Crunchyroll.com Hijacked
Popular websites have always been a target for hackers trying to spread malware. The popular website Crunchyroll.com, which allows users to stream their favorite anime shows, experienced an attack over the weekend which forced the company to close its website over the weekend. While there is still speculation as to the nature of the attack, the attack still serves as a reminder to any company with a website that it is a target.
On November 4, it appeared that visitors to the popular website were asked to download a desktop version of their software. This software was not as it seemed as it also included malware that was installed along with it. Crunchyroll staff based in Germany were quick to notice that something was not right and immediately took to Twitter to warn users not to access the website. The website was then taken offline to prevent further infections.
This desktop application was not one offered by the site themselves, but one being offered by the hackers in order to distribute malware. It is still not known what malware the file, called “CrunchyViewer.exe”, was looking to distribute. Later the same day Ellation, Crunchyroll’s parent company, released a statement detailing what occurred and giving instructions on how to remove the malicious content if it was downloaded.
In the statement issued by Ellation, it was stated that at 3.30am PST hackers gained access and altered their Cloudflare configuration. Cloudflare is responsible for redirecting traffic to Crunchyroll’s servers. The attackers redirected incoming visitors intending to visit the Crunchyroll.com website to a non-Crunchyroll-hosted server with the intent for visitors to download the malicious file. The malware directly targets Windows users. It an example of how to respond to such events, the site was taken down at 6:00 am PST as a precaution and were able to re-secure and restore the correct configuration to our Cloudflare service at 9:00 am PST. Service was restored to users by 9.30am. Crunchyroll is confident that none of its servers were affected in any way as the hack appears limited to the Cloudflare layer. If this is so Crunchyroll was a victim of a DNS hijack of sorts.
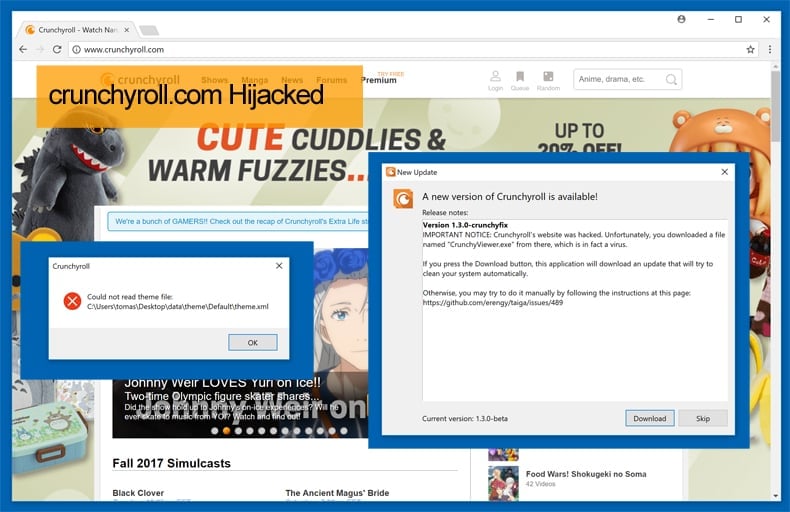
What was installed by CrunchyViewer.exe
When the CrunchyViewer.exe program was downloaded and executed, it would extract an embedded base64 encoded file to %AppData%\svchost.exe and execute it. When the malicious executable starts, it will create an autostart called Java that launches the %AppData%\svchost.exe program when the victim logs into the computer. That is what is known, currently, the rest is a mystery.
Security researcher Bart Blaze has been analyzing the code, he feels that the malicious code may be a keylogger. In Blaze’s detailed write up he questions whether the attack was indeed a DNS hijack as he could find no evidence to prove it as such. Additional researchers have made claims that the download can act as a backdoor for installing ransomware but Blaze has found no evidence of this either. It appears that the malware actually downloads Meterpreter, which is a default Metasploit payload. Metapreter can be seen as a backdoor as it allows the attacker to completely control your machine. In the write-up Blaze contends that it is still uncertain as to what exactly happened but he was full of praise for Crunchyroll and their response in containing the threat.
What to do in case of infection
If you downloaded the malicious file and did not execute it is advised to do the following:
- Delete “CrunchyViewer.exe” from your file system
- As precaution, please perform a scan with an antivirus product
If you downloaded and executed the malicious file you can perform the following actions to disinfect your computer:
- Delete “CrunchyViewer.exe” from your file system
- Remove the malicious “Java” Run key (You can find Information on how to edit the Windows Registry in the Microsoft support database if you are unfamiliar with the steps)
- Open Regedit, and browse to: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Delete the Java key
- Remove the malicious binary, by navigating to: %appdata%\Roaming (for example: C:\Users\Yourusername\AppData\Roaming\)
- Delete the ‘svchost.exe’ file
- Perform a scan with your installed antivirus product
Preventing is rather simple as if you did not download the malicious file you have nothing to worry about. In order to prevent future infections carried out by similar methods the following steps should be followed:
- Install an antivirus
- Keep your browser up-to-date
- Install NoScript if you have Firefox
- Install a 'well-rounded' ad-blocker, for example, uBlock Origin (works with most browsers)
- If a website you visit frequently suddenly looks completely different or urges you to download a file for whatever reason rather do not and leave the website.
- Additionally, try to Google or use social media to verify if anyone else is experiencing the same issue.
DNS Attacks
While it still may not be definitive that Crunchyroll experienced a DNS attack, they are a favored method of hackers globally to carry out their agenda. A domain name server (DNS) attack is where an individual redirect queries to a domain name server (DNS), by overriding a computer’s TCP/IP settings. This can be achieved through the use of malicious software or by modifying a server’s settings. Once the individual performing the DNS hijacking has control of the DNS, they can use it to direct traffic to different websites.
There is widely believed to be two major kinds of DNS attack. The first type DNS hijacking that involves infecting computers with malware or DNS, which determines computers to no longer translate the user-friendly domain names to the correct corresponding IP addresses. The second type involves hacking certain websites and literally having their DNS addresses changed so that visitors from these websites end up visiting completely different destinations online. This method was most likely used in the above-reported incident.
There is often a misconception relating to the seriousness of DNS attacks. In this instance, malware was indeed downloaded. Often it may be something regarded as inconvenience such as not been able to watch your favorite anime, but DNS redirecting can be used to monitor your every move and site visited on the internet. DNS attacks have also been used by governments to impose a certain level of censorship on their citizens.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion