Zealot Leveraging NSA Exploits to Mine Monero
Researchers at F5 Networks have been analyzing and monitoring an advanced and aggressive malware campaign. They have termed the campaign Zealot, the name derives from one of the files dropped on targeted servers called zealot.zip. Currently, it appears as only Linux and Microsoft servers are been targeted. The servers are been attacked with an assortment of exploits with the goal of installing malware that mines the Monero cryptocurrency. As has been seen throughout the year, Monero has become the favored cryptocurrency of cybercriminals for its increased anonymity features.
According to Maxim Zavodchik and Liron Segal, two security researchers for F5 Networks, the attackers are scanning for servers that are still vulnerable to two exploits, the first being Apache Struts (CVE-2017-5638) and the second being DotNetNuke ASP.NET CMS (CVE-2017-9822). If these are unpatched the attackers will be able to gain a foothold in the unpatched network.
The Zealot Campaign in Greater Detail
In this campaign, researchers discovered that the Apache Struts flaw included payloads for targeting both Linux and Windows machines at the same time. Added to this, as the Zealot campaign targets both Windows and Linux systems aggressively with the DNN and Struts exploits together it can be regarded as one campaign rather than two from the same attacker. When analyzing the code, it appears extremely obfuscated. Researchers discovered that despite being obfuscated the code hid a much more sophisticated multi-staged attack, with lateral movement capabilities, leveraging the leaked NSA-attributed EternalBlue and EternalSynergy exploits. While the Zealot campaign is mining Monero, the attackers can use compromised systems to do whatever they want.
The attack begins with the threat actor scanning the web and sending two HTTP requests. The first request is the notorious Apache Struts exploit. Traditionally the exploit targets either Windows or Linux servers. Zealot, however, targets both. If a server is determined to vulnerable it will execute JAVA code to determine the underlying OS. When a vulnerable Linux server is found the malware will try to fetch the script using several methods. First, it will try to connect to a remote server over a TCP socket and redirect the received data directly to the shell. If this fails it will then use “curl” and “wget” tools (that ship with Linux) to download a file name “larva”, then execute and delete it immediately once executed.
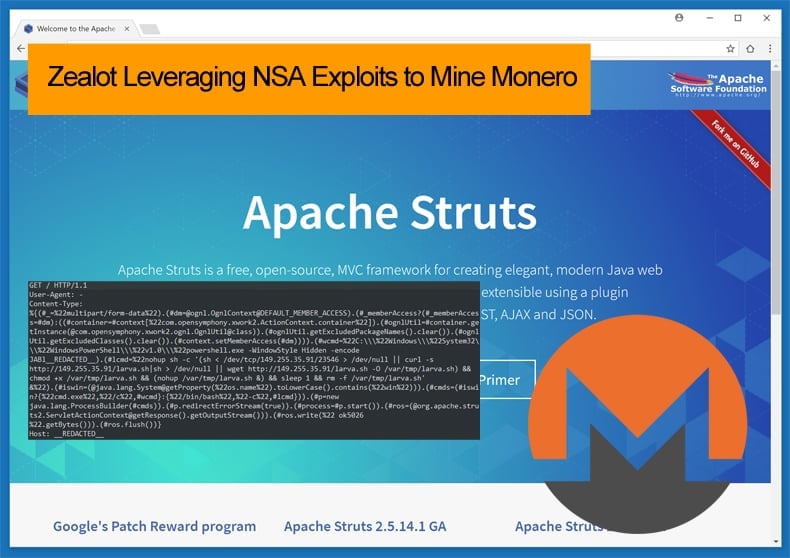
If a vulnerable Windows server is found the STRUTS payload will run a PowerShell interpreter in a hidden mode, which will run a base64 encoded code. Once decoded two times, the result is another obfuscated script. The code reveals a URL to another file to be downloaded from another domain. It will then proceed to download a file in PowerShell script “scv.ps1”. This main deployer will then download the miner, known to the infosec community as Mule. On Linux servers, Python scripts that appear to be taken from the EmpireProject post-exploitation framework are used to install the Mule miner. One of the interesting aspects of Zealot is its ability to propagate on internal networks. One of the ways it does this is by checking if Python 2.7 is installed on the compromised network. If not it will download the python installer and deploy it. Then it will download the main python module (“probe.py”) which initiates the propagation into the internal network. The second method applicable to Windows servers is the attacker’s use the now infamous EternalBlue and EternalSynergy NSA exploit tools leaked last year.
Not a Bad Day in the Office
From the Monero wallet addresses collected the researchers have determined that the attackers behind the campaign have made at least $8,500 from their attacks. This may not be the limit to their attack as they may have other Monero wallets, meaning the total sum could be much higher. Those responsible appear to be Starcraft, a popular strategy game, fans as many of the files associated with the payload are taken from the game, such as Zealot, Observer, Overlord, Raven, as well as others associated with the popular franchise.
The two researchers, Zavodchik and Segal concluded that “The level of sophistication we are currently observing in the Zealot campaign is leading us to believe that the campaign was developed and is being run by threat actors several levels above common bot herders,” Pointing to the use of a multi-stage infection chain, advanced and customized malware, and attention to moving laterally through networks as evidence of this.
The Notorious Apache Struts Vulnerability
The Apache Struts vulnerability made international headlines as being the flaw that was exploited in the Equifax data breach. The vulnerability, which was patched, allowed attackers to steal data from over 143 million customers, from both the US and the UK. News of the breach severely affected Equifax’s stock price and cost the jobs of a few upper management personnel. In another incident the vulnerability was leveraged to install ransomware on targeted Linux and Windows servers, ultimately netting the attackers over $100,000.
Essentially the vulnerability, when used for nefarious reasons, would allow an attacker to execute commands on the server via content uploaded to the Jakarta Multipart parser component, used in some Struts applications. According to the Apache Struts website, “Apache Struts is a free, open-source, MVC framework for creating elegant, modern Java web applications. It favors convention over configuration, is extensible using a plugin architecture, and ships with plugins to support REST, AJAX and JSON.”
Shortly after the vulnerability was announced and patched the following Monday, researchers at Cisco’s Talos Security team saw the vulnerability been leveraged in attacks. Nick Biasini, one of the researchers on the team rather prophetically stated that “It is likely that the exploitation will continue in a wide scale since it is relatively trivial to exploit and there are clearly systems that are potentially vulnerable,” Several attacks were detected by the researchers at Cisco. Despite the flaw been patched it seems attackers still feel that Linux and Windows servers remain unpatched and it is worth scanning the internet for those servers in order to drop a payload in the hopes, it will result in a payday.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion