Equifax Suffers Gigantic Data Breach
When news of hacks, data breaches, and malware attacks break on mainstream media one knows that the seriousness of the situation can be rarely questioned. When it happens to a company responsible for generating a large portion of credit scores for the American public and advertises the latest advances in ID theft protection those with a sense of humor might comment how ironic the situation is, those who may have their identities were stolen as a result probably won’t be laughing.
News broke on September 7 when Equifax announced that it had suffered a major data breach. Essentially 143 million Americans, including a few British and Canadian citizens, had their incredibly sensitive personal information exposed and potentially stolen. Information which was jeopardized included consumers' names, Social Security numbers, and birth dates for 143 million Americans, and in some instances, driving license numbers and credit card numbers for about 209,000 citizens.
Equifax’s Response
To add insult to further injury the breach was discovered on July 29 of this year, no reason has been provided as to why the delay in announcing the breach took place. When it can be safely assumed that information stolen was been peddled on the Dark Web shortly after the attack took place which probably occurred either mid-May or June, any further delays in announcing the breach so that consumers can take action to protect themselves is intolerable. One reason for the possible delay was reported via Bloomberg shortly after the news broke that three senior executives sold off approximately $2 million dollars’ worth of stocks at the start of August.
Regulatory filings show that Chief Financial Officer John Gamble sold shares worth $946,374 and Joseph Loughran, president of U.S. information solutions, exercised options to dispose of stock worth $584,099. The filings also show that on August 2 Rodolfo Ploder, president of workforce solutions, sold $250,458 of stock. Ines Gutzmer, a spokeswoman for the Atlanta-based company, said in an emailed statement that the three “sold a small percentage of their Equifax shares,” and they “had no knowledge that an intrusion had occurred at the time.” Even though the company was aware of the breach a few days before and none of the filings lists the transactions as being part of 10b5-1 scheduled trading plans.
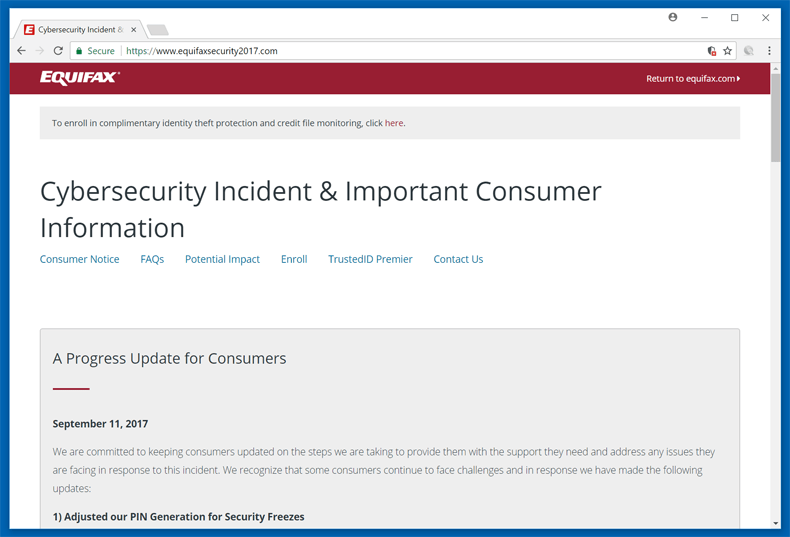
The company has taken some measures in an attempt to alleviate consumers’ woes. Shortly after the announcement, the company advised consumers to go to equifaxsecurity2017.com to check if their information has been stolen. Consumers will need to provide the last 6 digits of their SSN and last name. If you were expecting a black and white answer as to whether your information was jeopardized you may be sorely disappointed. The website does not give a clear indication if your data was affected, it does, however, make it clear if you were not affected. The situation is terribly confusing and consumers can be forgiven for demanding more from a company that is required to keep their personal information safe.
That sadly is not the end of the debacle in that Equifax is offering consumers affected by the breach free credit monitoring and identity theft protection. So, if you figured out you may or may not have been affected but you certainly know for sure that you were not affected, you can get a free service from the company entrusted to protect your data in the first place. At this point, there is a lot of head scratching taking place.
Advice to those affected
Given how hard it is to determine whether or not you were affected in the breach even if you suspect that you may have been affected there are a few things you can do to help prevent identity theft. You can place a credit freeze on your account. This will make it very hard for someone to take out credit in your name using stolen details. This may result in extra costs to not only place the freeze but also remove it. If you are determined to be at a high risk of identity theft this course of action is highly recommended. If you are a low risk of credit theft this option can be a hassle not worth the cost and effort. Another step is if you see any activity you don’t recognize you can visit www.identitytheft.gov and follow the steps to report the potential identity theft and get the account removed from the credit report. It is further advised to consumers to submit their taxes earlier in an attempt at preventing your tax information from been abused by hackers filing a fraudulent tax return.
How the hack was done
Equifax has employed FireEye’s security firm Mandiant to help the company determine exactly what happened. It was initially believed that unknown hackers exploited a security vulnerability on its website to gain unauthorized access to certain files. Quartz reported that the vulnerability exploited by the hackers was found in open source server software Struts, which is a popular programming framework for building web applications in Java. Security researchers had detected two vulnerabilities within the software which could date back to 2008. In the report which was published earlier last week the bug is easily exploited using the REST plugin. The plugin is used specifically to handle web requests. The vulnerability is found in how Struts parses the data and converts it into information interpreted in Java. When exploited malicious code can be hidden and executed once Struts converts it.
What may cause further worry to an already troubling situation is that 65% of Fortune 100 companies utilize the software in some manner. Organisations like Lockheed Martin, the Internal Revenue Service, Citigroup, Vodafone, Virgin Atlantic, Reader’s Digest, Office Depot, and SHOWTIME have developed applications that utilize the framework.
The response of Equifax in the wake the massive data breach will possibly be taught in schools as what not to do in the event of a data breach. One can only hope that changes to security policies and best practices are taken more seriously by large organizations who have a duty to do their utmost in protecting sensitive data.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion