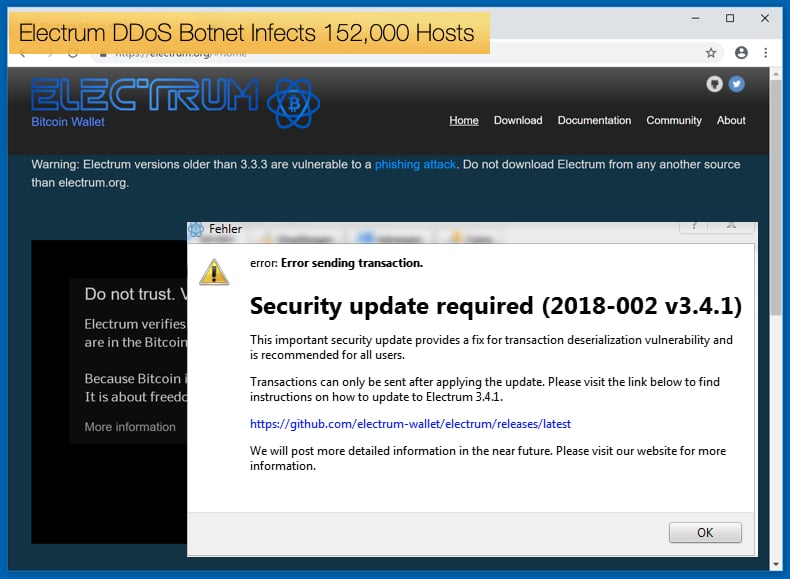
Electrum DDoS Botnet Infects 152,000 Hosts
Researchers at Malwarebytes have been closely following a sustained campaign against both users of the popular Electrum Bitcoin wallet and the company itself. What initially started out as a phishing campaign which was designed to trick users into downloading a malicious version of the wallet by exploiting a weakness in the Electrum software. This malicious wallet would then steal funds from the victim, by February of 2019 the attackers had stolen approximately 4 million USD, and in April this number has increased to 4.6 million USD. In February, the wallet's developers responded by exploiting the same flaw in order to redirect users to download the latest patched version.
For most incidents that would be the end, however, in March it became apparent that the software was in far more trouble than originally believed. The developers of the wallet actually had to attack their own users using an unknown vulnerability so that they couldn’t accidentally connect to a bad node exploited by the attackers. Now the attackers have responded by infecting machines with a botnet in order to carry out Distributed Denial of Service (DDoS) attacks against the wallet’s infrastructure. According to the researchers on April 24, the number of infected machines in the botnet was just below 100,000 and the next day it reached its highest at 152,000. The number of infected hosts keeps fluctuating but has seemed to plateau at over 100,000.
Previously the attackers used the RIG exploit kit and Smoke Loader to infect users and steal funds. These campaigns allowed for DDoS attacks using malware to drop and fuel the botnet infection has been called ElectrumDoSMiner. Researchers have detected a new piece of malware called Trojan.BeamWinHTTP which is also been used in the DDoS attacks. This recently discovered malware is also responsible for downloading the ElectrumDoSMiner often found on infected systems named as transactionservices.exe. The researchers have further analyzed the IP addresses associated with the bots to find out where they are geographically located.
The vast majority of bots reside in India and countries in South East Asia. In the Americas, the majority of bots reside in Brazil and Peru. In this constant campaign, the number of infected hosts keeps dropping then subsequently rising. Malwarebytes will remove 2,000 infections a day, despite this new infections occur daily to replace those numbers. This is a massively under-reported campaign that has cost victims a combined 4.6 million dollars. In this incident, the attackers wasted little to no time in exploiting a vulnerability then attacking the company when it had patched the flaw. The attackers are obviously committed given the amount of money potentially at stake.
DDoS Attacks Seen as Biggest Threat to Enterprises
In a recent study conducted by the Neustar International Security Council (NISC) which asked US and EMEA security professionals a series of questions determined that DDoS attacks are perceived as the highest threat to their organizations, with roughly half of their companies having been attacked in 2018. Further, it was discovered that at least 75% of those interviewed said that they are deeply concerned about bot traffic, whether bot robots or scrapers, stealing company information, despite the same number already deploying a bot traffic manager solution.
The interviews were conducted with 300 individuals holding the position of CTO, Director of IT, security consultants, or a number of other positions related to enterprise security responsibilities and from organizations based in the US, UK, France, Germany, Italy, and Spain. By interviewing industry professionals it enables better allocation of resources to help combat cyber threats. It also allows organizations to have a better view of the cyber threat landscape. To that extent, NISC Chairman and Neustar SVP and Fellow Rodney Joffe summarised the threat posed by malicious bots as,
“Unfortunately, bot traffic makes up a large proportion of the Internet. So it is key that organizations make sure incoming data is scrubbed in real-time, while also identifying patterns of good and bad traffic to help with filtering. [..] Implementing a Web Application Firewall (WAF) is crucial for preventing bot-based volumetric attacks, as well as threats that target the application layer.”
According to the NISC, 48% of respondents stated the threats posed by DDoS attacks have increased during November and December 2018, while 42% said that they have increased their ability to respond to DDoS attacks. This very real and rational fear appears to be driven by the rapid rise of the Internet of Things (IoT). Currently, cities, banks, and critical infrastructure operations are been connected to the Internet, this, in turn, has enabled malicious bots to cause havoc at a global level. The more devices which connected to the Internet increases this threat significantly. Further, more and more companies have to secure their devices from been used maliciously which in turn poses a myriad of further problems.
When all is considered this led Joffe to conclude,
“Without the appropriate detection, data scrubbing and mitigation tools in place, IoT devices have the potential to become part of a malicious botnet, whereby hackers essentially weaponize these devices to launch more powerful DDoS attacks. Worryingly, as more and more devices continue to connect to the Internet, these types of attack pose an increased risk to not only the defenses of an enterprise but also to a whole nation.”
Reviewing the campaign investigated by researchers at Malwarebytes it is clear that certain groups of hackers are not content just stealing money but are willing to retaliate when companies and organizations move to protect their users. One of the methods of retaliation available to hackers is a DDoS attack, applying the mentality of if they can’t steal then no one can use the platform or service. The study done by the NISC does make for worrying reading but it does mean that those in charge of an organization’s security are more than aware of the issue and hopefully more in the future will be down to combat the threat.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion