Fallout Exploit Kit Distributing SAVEFiles Ransomware
Last week this platform published an article which covered the emergence of a new exploit kit called Fallout discovered by security researchers at FireEye. Initially the exploit kit has been used to distribute the SmokeLauncher trojan and the GandCrab ransomware. This week, it has started to distribute a new ransomware called SAVEfiles via malvertising campaigns.
SAVEFiles was discovered by security researcher Michael Gillespie, who has developed a reputation for discovering and analyzing new ransomware variants. While the ransomware was discovered by Gillespie it was not known necessarily how the ransomware was distributed. Exploit kit expert Kafeine discovered that SAVEFiles was been distributed via malvertising campaigns where IP addresses in Japan, France, and other locations have been targeted. It was further discovered that the campaign will cause the visitor to go through a stream of redirects until they eventually get to a site hosting the Fallout Exploit kit. The exploit kit will then automatically download and install the SAVEfiles ransomware onto the victim’s computer. The connection to hxxp://xxxart.pp.ua/1/get.php is the ransomware connecting back to its Command & Control server to receive an encryption key.
One of the interesting things about SAVEFiles is that while it is encrypting files on the victim's computer the ransomware will also create ransom notes in each folder called !!!SAVE__FILES__INFO!!!.txt. These ransom notes will tell the victim to contact the attackers at BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.ch or savefiles@india.com for payment instructions. Often attackers will rely on just one ransom note.
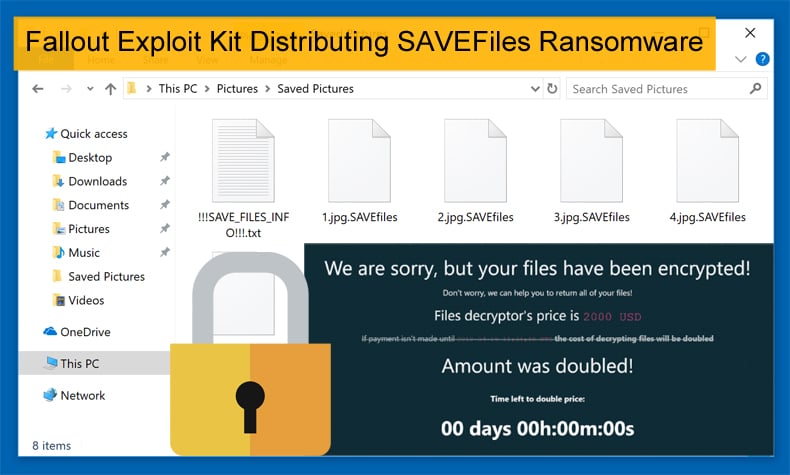
Another point of interest concerns the ransom note as no ransom is given rather victims would need to contact the attackers to find out how much they would have to part with in order to decrypt the victim’s files. The note itself is presented to the victim as a service provided by the attackers rather than the malicious attack it is. This is a commonly used tactic by those using ransomware to expropriate funds from victims. If only they were providing a useful service rather than deliberately encrypting files in order to make a quick buck.
Fallout
Discovered in August of this year, Fallout is a very new exploit kit and appears to be used exclusively in malvertising campaigns in an attempt to create backdoors on targeted computers. In an article published on Bleeping Computer, Kafeine told the publication that Fallout is an updated version of Nuclear Pack which was initially discovered in 2009. Nuclear Pack was a popular kit sold on the Dark Web which was capable to deploy a wide range of attacks, from Flash, Silverlight, PDF, and Internet Explorer exploits to the possibility of launching advanced pieces of malware and ransomware at the time. It was used by attackers as the main vehicle to exploit zero-day vulnerabilities with the purpose of data exfiltration among other nefarious purposes.
While similar in mode of operation to Nuclear Pack, Fallout is used by attackers hacking into sites or generating new ones that they then host the exploit kit scripts on. Attackers then use malvertising to redirect users to the sites where the code is located. Fallout attempts to exploit vulnerabilities in VBScript and Flash Player on visitors’ machines, a commonly used tactic abused by numerous other exploit kits. All a victim has to do is be redirected to or visit a site that is running the exploit kit, and if they are vulnerable they will have malware automatically installed onto their computer. Proving to any who doubts the importance of updating software the importance of taking the time to do so. Because of software vendors improving their approaches to securing software and authorities cracking down on the authors of exploit kits their use declined in recent years. Despite this, it is important to remember that exploit kits are still a threat, even if they are an opportunistic one.
Ransomware dominating Headlines
Ransomware, by all accounts, was declared dead at the start of the year with the rise of cryptocurrency miners. The malware’s death was declared prematurely. In March 2018, the City of Atlanta suffered a major ransomware attack costing the city millions of dollars in damages. As a result of the attack, the Hartsfield-Jackson Atlanta International Airport shut off Wi-Fi service as a security precaution while the active ransomware attack took place in the city. The airport is regarded as one of the busiest airports in the world, if not the busiest, and the shutdown would have been at best a minor nuisance to passengers using the airport.
The most recent casualty of ransomware is Bristol Airport, in the UK. On September 16, it was reported that flight information screens were blacked out over the weekend at the airport. Airport officials blamed the incident on a ransomware infection that affected the computers running the airport's in-house TV screens displaying arrival and departure flight information. Upon initial analysis conducted by officials, it would appear the infection began on the Friday before the weekend. The infection resulted in officials having to use paper posters and whiteboards to announce check-in and arrival information for flights going through the airport. Passengers were advised via social media to arrive early and allow extra time for the check-in process as a direct result of the infection. Speaking to local press over the weekend, airport officials said they did not intend to pay the attacker's ransom demand and opted to take down their systems while they serviced affected computers. Fortunately, no flight delays or cancellations resulted from the major inconvenience.
Ransomware didn’t die as many hoped it just became used in far more targeted attacks. Like exploit kits, researchers can never declare a malware dead. It will return like a bad zombie movie.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion