SamSam Ransomware Targets Hospitals
The hacking group behind SamSam attacks have been busy striking high profile targets since the beginning of January. These targets include hospitals, a city council, and an ICS (Industrial Control Systems) firm. Reported attacks include the one against the Hancock Health Hospital in of Greenfield, Indiana; Adams Memorial Hospital in Decatur, Indiana; the municipality of Farmington, New Mexico; cloud-based EHR (electronic health records) provider Allscripts; and an unnamed ICS company in the US. Unlike many other ransomware campaigns the group behind SamaSam, also sometimes referred to as Samas, use the variant in a targeted way not relying on massive phishing campaigns.
On January 18 the Greenfield Reporter published an article detailing the SamSam attack on Hancock Health Hospital. Hospital officials admitted that hackers’ targeted more than 1,400 files, the names of every one temporarily changed to “I’m sorry.” They gave the hospital seven days to pay or the files would be permanently encrypted but no patient records were jeopardized. Since the attack, an analysis of the attack revealed the believed location of the attackers is somewhere in Eastern Europe.
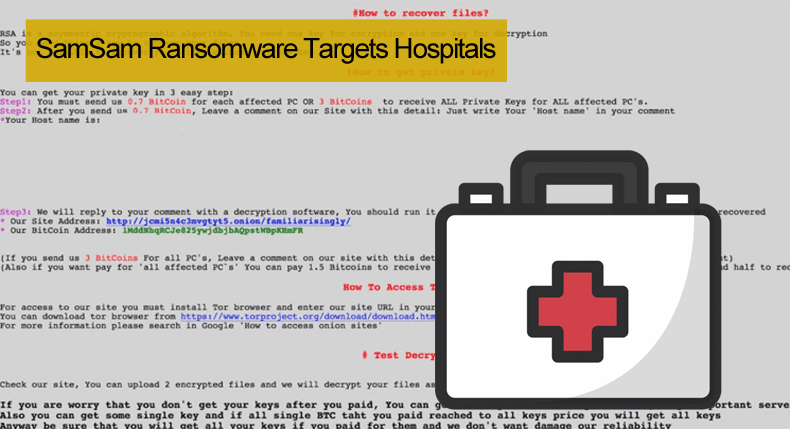
Despite the consensus among security experts to never pay the ransom, Hancock Health CEO Steve Long admitting to paying the ransom demanded by the group behind the attack. In this instance, Hancock Health paid 55,000 USD to regain access to its computer systems. This was despite the hospital having sufficient backups to recover the encrypted files. The reason given by the hospital to pay the ransom and not rather restore the backups is that it might take days to restore and could potentially be incredibly costly. Like in the majority of ransomware attacks the ransom instructed payment was to be made in Bitcoin. Hancock had to pay 4 BTC according to the ransom note in 7 days or suffer permanent encryption.
Luckily for the hospital, the hackers stayed true to their word, releasing the files early Saturday after retrieving the bitcoins uploaded to the web. By Monday, the hospital’s computers systems were up and running, though Long anticipated there could be some glitches to address in coming days and weeks. Staff members at the hospital noticed computers were running slower than usual Thursday evening. A short time later, a message flashed on a hospital computer screen, stating parts of the system would remain locked until a ransom was paid. It was later learned the hackers gained access to the system by using the hospital’s remote-access portal, logging in with an outside vendor’s username and password rather than the more common method of getting an employee to open a malicious email.
Officials confirmed that no equipment used to treat or diagnose patients were impacted by the attack. Most patients likely didn’t notice there was a problem, though the hospital’s patient portal, which allows patients to view their medical records online, was down and could have caused an inconvenience, officials said.
Other Reported Instances
According to data provided by the ID-Ransomware service, there have been 17 submissions of SamSam-related files to the service in January alone. On January 11 Adams Memorial Hospital confirmed that a ransomware attack targeted some of its computer servers. Adams Health Network, the company that runs the hospital, has not disclosed the sum of the ransom request or whether it complied. In a statement to the press a spokesperson for Adams Health Network stated,
“While AHN did experience a business interruption throughout the weekend as we worked to restore the affected servers, there was never an interruption in patient care. We are continuing to assess the severity of the situation, but at this time we believe no patient files have been accessed. At no time during this event has the quality and safety of patient care been affected.”
The City of Farmington also suffered the same attack. City Manager Rob Mayes confirmed that the FBI advised the city not to pay the 3 BTC ransom that was demanded. Mayes said the city was able to recover the encrypted information without paying the ransom. It is the standard protocol of the FBI to advise against paying the ransom according to their website. The FBI is of the opinion that paying a ransom not only encourages current cybercriminals to target more organizations, it also offers an incentive for other criminals to get involved. The organization targeted by the ransomware might also inadvertently be funding other illicit activity associated with criminals.
SamSam Variant
Whereas most ransomware is automatically propagated, SamSam is deployed manually. This is done by scanning the Internet for computers with open RDP connections and they break into networks by brute-forcing these RDP endpoints to spread to more computers. In order to install the ransomware, the group behind the campaigns begin by using the open-source JexBoss Exploit Tool to identify and exploit vulnerabilities in application servers running on Red Hat JBoss Middleware. Once the server has been compromised, the attackers use information-stealing malware to gather credentials and other information about the host network, facilitating lateral expansion across the network. Next, the attackers generate an RSA key pair and upload the public the public key and the ransomware itself onto the compromised systems using batch scripts, deleting volume shadow copies in order to avoid detection. The SamSam variant is capable of avoiding detection by disabling built-in Windows protection mechanisms, such as System Restore, Safe Mode, System Recovery, and Windows Error Reporting. In addition to killing any attempts to run Task Manager, it can disable other tools such as the Microsoft Registry Editor. Once SamSam encryption is complete, the SamSam ransomware deletes itself.
This is all an indication of how organized and proficient the group behind the campaign is. It is also important to note that the group leveraging SamSam also adjust ransoms according to who they are targeting. This is done in an attempt to maximise the possibility of payout by the victim. By offering a ransom that may be cheaper or more convenient than paying for restoring files or the cost of being unable to do business for a period will be a temptation to business leaders forced to make a difficult decision.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion