WinPot Turns ATMs into Jackpot Machines
The dream of having an ATM give you money without ever deducting it from your bank account is a relatable dream for a large majority of the population. Real currency that can be spent as one wished with no repercussion on your own personal balance is too good to be true. Hacker’s beg to differ and have been hacking ATMs for years, often relying on the fact that most ATMs have outdated software, in most cases older versions of Microsoft, that has long since been abandoned and no longer receiving any support.
According to research published by Kaspersky Labs a new piece of malware designed specifically to hack ATMs. Called WinPot, quite literally turns the ATM into a slot machine. However, a slot machine implies there is a chance of winning. WinPot allows the “player” to always win and illegally receive cash from the machine. In order to install this type of malware the hacker needs either network access or to be able to physically access the machine itself. As detailed in another report published by Kaspersky Labs details how just using a 15 USD drill and drilling in the right spot will grant a hacker serial access to the computer within the ATM. Once this is done it is relatively simple to install the malware which replaces the ATMs normal display with four buttons labeled “SPIN”. Each “SPIN” button represents one of the four cassettes, the cash dispensing containers, in the ATM. When the hacker selects one cash is dispensed from that container. Kaspersky does not name the ATM brand but wisely just refers to it as a “popular” ATM brand.
WinPot which was discovered by Kaspersky in March 2018 has gone through a variety of versions to date. While a separate malware strain in its own right, researchers noticed that WinPot is most certainly inspired by another similar strain called Cutlet Maker. Discovered in 2016 Cutlet Maker also displayed detailed information about the contents of its victim ATMs, though rather than the slot motif it used an image of a stereotypical chef giving a wink and the hand gesture for “OK.” According to Konstantin Zykov, a senior security researcher at Kaspersky Lab, these similarities are best described as a feature and not a bug between the two. Further Zykov states,
“The latest versions of ‘cashout’ ATM software contain only small improvements compared with previous generations. These improvements allow the criminals to automate the jackpotting process because time is critical for them.”
While it would seem that the hackers developing the malware have a sense of humor, it is not without purpose. ATM malware such as Cutlet Maker and WinPot are uncomplicated and reliable, this certainly gives developers the space for a little creative flair, but the uncomplicated nature does allow for greater automation. The faster they penetrate the system the faster they can make away with their ill-gotten gains.
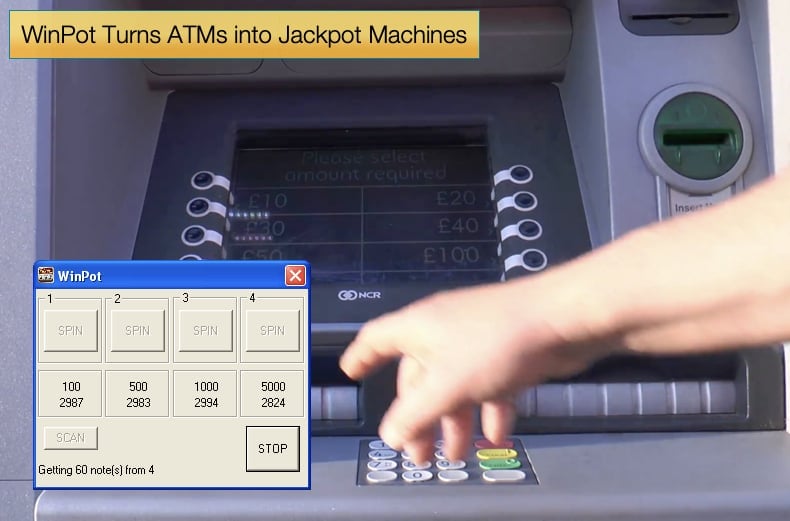
This means it becomes harder to catch the hacker as the time needed to catch them in the act is drastically reduced. However, it is also this need to gain physical access that is the malware’s major deployment hurdle. In countries with a pronounced law enforcement presence, the gaining of such access becomes exponentially harder while the possibility of getting caught is also significantly ramped up. Organized criminal gangs will deploy “money mules” in an attempt to combat this. The mule’s job is essentially to deploy the malware at ATMs and steal the funds, this leaves the one organizing the theft free of much of the liability. For all the mule’s efforts, they get a section of the proceeds but risk time in jail.
The Fate of the Mule
In 2017, Forbes published an article reporting on the fate of a group of individuals who used the Tyupkin malware to steal cash from ATMs across Europe. The gang of eight individuals was arrested in Moldovia and Romania and are believed to have made millions from the numerous thefts. It is unclear if the masterminds were caught but what was revealed is the fate of the mules used by the gang. The developers of Tyupkin were taking large chunks of income from mules who fundamentally took all the risk. One deal offered by someone controlling a variant of Tyupkin showed how the mules were so thoroughly swindled, even as they helped swindle the banks.
According to Russian cyber intelligence company Group-IB, a programmer posting on a forum in March 2017 sought mules to upload his Tyupkin version in ATMs across the world. They asked for 5,000 USD and in return, the mule would get the malware and attack code that had to be loaded onto a card. That card would eventually activate the malware at the target ATM with the malware then proceeding to instruct the ATM to empty its cassettes. That was the end goal. However, before this could be done the buyer would have to install the malware via a USB port, many the mule had to get physical access to the machine otherwise the card would not spew out funds. According to the agreement between “buyer” and “seller” the buyer had to hand over 40% of all the cash stolen. The buyer would take all the risk plus fork out 5,000 USD then still have to pay over a further 40% of the stolen proceeds. There is only one winner in that equation.
Combating this type of malware in itself is relatively easy. Companies installing and operating the ATMs need to install a software whitelist. This list will contain all the approved software which the machine can run all other software will be discarded. Despite the relative ease of preventing WinPot and other similar strains of malware of been deployed successfully it does not appear to be done. This lack of willingness to create and install such lists will ultimately enrich organized criminal gangs while further placing money mules at risk for the promise of a quick payout.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion