New Malvertising Campaign Distributes Exploit Kit and Ransomware
Researchers at Malwarebytes have discovered a new and large malvertising campaign which targets users of the popular YouTube to MP3 conversion website Onlinevideoconverter. According to SimilarWeb the conversion website is visited by over 200 million users a month, making it clear why it has been targeted by hackers distributing malware via a malvertising campaign. Such campaigns had fallen out of favor in recent months according to researchers at Malwarebytes with detections of such campaigns steadily decreasing. The latest campaign is a clear indication that the tactic is still a viable one for hackers to use.
Malvertising involves the malicious use of advertising to spread malware. One of the main methods in distributing malware this way is by hiding and then subsequently executing malicious code within relatively safe online advertisements. These ads can lead a victim to unreliable content or directly infect a victim's computer with malware, which may damage a system, access sensitive information or even control the computer through remote access. Malvertising is often used in conjunction with what has been termed by researchers as drive-by downloads and can be defined as the unintentional downloading of malware without the need for the user to click on a download link. The malware can be downloaded merely by clicking on an ad which is deemed safe by the user.
In a blog post published by Malwarebytes’ Director of Threat Intelligence, Jerome Segura, details of the latest campaign are revealed to the public. In this instance, the malvertising campaign distributes the “elusive” GreenFlash Sundown exploit kit. The exploit kit has been deemed elusive as it is rarely seen been used outside Asia with the majority of uses occurring in South Korea. The malware is spread through servers used to deliver ads by multiple publishers, including YouTube to audio conversion service mentioned above.
Once a user clicks on an ad they believe is for the conversion service the infection begins. Rather than been redirected to the service's website, visitors are sent to the exploit kit. Here the exploit kit will perform a number of checks to see if the visitor is a viable target. These checks are designed to see if the machine clicking the link is a virtual machine or not. If it is a virtual machine, a file designed to emulate an actual computer and thus will be of very little use to the hacker, the process ends.
If it passes the checks and is determined to be an actual machine the second stage of the infection occurs. This begins with the malicious code been hidden within a fake .GIF image which contains obfuscated JavaScript. The script links to a fast image website that delivers the malicious payload through another redirect to an adfast website. A Flash object contains the malware and executes it via PowerShell. If this is successful the exploit kit will drop the Seon ransomware and then slightly later will deliver a crypto miner as well as a data stealer. Malwarebytes in discussing this campaign when compared to previous campaigns using the GreenFlash Sundowner exploit kit concluded that,
“Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.”
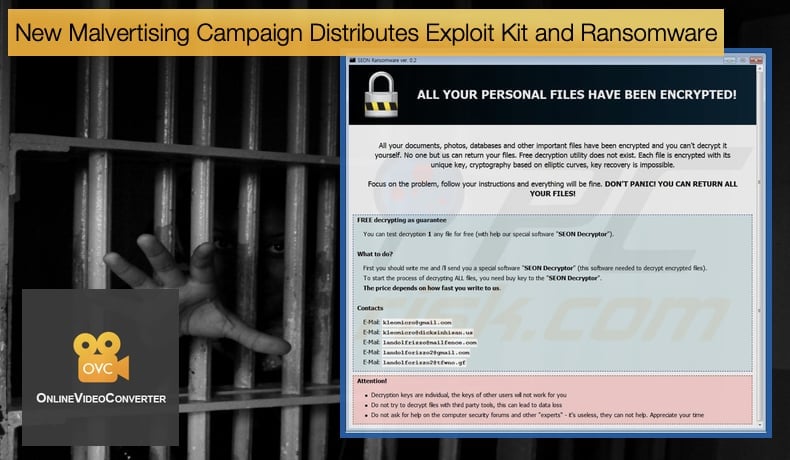
Seon Ransomware
The use of the Seon ransomware is what will interest many within the InfoSec community. The malware was first discovered in November 2018 by the Anti-malware Vigilante. Like other ransomware variants, it encrypts files, this time by adding the .FIXT extension then demands a ransom to be paid by in Bitcoin. Seon ransomware installs itself in the victim’s computer and searches for its target files which include audio files, video files, word documents, etc. It then encrypts the data files using strong cryptography algorithms. The ransomware generates two ransom notes one is placed on the desktop of the infected computer and the other is placed on the folder with the infected files. What separates Seon from other variants and makes it a worthy adversary, is that it will delete Shadow Volume copies on disk to prevent the recovery of data. By removing the shadow copies the ransomware removes the restore points previously set up by the machine, further making data recovery harder. The combining of ransomware within exploit kits is nothing new but it is still a deadly combination. When combined with Seon the danger level posed by the exploit kit is increased tenfold.
As mentioned above that malvertising took a dip in popularity amongst those operating in the cybercrime shadows. This latest campaign shows that malvertising campaigns are still a threat and need to still be taken seriously. In 2017 researchers at GeoEdge malvertising campaigns cost ad companies 1.13 billion USD. It was estimated at the time that the number for the following could increase from anywhere between 20% and 30%. In the same article it was also shown why images, including GIFS, are a popular attack vector. Researchers noted,
“Not every security provider monitors and analyzes images for malicious code on a constant basis. This creates an opportunity for the exploitation of a potential vulnerability in the embedded images which, if left undetected, could provide malicious advertisers with a potential windfall.”
The tactic of hiding malware in images has been called stenography and Adi Zlotkin, Security Research Team Leader at GeoEdge said that,
“We first noticed incidences of steganography – malicious code embedded in images – in early 2018 but since then, in the last few months, the number of such attacks has increased exponentially,”
Since then many firms have wisened up to this tactic and included security modules to prevent such abuse of images for the purposes of infecting users with malware. However, infections still occur and in instances such as the one discussed above an innocent click could result in the victim paying a ransom, mining cryptocurrency without their knowledge, or surrendering vital information.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion