New MacOS Trojan Seen in the Wild
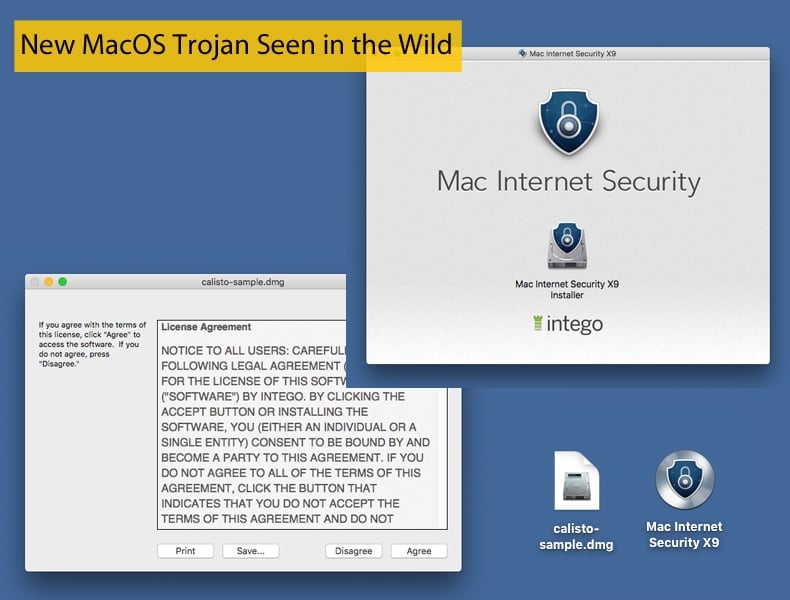
While malware targeting Mac users is far from common when compared to other platforms, Mac users should be aware that they are not immune to malware infections. Security researchers at Kaspersky last week detected a new variant of the Mac malware Proton, which they have called Calisto. According to those researchers, the malware was uploaded to VirusTotal way back in 2016. This is most likely the same year it was created. For two years Calisto remained off the radar of antivirus solutions, until May of this year with the first detections appearing on VirusTotal. Researchers of the opinion that Calisto may be a precursor to Proton which made InfoSec headlines in 2017. It would appear that Calisto is distributed via a fake Intego Mac Internet Security X9 installer. This is similar to Proton’s delivery method in that the Trojan was distributed and installed at one stage via a fake Symantec app. The distribution was made possible by the malware authors creating a fake Symantec blog which was search engine optimized to direct traffic to it.
This was not the only method employed by the malware authors. It was later seen in the wild when the popular DVD ripping tool Handbrake was hacked to distribute Proton in May 2017. It was seen again in October 2017 following a hack of the Eltima Software website that resulted in Elmedia Player and Folx being modified to drop Proton.
While the delivery method alone is not sufficient evidence to prove the link between Calisto and Proton the researchers at Kaspersky have pieced together other bits of evidence. As far as it is known members of the Proton malware family were distributed and discovered in 2017. The Calisto trojan detected was created no later than 2016. Assuming that this trojan was written by the same authors, it could well be one of the very first versions of Backdoor.OSX.Proton, or Proton for short, or even a prototype. The latter hypothesis is supported by a large number of unused and not fully implemented functions. However, they were missing from later versions of Proton. Also like Proton, Calisto is able to steal a great amount of personal data from the user system, including the contents of Keychain and the sample analyzed contains the line “com.proton.calisto.plist.” All this combined creates a strong case that those behind Calisto were also behind Proton.
Calisto’s Behaviour
Fortunately, it would appear that Calisto can be described as dead in the water. This is due to the fact that the server it attempts to call home to no longer exists. Further, with the addition of System Integrity Protection (SIP) to Mac OS X 10.11 (El Capitan) on September 30, 2015, caused problems for this malware. SIP is a security feature which comprises a number of mechanisms that are enforced by the kernel. The main result of this feature is the protection of system-owned files and directories against modifications by processes without a specific “entitlement”, even when executed by the root user or a user with root privileges. Despite this Calisto is dependent on being able to make changes to several SIP-protected locations, and some of its functionality fails on El Capitan or later systems.
This does not mean that Calisto is completely harmless this despite the fact the malware is unable to perform some of its duties on a modern system. As mentioned above Calisto will still gather password-related files, just like later variants of Proton, meant for exfiltration to a malicious server if it were ever to become operational. Another aspect that poses a threat is the issue of malware leaving behind sensitive data for other future attackers to find. Security researchers at Malwarebytes published an article that dealt specifically with this threat. In the article another piece of malware targeting MacOS was analyzed, this time rather than it being a trojan the malware, named OSX.Dummy, was probably designed to steal cryptocurrency as it targets the crypto mining community. One of Dummy’s features was the ability to steal a password and store it for later use. Both Calisto and Proton also do this, so even if the malware poses no immediate danger a password could be stolen and stored without the victim’s knowledge. This information could be found by another threat actor and exploited. This would be considered an incredibly lucky day for the threat actor and an unlucky one for the victim.
Defending against Calisto
When malware authors exploit legitimate downloads they can be incredibly hard to defend against. One way to defend against Calisto, Proton and other such trojans is to verify you are downloading a legitimate version of the desired program. One method of doing this is by checking the MD5 hash code that is associated with every download. Professor Ronald Rivest of MIT created the MD5 cryptographic hash function in 1991 to replace the earlier MD4 algorithm. It employs a 128-bit hash value, typically expressed as a 32-character hexadecimal number. This code can be used to test the file integrity and make sure it has not been tampered with. File integrity can be checked by comparing the original hash code with one of the downloaded files if they match the files integrity is assured.
The OpenOffice.org website provides some instructions on how you can verify MD5 hashes on a variety of platforms. The tool provides verification instructions for the MD5 Hash Tool extension for the Firefox browser regardless of OS, the digestIT tool for MS Windows, and the md5sum command line tool for Linux systems. If you are worried that your Mac could be infected by this or any other malware, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically detect and eliminate any possible infections.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion