Phobos Ransomware Emerges from the Dark
Discovered in December 2018, a new ransomware variant called Phobos was discovered by researchers at Covewave which it would seem is a combination of the Dharma and Crysis ransomware variants. The naming of the new ransomware variant will pique the interest of those fond of Greek Mythology as Phobos was the god of fear who was the son of Ares and a brother to Deimos the god of terror. With such a strong name questions will be asked as to whether the malware is indeed something to be scared of.
In the report published by Coveware what readers will initially find the most striking is the similarities to the Dharma ransomware variant that has been used so successfully over the years. These similarities go so far as to use the same attack vector that Dharma has, namely open or poorly secured RDP ports. The leveraging of unsecured RDP or Remote Desktop Protocols ports is a favored attack method of hackers. In September 2018, the FBI warned businesses owners to secure these ports as a spike in attempts to gain a foothold in a network was seen exploiting this attack vector. One such attack campaign seen was a campaign using the Crysis ransomware, a closely related cousin to Phobos.
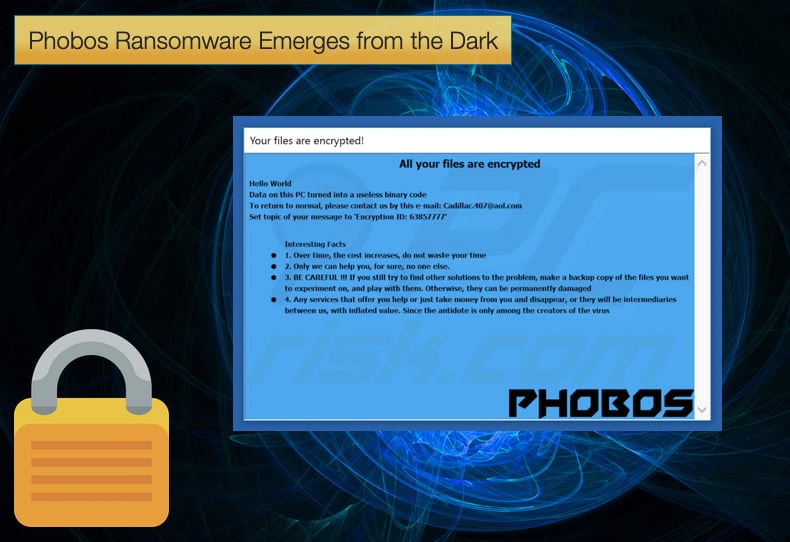
Another striking similarity between Phobos and Dharma can be seen once the newer of the two infects a computer and encrypts data using the .phobos extension. Both use the same ransom note. In a classic case of the cliché, “if it’s not broken don’t fix it,” the ransom note is the same down the typeface and wording. A difference between the two notes does exist, although a minor one, logos used by malware authors to differentiate Phobos from Dharma have been added to the note. The cut and paste job does not end there with much of the code behind the ransomware being the same. This strongly suggests those behind Dharma and Crysis are behind this latest Phobos campaign used to target businesses around the world.
To find the similarities between Phobos and Crysis a deeper dig under the hood is required. The researchers analyzing Phobos discovered that both share the same anti-virus detection module. The difference that sets Phobos apart may be minor, namely the encryption extension and new logo, researchers believe that “What is clear is that while the ransomware type may be different, the group distributing Phobos, the exploit methods, ransom notes and communications remain the nearly identical to Dharma,”
Dharma Gang More Than Likely Responsible
Security researchers at Covewave were quick to attribute Phobos to the same cybercriminal group behind Dharma. Such a quick pointing of the finger is dangerous but a lot of the facts are hard to argue with. The same researchers believe that Phobos is been distributed as an insurance policy for malicious campaigns, providing attackers with a second option for conducting attacks, should Dharma end up decrypted or prevented from successfully extorting ransoms from victims.
This idea of Phobos been an insurance policy is not without merit. According to Europol’s 2018 Internet Organised Crime Threat Assessment (IOCTA) report ransomware remains the top threat to organizations, causing millions of dollars of damage and remaining a potent tool for cybercriminals and nation-state attackers. In the report ransomware families including Crysis and Dharma were cited among those most damaging to businesses over the past 12 months. It was also noted in the report that rather than spam campaigns attackers have shifted to highly targeted attacks against specific organizations.
Europol concluded in regards to ransomware,
“Even though the growth of ransomware is beginning to slow, ransomware is still overtaking banking Trojans in financially-motivated malware attacks, a trend anticipated to continue over the following years. In addition to attacks by financially motivated criminals, significant, public reporting increasingly attributes global cyber-attacks to the actions of nation states. Mobile malware has not been extensively reported in 2017, but this has been identified as an anticipated future threat for private and public entities alike.”
And to cyber threats in general,
“As we have seen with other cyber attacks, as criminals become more adept and the tools more sophisticated yet easier to obtain, fewer attacks are directed towards citizens and more towards small businesses and larger targets, where greater potential profits lie,”
How to Prevent Phobos Infections
Whether Dharma or Phobos ransomware is still a major threat to contend with. It is not worth fearing Phobos or the numerous other ransomware families out there because there are easy ways to protect against the threat posed. It is important for organizations to secure their RDP ports and backup their data. RDP has become an easy and important way to better manage a Windows server, this convenience does come at a cost. In order to secure the RDP ports that are open or unsecured administrators can take the following steps:
- Use strong passwords
- Make sure software is updated
- Restrict access using firewalls
- Enable network level authentication
- Limit users who can log in using Remote Desktop
Administrators can further increase their security robustness by changing listening ports for remote desktops. This will help prevent hackers from scanning the network for computers listening on the default Remote Desktop port (TCP 3389). Researchers at Liquid Web argue that exploiting RDP is one of the easier methods of attack available to hackers. Given the above evidence, it is becoming increasingly vital to secure RDP ports as even unsuccessful attacks can cause damage and incur massive costs. As is true with so many convenient technologies the increase in convenience comes at a decrease in security which hackers and cybercriminals are more than willing to exploit.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion