Vidar and GandCrab Distributed in Same Campaign
With the recent spate of cyber-attacks utilizing two or more different malware variants or tactics, the smart money would have predicted the trend to continue into 2019. In a recently discovered campaign, the smart money appears to be right. Hackers are targeting victims with a two-pronged attack that secretly infiltrates systems with data-stealing malware, before dropping ransomware onto the infected system. In a report published by researchers based at Malwarebytes, this new campaign employs the Vidar data stealer and the now infamous GandCrab ransomware.
Many of the world’s hackers see no need to reinvent the wheel and those behind this campaign seem to fit the mold. The malware is distributed via the tried, tested, and the approved method of a malvertising campaign. The hackers in this instance have been targeting high-traffic torrent and streaming sites in an attempt to try and lure victims into clicking on a risky link and which will redirect victims to a site hosting the malicious payloads. While using tried and tested malvertising techniques the hackers again use a well-known method of delivery, the Fallout exploit kit. The exploit kit appeared to have surfaced in August 2018, at a time when many researchers felt that exploit kits were going the way of the dinosaur. The kit uses a number of exploits which target Internet Explorer and Flash Player in order to get a foothold onto the victim’s computer.
In the past, the kit has been used to distribute GandCrab and the SmokeLoader trojan, a piece of malware used generally to help facilitate the installation of other malware variants onto a victims computer. Towards the last quarter of 2018 GandCrab featured prominently in news headlines. The ransomware garnered a substantial amount of attention when its malware authors released the decryption key for Syrian victims in a show of compassion. Based on the released key Europol and Bitdefender in a collaborative effort managed to create a decryption key that could be used on the vast majority of GandCrab versions out there. Sadly, this has not stopped other hackers from using GandCrab, with many hackers opting to target businesses in the hope of an easier payout.
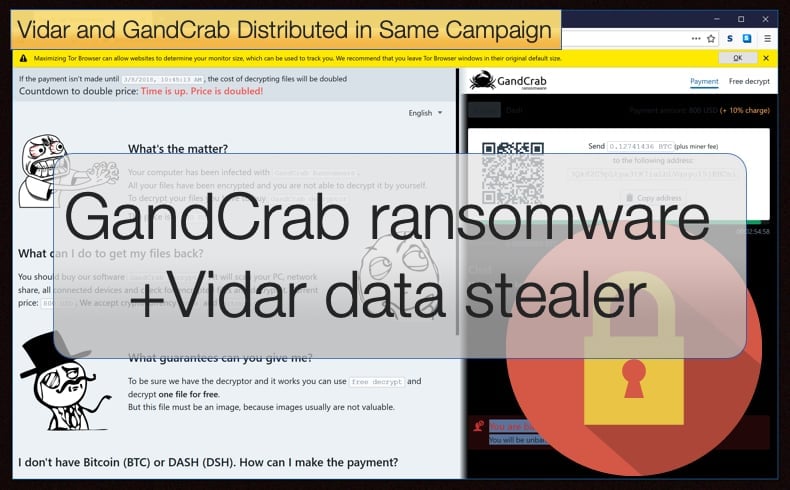
GandCrab also poses another threat to users in the sense that it is constantly been updated in order to make it harder for security software to detect and analyze. Newer versions often incorporate new features making it more effective. This has certainly helped ensure the ransomware’s popularity amongst cybercriminals. In this instance, the hackers deploy GandCrab version 5.04 once the data stealer has been deployed. The system is then encrypted and a ransom note displayed, demanding payment in either Bitcoin or Dash in exchange for retrieving the files. This is a proven money making scheme, however, researchers think the deployment of GandCrab maybe a smokescreen to stop them uncovering the initial Vidar. In an interview with ZDNet Jérôme Segura, security researcher head of investigations at Malwarebytes, said,
“It could be, for instance, a simple decoy where the real goal is to irreversibly corrupt systems without any way to recover lost data. But as we see here, it can be coupled with other threats and used as a last payload when other resources have already been exhausted…As a result, victims get a double whammy. Not only are they robbed of their financial and personal information, but they are also being extorted to recover the now encrypted data,”
Vidar Data Stealer
Those familiar with Norse mythology may recognize something familiar with the information-stealing malware. It would appear that the malware is named after the Norse god Víðarr the Silent, sometimes referred to as the silent one was believed to be a son of Odin and is foretold to avenge his father's death by killing the wolf Fenrir at Ragnarök. Typically seen as the god of vengeance the malware authors probably saw the similarity between the silent one and the stealthy piece of malware. The malware is relatively new and has been described as an Arkei copycat. Vidar seems to have emerged in October 2018 and is written in C++.
The information stealer boasts all the features cybercriminals have come to expect from such malware variants. Features include:
- Searching for specific documents
- Stealing ID from cookie browsers
- Stealing browser histories (including tor browsers)
- Stealing wallets
- Stealing data from two-factor authentication software
- Grabbing messages from various messenger software packages
- Screenshot capabilities
- Loader settings
- Telegram notifications (on server-side)
- Get a complete snapshot of all information of the victim’s system.
The malware is also available to buy for a price ranging from 250 USD to 700 USD. As an added bonus to those who have purchased the information stealer, they will also gain access to a C2 Shop portal where they are able to generate their own payloads. Finding the portal via other methods can prove to be difficult as the portal’s domain is changed every four days.
The use of Vidar in this instance has some noteworthy uses. Such malware is typically designed to operate secretly, leaving victims unaware that their systems have been compromised, while the attacker makes off with private information that's packaged up and sent to a command and control (C&C) server. Well, not particularly noteworthy what researchers would find interesting is that the information stealer also operates as a downloader for additional forms of malware, in this instance the previously mentioned GandCrab ransomware.
In order to not fall victim to the latest malvertising campaign, it is advised to keep systems and software up to date. This prevents drive-by downloads from using known exploits to gain a foothold. Further users can use various web protection and ad blocker software packages which prevent the user from being maliciously redirected from malvertising campaigns.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion