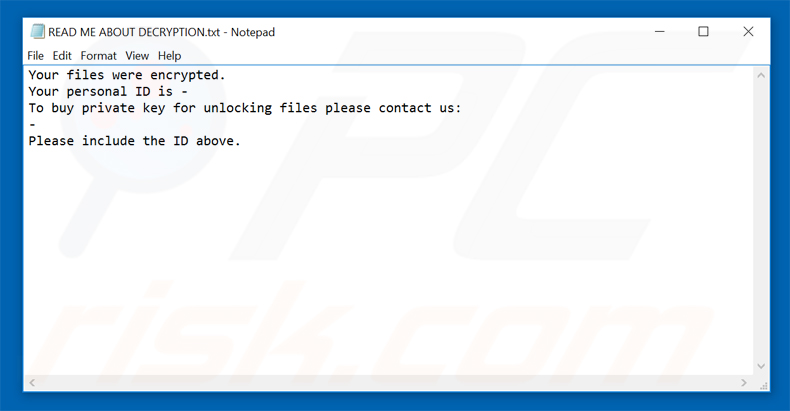
Sorebrect ransomware presents a ransom demanding message in “READ ME ABOUT DECRYPTION.txt” file:
Steps to prevent Sorebrect infection
While this ransomware variant does not employ a new attack vector in infecting machines, it is most certainly more advanced and cunning in how it intends first to inject malicious code, then delete itself and logs to evade detection. Although it uses methods previously used by other malware it is by no means less dangerous as it employs those tried and tested measures far more effectively and the threat posed should not be taken lightly.
The analysts at Trend Labs have advised the following best practices should be adopted in order to prevent system infection from this fileless type of ransomware:
- Restrict user write permissions. A significant factor that exposes network shares to ransomware is the tendency to give users full permissions. Limiting them will prevent ransomware from carrying out its file-encrypting routines across the network. Reviewing the permissions for each user in the Domain is a good starting point. This entails assessing each user account/group within the Active Directory and only providing the necessary privilege levels. Configuring the security of shared files and folders on a network is also recommended (don’t set up folders that anyone can easily access, for instance).
- Limit privilege for PsExec. PsExec is commonly used in enterprise networks, providing system administrators flexibility with how they interact with remote machines. As pointed out by its creator, however, in cybercriminals’ hands it can provide a way to interface and laterally move within remote systems using compromised credentials. This would ultimately enable them to install and propagate threats such as ransomware. Limiting and securing the use of tools and services such as PsExec and providing permission to run them only to administrator accounts that really need it help mitigate threats that misuse PsExec.
- Back up files. Cybercriminals use the potential loss of important and personal data as a fear-mongering tactic to coerce victims into paying the ransom. Organizations and end users can back up files to remove their leverage: keep at least three copies, with two stored in different devices, and another to an offsite or safe location.
- Keep the system and network updated. Ensuring that the operating system, software, and other applications are current with the latest patches deters threats from using security gaps as their doorways into the systems or networks. This has been exemplified by malware such as WannaCry, UIWIX, and Adylkuzz that exploited a vulnerability. Employing virtual patching in the absence of patches can also be considered.
- Foster a cybersecurity-aware workforce. User education and awareness helps improve everyone’s security posture. Like other malware, ransomware’s points of entry is typically through email and malicious downloads or domains. Organizations should conduct regular training to ensure that employees have a solid understanding of company security policy, procedure, and best practices.
- Deploy multilayered security mechanisms. As ransomware matures in the threat landscape, we can only expect it to diversify in terms of attack methods and targets. There is no silver bullet for ransomware, which is why enterprises need a defense-in-depth approach to security where proactive security mechanisms are arrayed. Data categorization and network segmentation help mitigate damage in case of exposure. While advanced sandboxing provides a way to quarantine and analyze unknown or dubious files, application control and behavior monitoring prevent suspicious files from executing and block unwanted modifications to the system. (Trend Micro 2017)
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion