Posteo Attempts to Combat Petya
German email service provider, Posteo, has attempted to combat the new version of Petya by blocking the email accounts used by the hackers utilizing their service in order to extort Bitcoin from victims. By blocking the email accounts of the hackers, they cannot access their mail or send mail. Thus, this would leave victims who to paid the ransom unable to receive the encryption code. This has left many to criticize the move by the company to block emails and thus render victims without the option to pay for their files to be decrypted. In an email sent to journalists at Motherboard, Posteo defended their position and believe that preventing misuse of their platform to be vital for the company and legitimate users of their platform. Posteo went further to say that there was no guarantee that if the ransom is paid the victim's files would be decrypted.
While much of the criticism surrounds whether this is an effective way to prevent infection, little of the criticism leveled against the company takes recognition of the companies right to block accounts it deems are misusing its platform. Granted, by blocking the hackers accounts the spread of the ransomware is not minimized. However, the PR storm that could result from a legitimate company knowingly allowing illegitimate actions to occur on their platform could cost the company dearly. At the time when Motherboard reported on the matter, it was estimated that approximately 20 victims had paid the ransom totally an estimated 5,500 USD.
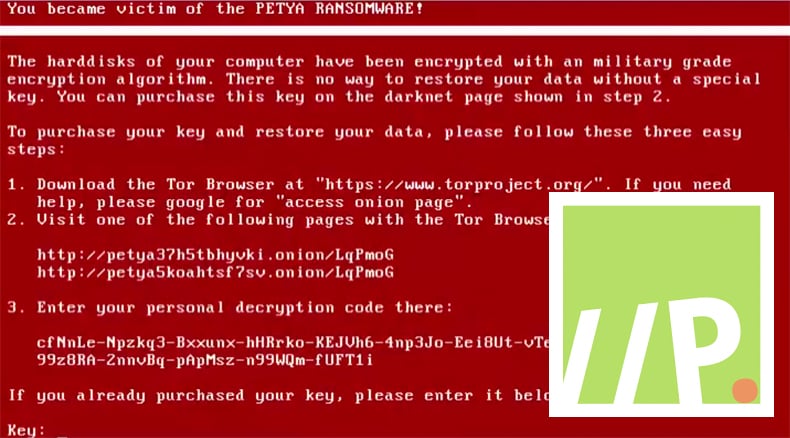
Petya or NotPetya or GoldenEye
The ransomware dubbed Petya emerged as early as 2016, although its latest iteration and attack campaign is the most devastating to date. The campaign which began or at least was detected on the 27 June has been estimated to have infected over 2,000 systems with the majority of those affected residing in the Ukraine and Russia. Some reports have stated over 300,000 computers have been affected. It was an incredibly targeted attack, compared to WannaCry, and compromised the operations of large multinationals including Danish shipping giant Maersk and US pharmaceutical company Merck as well as numerous ATMs across the Ukraine. Its similarities to WannaCry rest on that they both employed the leaked NSA exploit EternalBlue. Other than them both being ransomware and using the same exploit that is where the similarities end. Petya can be seen as a definite improvement on recent ransomware attacks. The hackers have learned from WannaCry’s mistakes.
Bogdan Botezatu, a researcher at the security firm Bitdefender has stated that “The quality of the code improves from iteration to iteration - this GoldenEye ransomware is pretty solid,” Where WannaCry had a killswitch which resulted from fairly amateurish coding, Petya or GoldenEye does not have the same failing. While WannaCry depended solely on EternalBlue in order to spread at the rate it did, Petya was spread also through Ukrainian software and Microsoft Word documents laced with malicious macros.
Administrators in a panic
One of the features which have administrators in a panic is how easily Petya can promulgate in systems with little or no controls on administrator privileges. Once infected Petya steals administrator credentials and utilizes powerful system management tools like Windows PsExec and Windows Management Instrumentation. Exploiting these tools it can instruct other computers connected via the network to install the malware.
Paying still the Achilles heal
Another key difference between Petya and WannaCry is the approach employed by the hackers. WannaCry spread like wildfire and those who released it was ill-equipped to deal with receiving payments. Those who released the most recent Petya campaign did not have the same problem. While Petya did not have the same problem regarding controlling the receiving of payment, it did, however, have another one. That’s despite Posteo blocking the relevant email address.
Petya relied on victims emailing a manual proof of payment in order to receive the decryption code. While it would make payments harder to track it would also reduce the victim's trust as to whether they will receive the code or not once the ransom is paid. Now that Posteo has blocked the account this weakness is rendered irrelevant.
No easy solution
As Petya has no killswitch and uses a variety of attack vectors there is no one solution solves all possibility. That been said more systems will be infected in future and more variants of Petya will come out of this to infect more systems. Unlike with WannaCry that could essentially be nullified by installing a patch due to Petya using multiple attack vectors patching would only solve the EternalBlue exploit and the vulnerability in the Ukranian accounting software. However, there is one more thing that can be done by administrators to prevent infections and that is by blocking the file C:\Windows\perfc.dat from running and using Microsoft’s Local Administrator Password Solution to protect credentials that grant network privileges. Again, like almost always, it is further advised to have important backups done.
One can argue that Posteo was wrong to block the email account used by the hackers as it does not stop the spread of the malware. Some would also argue that it denies the victim the right to choose whether to pay or not. This can be viewed as a silver lining in the sense that victims now cannot pay, thus no longer have to worry about the consequences of their actions and whether the ransom they have paid will go to fund another campaign they might be the victim of. Regardless of the moral questions surrounding Posteo’s actions, which in time will be seen as irrelevant, the reality remains that ransomware attacks are on the rise. Not only are they on the rise they are becoming the favorite extortion method used by hackers. Not only are they on the rise but they are becoming increasingly complex and despite the various warnings issued by experts organizations to not seem to take these attacks seriously until affected.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion