The Common Types of Computer Infections
What is Mac Specific Malware?
Also known as: Mac virus
Mac specific malware is a type of malicious application that is targeted at Mac computers running MacOS operating system. A term Mac virus is commonly used but it's not technically correct. At the moment there are no Mac (or Windows) viruses in the wild. In theory a computer virus is malicious program that can self replicate when launched. In the early development of operating systems viruses caused a lot of damage, but nowadays computer viruses are totally extinct and are replaced by malware. While Mac malware and adware are not very widely spread nowadays more and more cyber criminals are starting to create malicious applications specifically targeted at Mac computers. Categories for Mac specific malware are the same as for Windows or Linux based operating systems, they range from potentially unwanted applications (relatively low harm) to trojans and ransomware (high risk infections). The market share of MacOS based computers is rising every year so cyber criminals are starting to search for alternative income sources and some of them are starting to attack Mac computers.
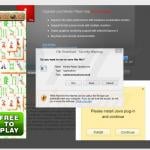
The most widely spread infections specifically designed for Mac computers comes in a form of potentially unwanted applications. Deceptive marketers are creating fake virus warning pop-up ads and fake flash player updates with an intention of tricking Mac users into downloading their unwanted applications. After the installation such apps scan user's computer and display exaggerated results stating that junk files and operating system cache files are high risk error, thus tricking Mac users into making unnecessary purchases.
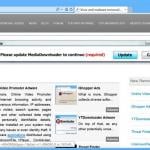
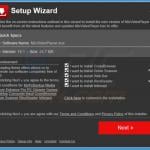
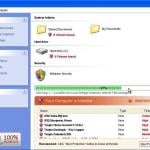
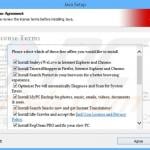
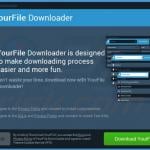
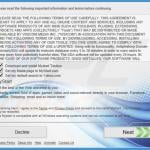
Screenshot of a deceptive free software installer that is used in adware and potentially unwanted application distribution:
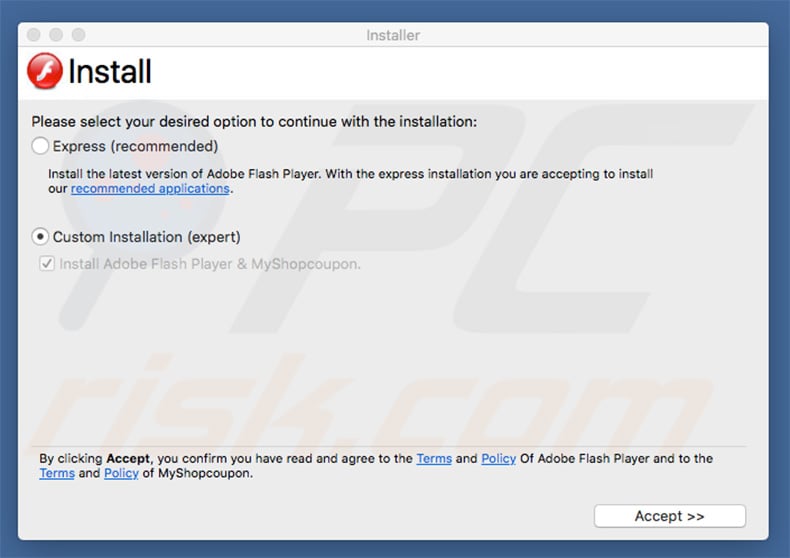
Another common form of Mac infections is adware. This type of infection usually infects user's computers using a deceptive marketing called bundling, Mac users install adware applications together with some free software downloaded from the Internet. After successful infiltration adware type applications generate intrusive pop-up and banner ads when browsing the Internet. Other types of adware redirect user's Internet searches through some unwanted websites.
Other Mac specific malware include Trojans, ransomware and cryptocurrency miners. Trojans aim to steal sensitive users data, ransomware aim to encrypt user's files and ask for a ransom in order to decrypt them and Cryptocurrency miners stealthily lurk on user's computer while exploiting computer's resources to mine crypto currency for the cyber criminals. These types of infections are not widely distributed but as Mac computers become more popular malware developers are increasingly targeting MacOS operating system.
Mac Specific malware symptoms:
- A program that you have not installed appeared on your desktop.
- Unwanted pop-up ads appear when browsing the Internet.
- Mac became slower than normal.
- Computer's CPU fan is working on it's highest capacity even when not doing heavy work on the computer.
- When searching the Internet through Google, Internet searches are automatically redirected to Yahoo or Bing search engine.
Distribution:
When it comes to malware distribution most commonly cyber criminals are using various social engineering techniques to spread their malicious applications. For example in a case of potentially unwanted applications, deceptive marketers use fake pop-up ads to spread their applications. In a case of adware - users usually install adware applications when tricked by fake flash player installers. Trojans and cryptocurrency miners are distributed using software crack downloads and hacked websites.
How to avoid installation of Mac specific malware?
To avoid installing malicious software Mac users should practice safe Internet browsing habits, this would include downloading software only from trusted sources (developer's website or official app store), not trusting online pop-up ads that claim about found infections or offer to download flash player updates. Mac users should stay away from downloading software cracks or game cheats. Using P2P services such as torrents also puts your computer security at risk. When downloading free software you should always pay close attention to the installation steps as they could hide installation of additional (most commonly unwanted) applications.
Most recent Mac Malware:
Most widespread Mac Malware:
What is Adware?
Also Known As: Unwanted ads or pop-up virus
'Adware' is a term used to describe a program that displays intrusive ads and is considered privacy invasive. Today, the Internet is rife with potentially unwanted applications that install with free downloads. Most free software download websites use download clients - small programs offering the installation of advertised browser plug-ins (usually adware) with the chosen freeware. Thus, reckless downloading of free software can lead to unwanted adware infections.
There are several types of adware: some may hijack users' Internet browser settings by adding various redirects; others may deliver unwanted pop-up ads. Some adware programs do not show any visible signs of infiltration, however, they are able to track users' Internet browsing habits by recording IP addresses, unique identifier numbers, operating systems, browser information, URLs visited, pages viewed, search queries entered, and other information. Moreover, most adware programs are badly programmed, and thus can disrupt the normal functioning of users' operating systems.
Adware Symptoms:
Slow web browser performance, annoying ads (searches, banners, text links, transitional, interstitial, and full page advertisements), browser redirects.
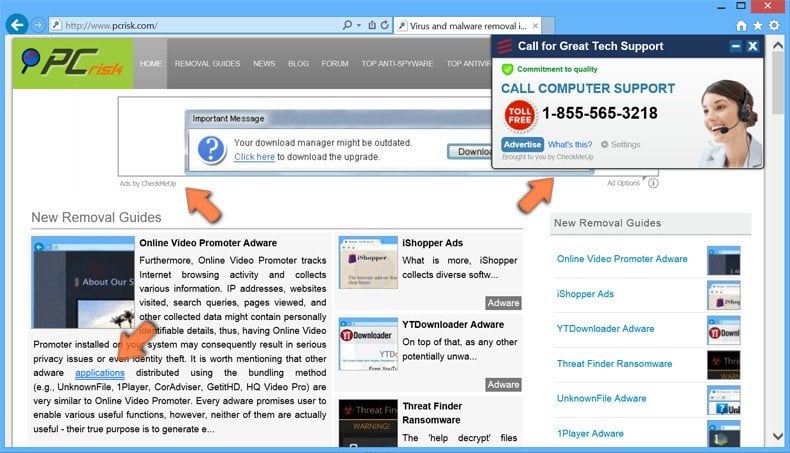
Screenshot of adware generating intrusive pop-up and banner ads:
Adware generating banner ads:
Distribution:
Adware is often included within freeware or shareware programs, and the installation of potentially unwanted applications can be caused by deceptive free software download clients and installers. Adware is also installed via fake Flash Player, Java, or Internet browser updates. Potentially unwanted programs are distributed by the use of misleading banners and other online ads.
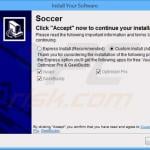
Screenshots of free software installers used to propagate adware:
How to avoid adware infections?
To avoid installation of adware, Internet users should express great caution when downloading and installing free software. If your download is managed by a download client, be sure to opt-out of installation of any advertised browser plug-ins by clicking on a 'Decline' button. When installing previously downloaded freeware, always choose 'Advanced' or 'Custom' installation options, rather than 'Quick' or 'Typical', since choosing the default options can lead to unwanted installation of bundled adware.
Most Recent Adware Infections:
Most widespread Adware:
What is a Fake Antivirus?
Also Known As: Rogue security software or Scareware
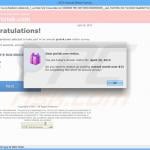
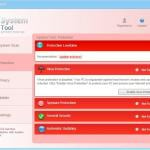
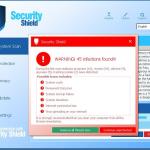
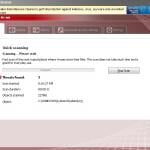
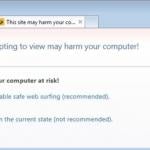
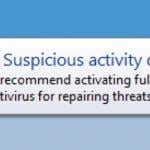
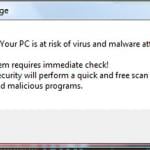
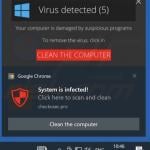
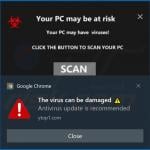
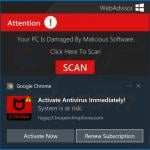
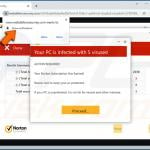
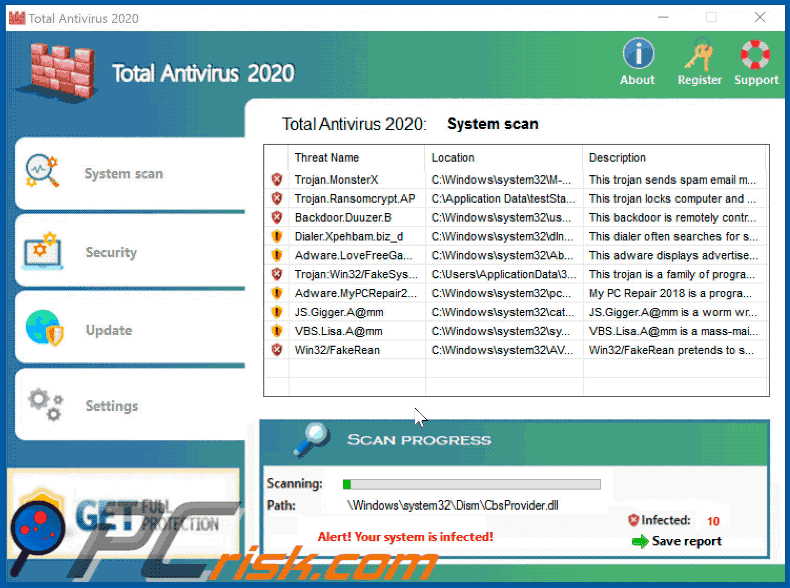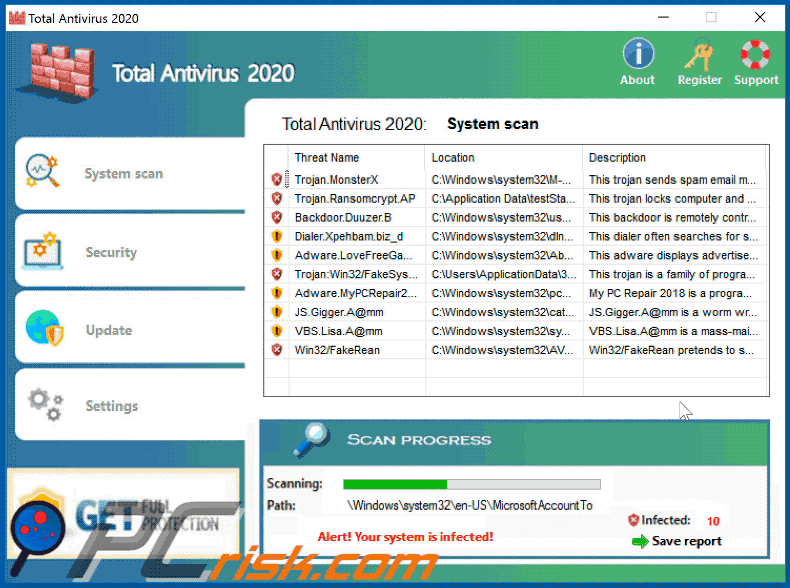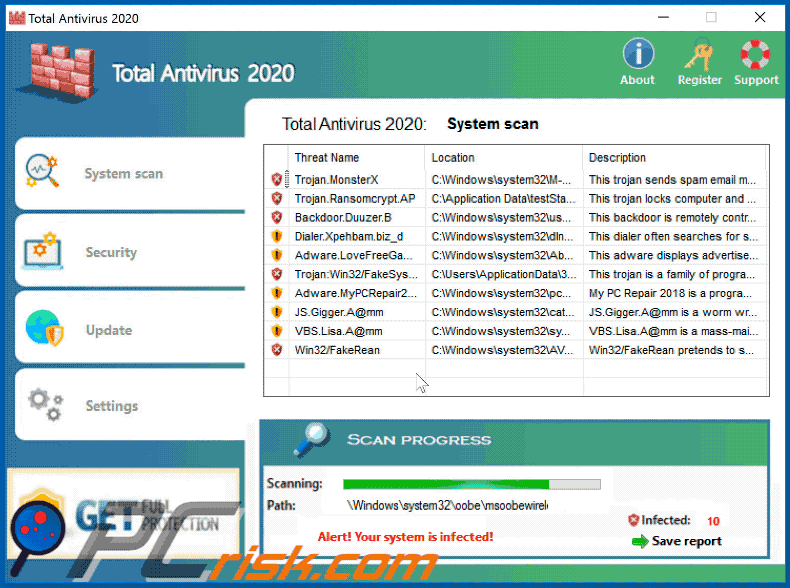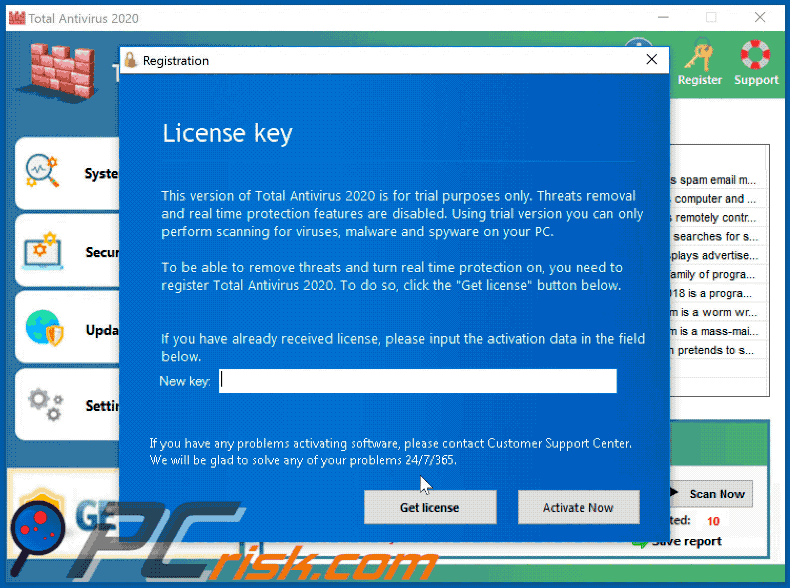
Fake Antivirus (also known as Scareware) is a term used to describe rogue security programs which imitate computer security scans and report non existent security infections to scare PC users into purchasing useless license keys. While such programs may appear beneficial on the surface, in fact they are misleading with the aim of tricking computer users into believing that their operating system is infected with high risk malware. Cyber criminals responsible for creating these bogus programs, design professional-looking user interfaces and security warning messages to make their fake antivirus programs appear trustworthy.
After successful infiltration, rogue antivirus programs disable the operating system's Task Manager, block execution of installed programs, and configure themselves to start automatically on system startup. PC users should realise that paying for a fake antivirus program is equivalent to sending money to Cyber criminals. Moreover, by paying for these rogue programs, users risk divulging their banking or credit card information, thus leading to potential further thefts from their accounts. Users who have already purchased such bogus antivirus software should contact their credit card company and dispute the charges, explaining that they have been tricked into buying a fake antivirus program. While the main function of fake antivirus programs is to encourage users to visit websites where they will be advised to pay for nonexistent security threat removal, these rogue programs are also capable of launching additional malicious programs, stealing personal information, and corrupting stored files.
Fake Antivirus Symptoms:
Constant security warning popup messages in the task bar, reminders to purchase a full version to remove supposedly identified 'security infections', poor computer performance, blocked execution of installed programs, blocked Internet access.
Screenshots of rogue antivirus programs generating fake security warning messages:
Distribution:
Cyber criminals use various methods to distribute rogue antivirus programs. Some of the most widely used are malicious websites, infected email messages, and fake online security scanners.
Other fake antivirus distribution methods:
- Search engine results poisoning
- Exploit payloads
- Fake antivirus downloads by other malware
- Fake Windows security updates
- Fake Facebook apps
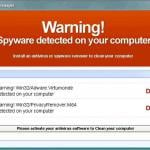
Screenshots of a fake online security scanners and messages used to proliferate rogue antivirus programs:
How to protect your computer from fake antivirus programs?
Always keep your operating system and all the installed programs (Java, Flash, etc.) up-to-date and be sure your firewall is turned on. Use legitimate antivirus and anti-spyware programs. Express caution when clicking links in email messages or on social networking websites. Never trust online pop-ups that state your computer is infected with malware, and then offer installation of security software that could supposedly eliminate 'identified' security threats - these online messages are used by Cyber criminals to spread fake security scanners.
Most recent Fake Antiviruses:
Most widespread Fake Antiviruses:
What is Ransomware?
Also Known As: Police Trojan, Computer-locking malware, crypto virus, file encrypter
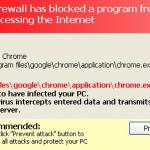
Ransomware is malicious software that locks users' desktops and demands the payment of a sum of money (the ransom) to unlock it. There are two major types of ransomware infections. The first exploits the names of authorities (for example, the FBI) and makes fake accusations of various law infringements (for example, for downloading pirated software, watching prohibited pornography, etc.) in order to trick computer users into paying a fine for supposed law infringements.
Cyber criminals responsible for creating these rogue programs, employ users' computer IP information to present their victims with a localized variant of a screen blocking message. Ransomware infections are distributed via exploit kits - malicious programs that infiltrate users' operating systems by exploiting security vulnerabilities in outdated software.
Another type of ransomware infection only effect users' Internet browsers (Internet Explorer, Mozilla Firefox, Google Chrome, and Safari), and is known as Browlock. This type of ransomware uses Java script to block users' attempts to close their Internet browsers.
Computer users should be aware that none of the legal authorities around the world use computer screen blocking messages to collect fines for law violations.
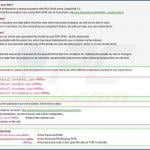
Screenshots of ransomware infections exploiting the names of various authorities:
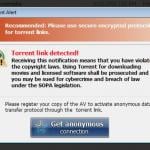
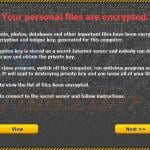
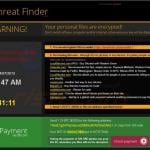
The second major type of ransomware infections are especially malicious, since they not only block users' desktops, but also encrypt data. This type of ransomware clearly states that it is an infection and demands payment of a ransom to decrypt users' files. This type of ransomware is relatively simple to remove, however, in the case of Cryptolocker, it is not possible to decrypt the files without the private RSA key. PC users who are dealing with this type of ransomware are advised to restore their encrypted files from a backup.
Screenshots of ransomware that encrypts users' files:
Ransomware Symptoms:
A completely blocked desktop with a message demanding paying of a ransom in order to unblock the computer (or decrypt files) and avoid criminal charges.
Distribution:
Cyber criminals often use exploit kits to infiltrate users' operating systems and execute the desktop blocking message. Exploit packs contain multiple exploits of different types, and if an operating system and installed software is not fully patched, causes the browser to download ransomware infections. Commonly, exploit kits are planted on malicious or hacked websites. Recent research shows that Cyber criminals are also proliferating ransomware infections through ad networks (which specialize in advertising on pornographic websites) and spam campaigns.
No More Ransom! project:

Victims of ransomware should know that it's not recommend to pay the ransom in order to get the decrypter from Cyber criminals. By paying the ransom you will be sponsoring Cyber criminal activity, moreover there are no guarantees that you will receive the decrypter. If you became a victim of ransomware please use No More Ransom! website to find more information about ransomware and potentially find a free decrypter for the ransomware that infected your computer.
How to avoid ransomware infections?
To protect computers from ransomware infections, users are advised keep their operating system and installed software up-to-date. Use legitimate antivirus and anti-spyware programs and do not click on links or open email attachments from untrusted sources. Avoid visiting pornographic websites and do not download files from P2P networks.
Most recent ransomware Infections:
Most widespread ransomware:
What is a Browser Hijacker?
Also Known As: Redirect Virus or Hijackware
A browser hijacker is a program that infiltrates users' computers and modifies Internet browser settings. Most commonly, browser hijackers modify users' homepage and default search engine settings and can interfere with the proper operation of the Internet browser itself. The main purpose of these bogus programs is to generate revenue from deceptive ads or sponsored Internet search results presented within the websites they promote. The most common forms of browser hijackers are browser extensions, toolbars, and helper applications. Browser hijackers infiltrate users' Internet browsers through drive-by downloads, infected email messages, or by installation of free software downloaded from the Internet.
Computer users should realise that, today, most free software download websites use download clients - small programs used to monetize their free services by offering installation of advertised browser plug-ins (usually browser hijackers in the form of toolbars). By not paying close attention to the downloading steps, users can inadvertently install various browser hijackers. Some of the adware capable of modifying browser settings is bundled with rogue browser helper objects able to block users' attempts to change their homage and default search engine settings.
Recent research shows that most browser hijackers redirect Internet users to deceptive Internet search engines. These engines return erroneous results with little or no relevance to the original search terms; the actions are performed to generate revenue from user clicks on sponsored search results - clicks that lead to sales-focused or malicious websites. Moreover, these bogus programs are known to track users' Internet surfing habits by recording various personal information (IP addresses, web sites visited, search terms entered, etc.), and such behavior can lead to privacy issues or even identity theft.
Screenshots of browser hijackers that change browser's homepage and default search engine settings:
Browser Hijacker Symptoms:
- Modified homepage and default search engine settings
- Blocked attempts to change browser settings
- Pop-up and banner ads in legitimate websites such as Google or Wikipedia
- Poor computer performance
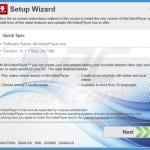
Screenshots of deceptive free software installers used in browser hijackers distribution:
Distribution:
Most commonly, browser hijackers are distributed using a deceptive software marketing method called bundling - they install with free software downloaded from the Internet. Adware capable of modifying browser settings is also known to be distributed using fake Java and browser update downloads.
How to avoid browser hijacker infections?
Always read the terms of use and privacy policy for any software that you download, and be especially careful when downloading free software. Do not click on pop-up ads that offer installation of free and 'useful' programs. Be very attentive when downloading and installing freeware: avoid installation of 'bundled' browser extensions by clicking on a 'decline' button; when installing free programs, use the 'advanced' or 'custom' installation options; and opt-out of installation of any bundled toolbars. In addition to these measures, ensure you keep your Internet browsers updated.
Most recent Browser Hijackers:
Most widespread Browser Hijackers:
What is a Trojan?
Also Known As: Email virus, spyware or DDos virus
A trojan (trojan horse) is a malware infections that is presented as a legitimate software. The name of this malware type originates from a story of Trojan War where Greeks constructed a wooden horse and hid their warriors inside. Trojans pulled the horse into their city as a victory trophy, soon after Greek warriors sneaked out of the wooden horse and opened the gate of Troy city allowing the Greek army to win the Trojan War. Similar to this story Cyber criminals make their malicious software appear as a legitimate program, for example a flash player. After computer users download and install what they think is a legitimate program they end up infecting their computers with a malicious code.
Cyber criminals are using various techniques to infect computer users. When it comes to Trojans most commonly Cyber criminals use email spam campaigns to distribute their malicious software.
Screenshot of a rogue email attachment that is used in Trojan distribution:
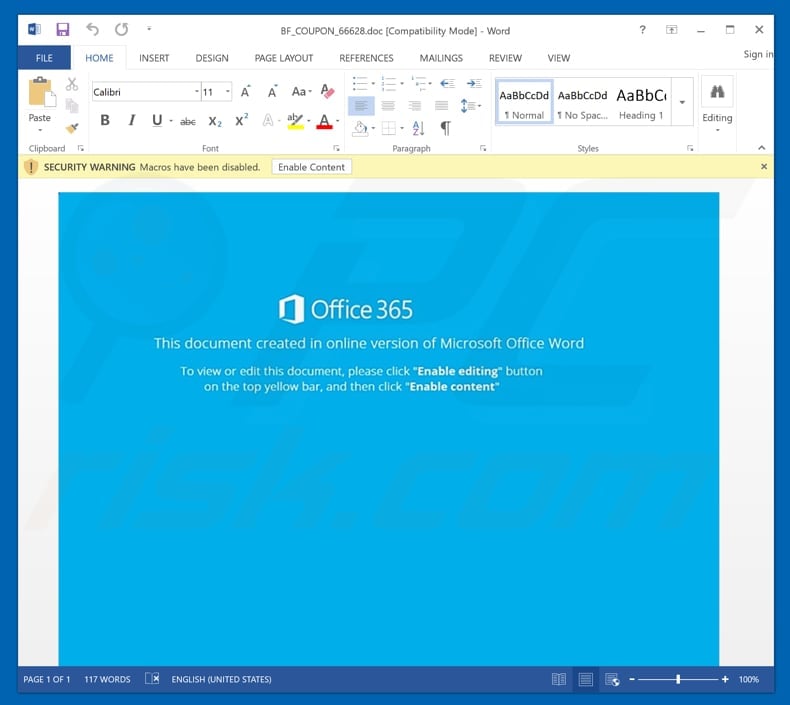
They send tens of thousands of emails pretending to be an invoice from a well known company. Such emails most commonly come with legitimate looking but malicious attachments. Users who fall for such trickery and open the attachment get their computers infected with a Trojan. As with real life criminal activity, Cyber criminals are distributing Trojans to gain monetary benefits. After infecting a computer Trojan can steal user's data (including sensitive banking information), control user's computer, download and execute additional malware on victim's computer. Generally Trojans can be split into several categories:
Backdoor Trojans - after infecting victim's computer, it creates a backdoor that allows Cyber criminals full access to user's computer. This type of Trojans are commonly used to steal user's Internet browsing data, infect victim's computers with additional malware and perform other malicious tasks.
Downloader Trojans - after infecting a computer it is used to download additional malware, for example this type of Trojan can download and execute a ransomware infection that encrypts user's files and asks for a ransom in order to decrypt them.
Infostealer Trojans - Trojans who fall under this category are designed to stealthily operate on user's computer without showing any signs of its presence. As the name implies this type of Trojans steal user's data, this can include banking information, social networking passwords, and any other sensitive information that can be used for stealing/making money in the future.
DDoS Trojans - Some Trojans are not interested in your personal data or infecting your computer with additional malware. DDoS trojans adds victim's computer to a botnet. When cyber criminals have a big enough botnet (hundreds or thousands of zombie computers) they can perform DDoS attacks on various websites or online services.
Trojan infection Symptoms:
Note that Trojan infections are designed to be stealthy - most commonly there are no symptoms on an infected computer.
- You see unfamiliar processes in your Tasks Manager.
- Your computer became slower that unusual.
- Your friends or colleagues receive emails/messages from you but you haven't sent them yourself.
Distribution:
Trojans can come in many forms. You computer can become infected with a Trojan after downloading legitimate looking software from some questionable website. Using services such as torrents. Downloading various software cracks or opening attachments from recently received emails.
How to avoid Trojan infections?
To avoid getting your computer infected by Trojans you should be very careful when downloading software - the only safe place to download applications is their developer website or official app store. Be very careful when opening attachments in your email inbox - even legitimate looking emails can be a part of social engineering created by Cyber criminals. Avoid using P2P services such as torrents and never use software cracks or game cheats - these are very common places where cyber criminals distribute their malicious software.
Most recent Trojans:
Most widespread Trojans:
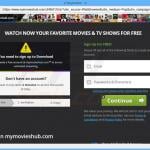
What is a Potentially Unwanted Application?
Also Known As: PUP (potentially unwanted program) or PUA
Potentially unwanted applications (also know as PUA or PUP - potentially unwanted programs) are applications that install on user's computer without proper consent. Programs that fall under this category are usually utility applications, various driver updaters, registry scanners and similar software. They install on user's computer using a deceptive marketing method called bundling. For example computer users downloads a flash player update and after a couple of minutes a new program pops up stating that various registry issues were found. After installation these programs tend to interfere with normal computer usage, they commonly add themselves to operating system's startup list and they tend to show various warning pop-ups and perform computer scans.
The main purpose of such applications is to trick computer users into believing that their computers are at risk (for example because of outdated drivers, or registry errors) and then to push them into purchasing a premium version of some application to fix the detected issues.
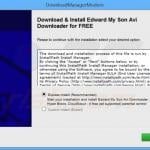
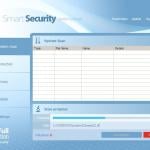
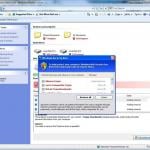
Screenshot of a typical potentially unwanted application:
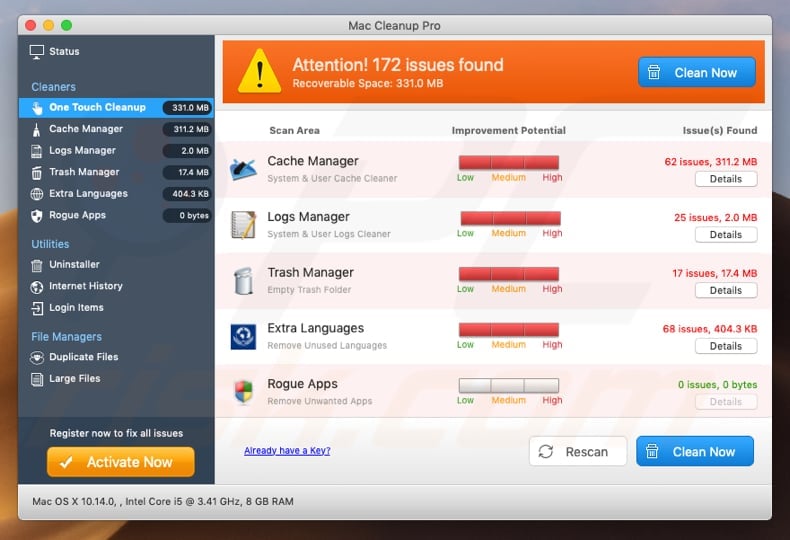
While usually potentially unwanted applications doesn't cause any serious threats to user's sensitive data the main issue with them is the fact that computer users can be tricked into purchasing a totally useless software. Note that registry issues or outdated drivers can't be viewed as a serious issues and applications that use various threatening graphs and colours to state otherwise are just exaggerating the situation to push computer users into making an unnecessary purchase.
Screenshot of a typical potentially unwanted application:
Potentially unwanted application symptoms:
- A program that you didn't install appeared on your desktop.
- An unfamiliar process appeared in your Tasks Manager.
- Various warning pop-ups are visible on your desktop.
- An unfamiliar program is starting that it found numerous registry issues and is asking for a payment to remove them.
Distribution:
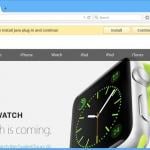
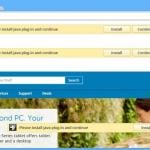
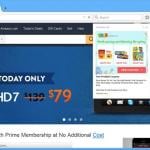
Potentially unwanted applications are usually distributed using a deceptive marketing method called bundling. In this scenario user is presented with a pop-up ad that is claiming that one's flash player is out of date. Then user is offered to download an update. The installer of the flash player is modified and the installation of various potentially unwanted application are hidden in the setup steps. Users tend to click "next" without attentively reading all the text in the modified setup. This ends up in a situation when apart from a flash player various unwanted applications are installed on user's computer.
Another common distribution channel is fake online virus scanners. In this case users are presented with a pop-up ad that imitates a computer scan. After a quick scan such pop-ups claim to have found various malware on user's computer and then insist of downloading some program that would supposedly eliminate the detected viruses. In reality none of websites can perform a computer virus scan - this is a trick used to fool computer users into downloading potentially unwanted applications.
How to avoid installation of potentially unwanted applications?
To avoid installing unwanted applications users should educate themselves on safe Internet browsing habits. In the majority of cases unwanted applications are distributed using social engineering tactics and trickery. One should download flash player, it's updates and other legitimate applications only from trusted sources (usually their developer's websites). Never trust online virus scans and other similar pop-ups that state about computer infections. When installing free software always pay close attention to the installation steps and click on all advanced or custom installation options - they can reveal installation of any additional unwanted software.
Most recent Potentially unwanted applications:
Most widespread Potentially unwanted applications:
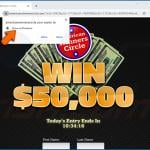
What is Phishing/Scam?
Also Known As: password stealer, pop-up scam
Phishing and various online scams are large businesses for cyber criminals. The word "phishing" originates from the word "fishing"; the similarity between these two words is that bait is used in both activities. When it comes to fishing, bait is used to trick a fish, and in the case of phishing – cyber criminals utilize some kind of bait to trick users into giving away their sensitive information (such as passwords or banking data).
The most common form of phishing is spam email campaigns, where thousands of emails are sent with false information; for example, emails claiming that the user's PayPal password has expired or that their Apple ID was used to make purchases.
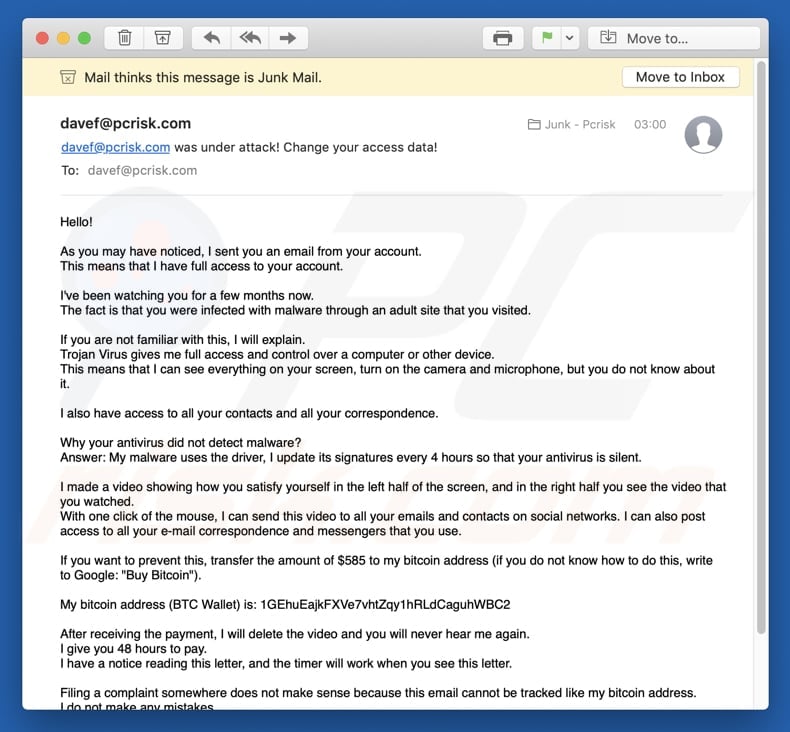
The links in such bogus emails lead to cyber criminal websites that are cloned from the original ones. Users are then tricked into entering their sensitive information into these fake pages. Later on, cyber criminals use the collected data to steal money or perform other fraudulent activities. Note that emails are not the only channel used in phishing attacks; cyber criminals are known to use text messages and phone calls to lure potential victims into giving away their personal information.
Sextortion scams are another popular form of fake emails. These claim to have compromising videos or photos of the user and demand that a ransom in Bitcoins (or other cryptocurrencies) be paid in order to remove the supposed sensitive material. Such emails usually state that a hacker had planted spyware on the computer and used it to record a video of the user watching pornography. In reality, cyber criminals don't have any compromising material. They are sending thousands of such bogus emails, and some users who receive them – believe the false information and pay the money.

Note that these are just a couple of phishing and online scam examples. Cyber criminals are always innovating and looking for new ways to steal sensitive information. Therefore, always be careful when browsing the Internet and entering your personal information. When it comes to phishing and scams – the best advice is to be skeptical; if something sounds too good to be true, it probably is.
Phishing/Scam symptoms:
- You received an email claiming that your password has expired or the account requires verification using the password.
- You received an email that is too good to be true (e.g., claiming that you won a lottery even when you didn't buy any lottery tickets).
- You received an email claiming that a hacker has recorded you watching pornography.
- You received an email claiming that you made a purchase that you do not recognize.
- You received a call claiming your PC or Mac is infected with viruses and needs cleaning.
Distribution:
Phishing attacks are most commonly executed through email spam campaigns. Cyber criminals are using various themes to lure their potential victims into giving away their information. Fake emails designed to steal sensitive data range from lottery winnings to expired passwords. In the case of online scams, cyber criminals often use misspelled domain names to trick users into visiting their fake websites. Another popular way of generating traffic to rogue websites is search engine poisoning techniques and various shady ad networks.
How to avoid becoming a victim of phishing and online scams?
If you have received an email claiming that you won a lottery or that you need to fill out some personal information for your bank – you should be very skeptical about such emails. Cyber criminals are using catchy subject lines and legitimate looking emails to trick computer users into becoming their next victims. Common sense and using antivirus software can significantly lower the chances of becoming a phishing email victim.
To avoid online scams, Internet users should always keep their browsers and operating systems up-to-date. Modern Internet browsers have built-in scam prevention filters, and they can protect you from visiting a dangerous website. As a second layer of protection, you should use a reputable antivirus program. The last and most important thing is to educate yourself on safe Internet browsing.
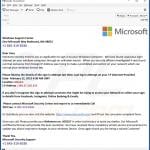
What is a Technical Support Scam?
Also Known As: tech support scam, pop-up scam
Technical support scam is a type where scammers claim to provide tech support services. Key features of these scams include phone calls and remote access software. Typically, victims are lured into calling (or otherwise communicating with) scammers via deceptive websites.
These pages often imitate legitimate sites or include graphics associated with genuine products, services, or companies – such as operating systems (Windows, Mac), antivirus software (Microsoft Defender, Norton, McAfee), electronics retailers (Geek Squad), and others. The scam websites often include various pop-up windows that run fake system scans or display threat alerts.
The goal is to convince victims that their computers are infected, blocked for security reasons, keep encountering critical errors, or are at great risk. These webpages offer technical support to aid victims with these nonexistent issues. Users are instructed to call the provided "helplines" to get tech support.
While the scam can take place entirely over the phone, these cyber criminals usually ask to access victims' devices remotely. The connection can be established using legitimate remote access programs like AnyDesk or TeamViewer.
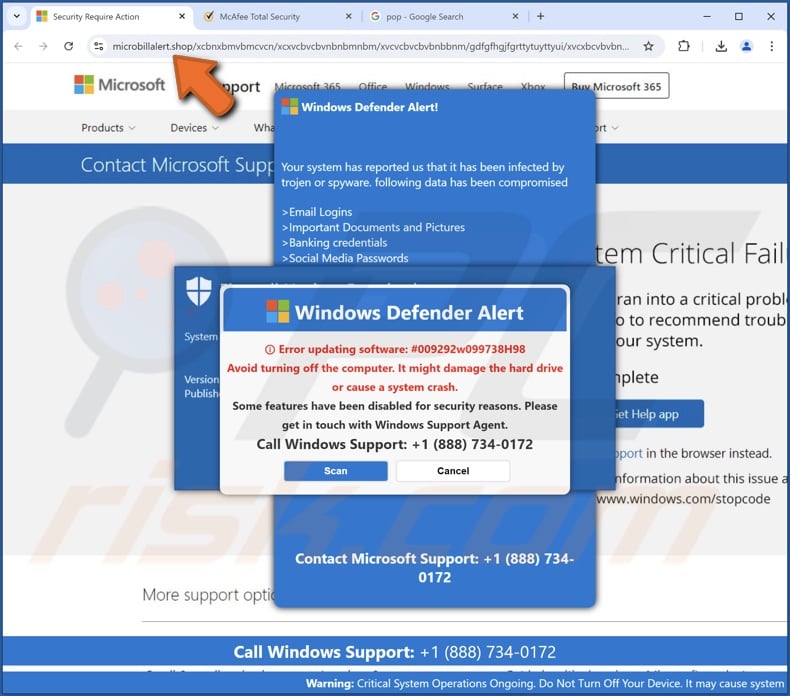
During the communication, scammers pretend to be professional support, commonly identifying themselves as "expert technicians", Microsoft or Apple "certified support", etc. In the initial stages of the scam, these cyber criminals perform activities meant to convince victims that they are providing the promised support services.
Scammers can use native Windows utility tools to create the illusion that the computer has been compromised. For example, they can use the Command Prompt to produce a rapid-fire output of files/directories and claim it to be a malware-scanning process. The criminals can also state that the output is suspicious and indicates that the system is infected.
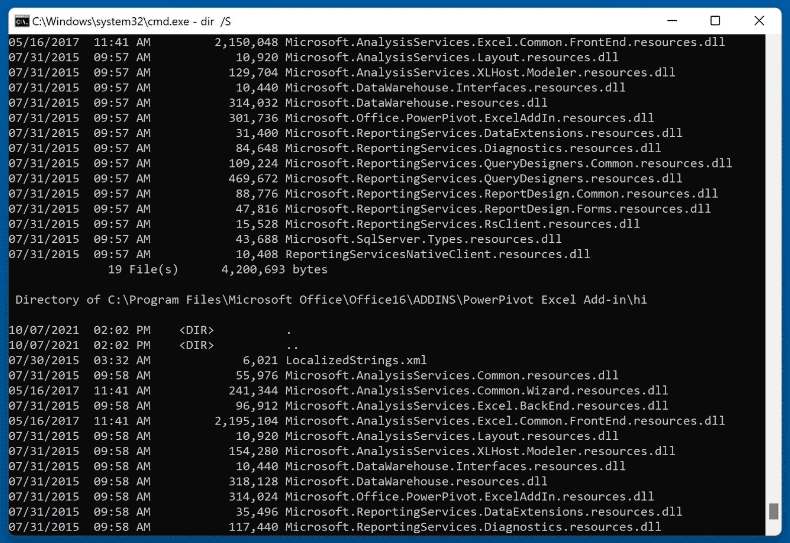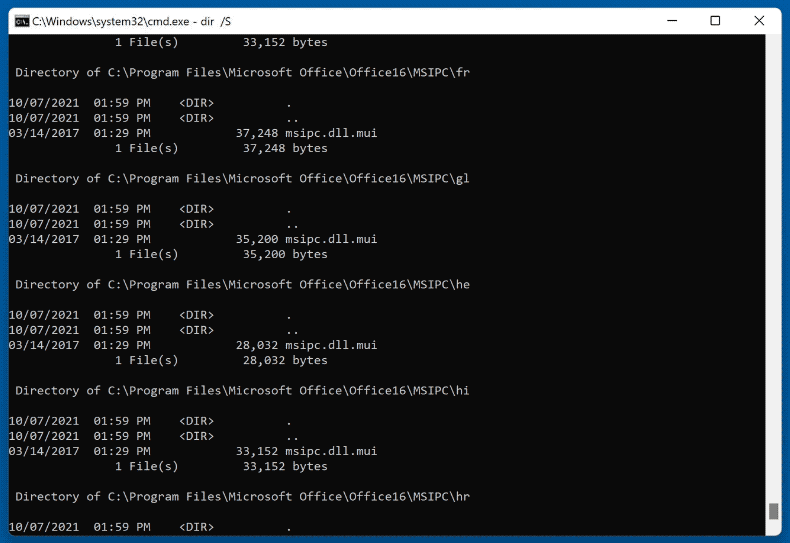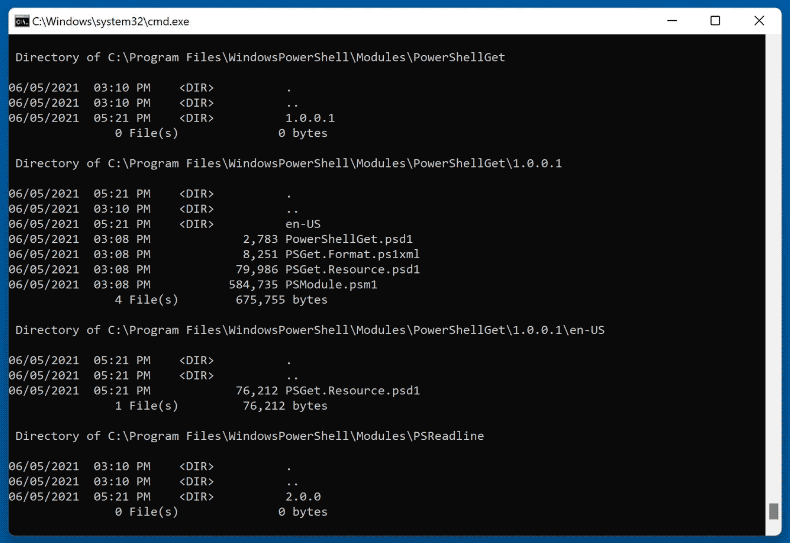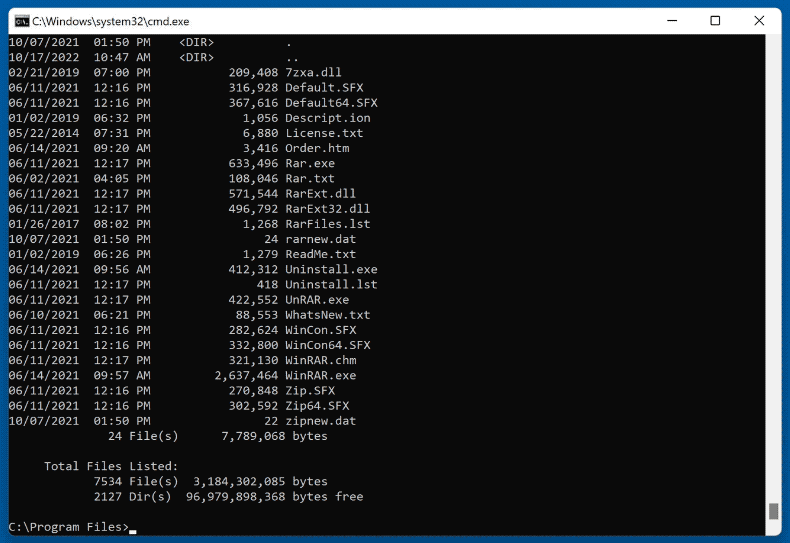
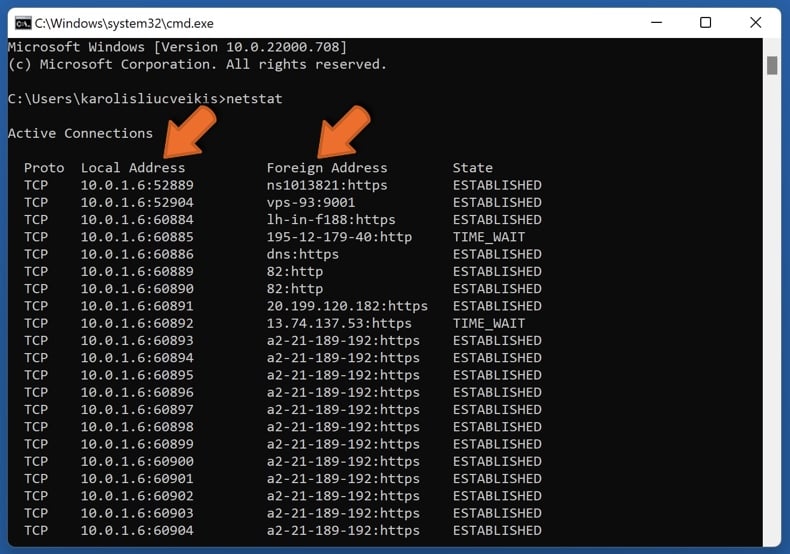
Another scare tactic that scammers may use is running the "netstat" command in Command Prompt. Once entered it basically presents users with network information listing connected local and foreign IP addresses. This is ordinary output; it is produced in the course of browsing the Internet.
The "Local Address" identifies the user's device, while the "Foreign Address" column represents the IP addresses of devices they have connected to (i.e., opened websites). Scammers re-invent the latter to mean hackers "connected" to the victims' computers.
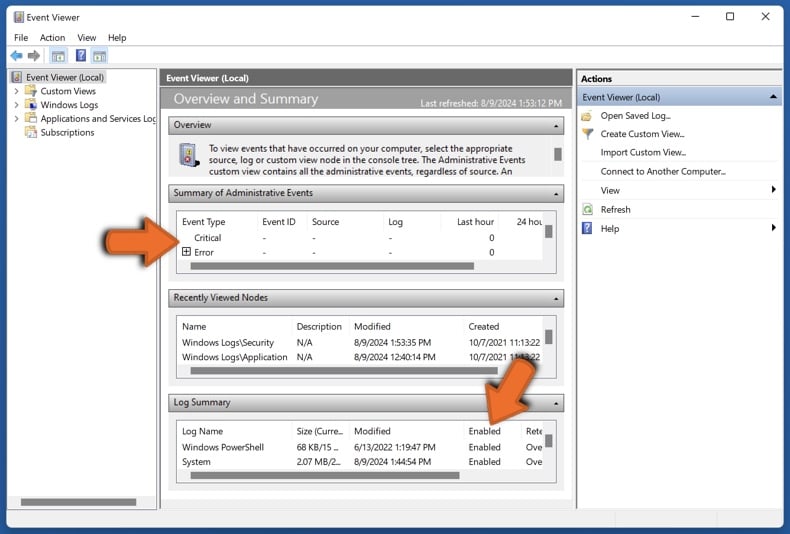
These cyber criminals can also use Event Viewer – a Windows component that allows users to view event logs and troubleshoot issues. The log entries are likely to include a variety of largely innocuous alerts concerning errors and disabled services (note that not all must always be enabled). Scammers claim that this harmless information is an indicator of system compromise.
Scammers can use third-party software to create the illusion of malware infections. Fake antivirus tools are often utilized for this purpose. These programs perform hoax system scans that detect multiple viruses on devices. This rogue software may require payment to activate their functionalities (like malware removal), yet remain nonoperational after purchase. More information can be found in the "Fake AntiVirus" section on this page.
The end goal of all scams is profit, and scammers can achieve it in various ways. In many cases, technical support scammers seek funds directly. Once victims are convinced that their computers are infected, criminals ask them to pay for the malware removal, software activation, subscription renewal, etc.
Scammers aim for large amounts – in the hundred and thousand ranges. They commonly offer years-long or even lifetime protection. Not only is this a lure for obtaining significant sums of money, but it can also allow cyber criminals to contact victims at their leisure and proclaim the detection of new threats or issues, which naturally necessitate additional payment to eliminate.
Tech support scams can be long and outdrawn, wherein the scammers keep constant contact with their victims and lead them through each step of the process. These criminals can attempt to establish a personal connection and use a variety of hoaxes to create an impression of legitimacy, such as giving bogus security codes and IDs.
In most cases, scammers request that the payments be made in gift cards or cash. In case of the former, cyber criminals can keep contact with the victims and instruct them on what to say to the store employees if they question the excess purchase (as it may be known by sellers that scammers seek gift cards). Once a gift card is redeemed, it cannot be refunded – hence, victims cannot retrieve their spent funds after the redemption codes are disclosed to scammers.
Cyber criminals can instruct victims on how to hide cash in innocent-looking packages and then ship them. In large-scale tech support schemes, the criminals may even have a ring of "mules" for delivering parcels between countries. Ordinarily, this method of fund acquisition allows for no money recovery options.
Bank transfers and cheques are used to a lesser extent, as there may be options for victims to retrieve their funds, security measures that impede international scammers, and they are far more traceable. Cryptocurrency is likewise uncommon; while it makes fund retrieval practically impossible, obtaining and sending digital currency can be a process too complex for the targeted victim demographic that tends to skew toward the advanced elderly.
However, there is a host of threats associated with technical support scams. Cyber criminals can target sensitive information, such as account log-in credentials (e.g., emails, social networking, e-commerce, money transferring, online banking, digital wallets, etc.), personally identifiable details (e.g., passport scans/photos, ID card details, etc.), and finance-related data (e.g., banking account or credit/debit card numbers, etc.).
Targeted information can be acquired by tricking victims into disclosing it over the phone, typing it where scammers claim they cannot see it, or entering it into phishing websites or files. Phishing sites/files can be competently disguised as account sign-in pages or registration/payment forms.
These criminals may use the feature of the remote access software to darken victims' screens or overlay them with images (e.g., threat warnings, Blue Screen of Death error, etc.). While victims cannot view their device screens, scammers can perform various malicious activities on the machines.
Cyber criminals can browse and steal valuable content, disable/uninstall genuine security tools, or install real trojans, ransomware, and other malware (more information on these programs can be found in the appropriate sections on this page). What is more, specific malware and certain remote access programs can enable cyber criminals to access victims' computers without the latter's knowledge and consent.
While scammers try to maintain the guise of professional tech support with the previously described scare tactics, they are not above resorting to coercion and threats. They can threaten or outright delete victims' files if they refuse to pay. In Windows versions preceding Windows 10, these criminals often used the Syskey utility to add a password to victims' devices – thus locking them out until the demands are met. As Syskey has been removed from Windows 10 and later versions, some scammers rely on third-party software that they install on victims' computers for this very purpose.
Cyber criminals can also resort to psychological abuse and bullying tactics, such as constantly calling at all hours, yelling, and verbally abusing uncooperative victims. There have even been cases where scammers resorted to threats of physical violence and grievous bodily injury.
Distribution:
In most cases, technical support scams rely on deceptive websites that use threat-related lures to trick visitors into calling their fake support lines. These pages can be force-opened by sites that utilize rogue advertising networks, either immediately upon initial access or when hosted content is interacted with (e.g., clicking buttons, text input fields, ads, links, etc.).
Intrusive advertisements and spam notifications are known to promote these scam webpages as well. Typosquatting (misspelled URLs) and search engine poisoning techniques can also be implemented to endorse these sites. Another method is relying on spam emails or other deceptive messages, which lead recipients to scam sites or invite them to call the scammers directly. Cold-calling and robocalls are used as lures as well.
How to avoid becoming a victim of technical support scams?
Caution is key to online safety. Be mindful when browsing and do not visit websites of ill repute. Do not click advertisements and notifications that make suspicious claims regarding your computer safety. Most modern Internet browsers have measures that prevent access to malicious websites, but additional security tools (such as antiviruses and specialized browser extensions) can increase the protection.
Nonetheless, if you happen upon a webpage running system scans and detecting viruses (a feat no website can achieve) – ignore and close it. Should it be impossible to close, end the browser's process (using Task Manager or the Activity Monitor on Mac). When reaccessing the browser, start a new browsing session, as restoring the previous one will reopen the deceptive page.
Approach incoming communications (e.g., emails, calls, SMSes, DMs/PMs, etc.) with caution. Do not trust messages from unknown or suspect sources, and do not comply with instructions provided by email/call that alert you of system infections or outdated services/products that you have not purchased in the first place.
If you have fallen victim to a tech support scam – disconnect your device from the Internet, uninstall the remote access software used by the scammers, perform a full system scan with a reputable antivirus, and remove all detected threats. Contact the appropriate authorities if you suspect that your private information has been exposed.
What is a Refund Scam?
Also Known As: overpayment scam
Refund scam is a type wherein victims are deceived into sending scammers money with the activity disguised as a refund process or other financial compensation. These scams involve direct communication with victims, usually via phone calls.
Initial contact is most commonly made via cold calls or spam messages (emails, SMSes, PMs/DMs, etc.). Lures center on refunds, invoices, subscription renewals, and similar. The key theme is the implication that funds were removed from the victim's account, but the charge can be reversed (i.e., refunded).
If the scam begins with a call, scammers typically identify themselves as support of a well-known company or service provider, and if the initial lure is a message (like an email), it is presented as an invoice or alert from a genuine entity. For example, the supposed charge can be a purchase made from an e-commerce platform (Amazon, eBay) or a subscription renewal for a product/service of a prominent company (Microsoft, Apple, Norton, McAfee, Netflix).
The scam depends on the sincerity of the victims. During the fake refund or charge/subscription cancellation process, scammers claim that a significantly larger sum was transferred and plead for the return of the excess funds – thus, victims are tricked into sending their own money to cyber criminals.
Refund scams involve scammers accessing victims' devices remotely. Legitimate remote access programs like TeamViewer or AnyDesk can be used to facilitate the connection. The use of such software is critical when it comes to convincing victims that excess funds were transferred into their accounts.
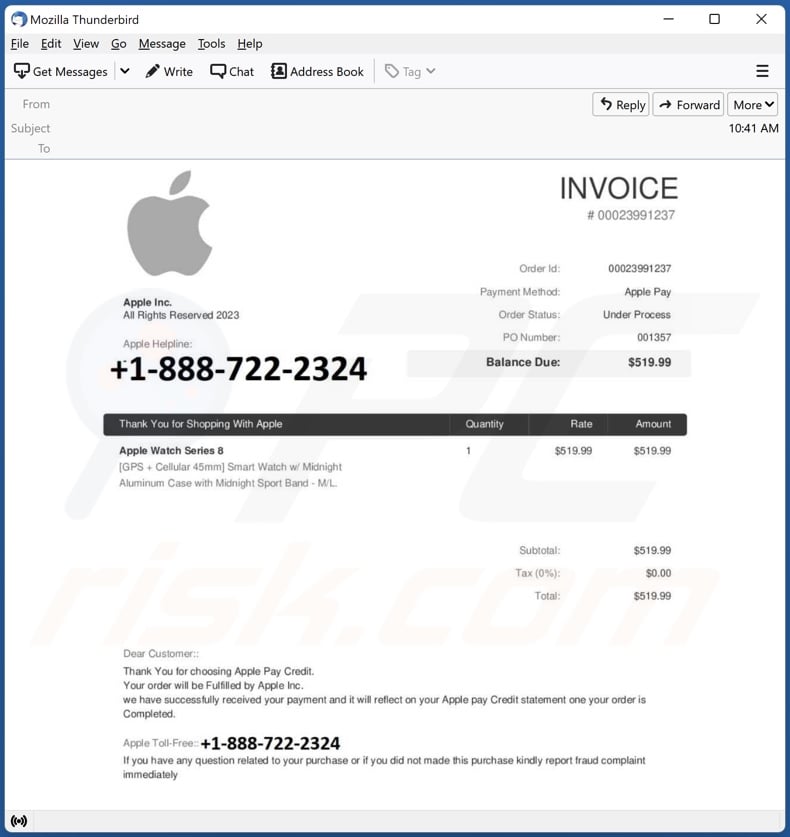
Once the remote access is established, scammers request victims to sign into their online banking accounts in order to aid them with the refund process. Writing a bogus refund request may be an element of the scam. These cyber criminals rarely bother creating legitimate-looking documents/webpages for victims to fill out. Instead, they can open a text editing program, such as Windows Notepad, and ask victims to enter their information – crucially, the supposed refund amount. The purpose is to trick victims into believing they are in control of the process.
Before the refund amount is typed into the text editor, scammers utilize a functionality of the remote access software to either darken the screen or overlay it with an image – thereby rendering victims incapable of seeing what is happening. Meanwhile, scammers attempt to create the impression that victims made an error when entering the sum, thus having a significantly larger amount transferred to them.
Two methods are used to craft this deception. Cyber criminals can move funds between victims' accounts, such as from "savings" to "checking". Most online banks do not restrict this activity; it is instantaneous, as the money is not actually leaving the owner's account. Carrying out a transfer to a different account (e.g., one in the scammers' possession) is not a swift process. There are security measures in place, transfers likely require verification (which would need additional actions from victims), and these transactions could be easily traceable and reversible.
Therefore, cyber criminals do not transfer money to themselves in this fashion. Instead, scammers rely on deception to get victims to do it in a manner that would leave them safer from criminal prosecution and diminish the possibility of fund retrieval.
The other technique is using Web development tools (DevTools). These tools are integrated into many browsers – hence, scammers do not need to download/install any additional software. DevTools are used by web developers to view, test, and modify websites. In case of refund scams, they are used to change the appearance of a webpage by editing its HTML code.
Hence, the sums indicated in victims' bank account pages are changed to appear larger. Editing the HTML merely affects the appearance of a website; it does not actually change the site or – in this case – the bank account and the money therein. This appearance modification is easily reversed by refreshing the page.
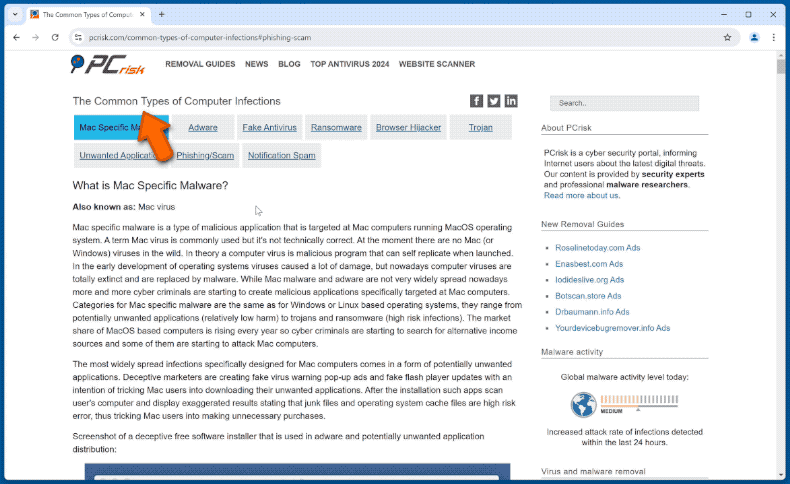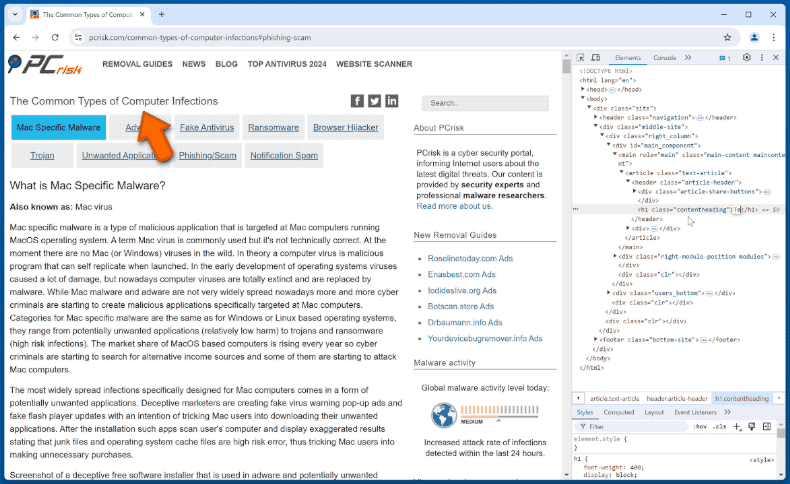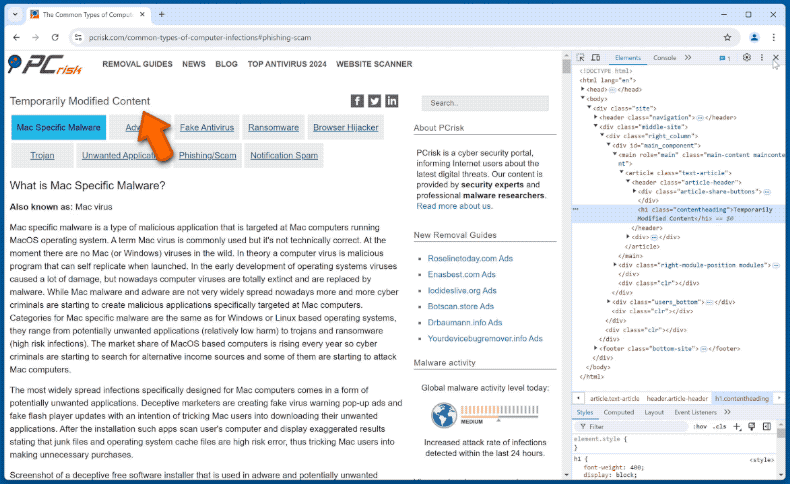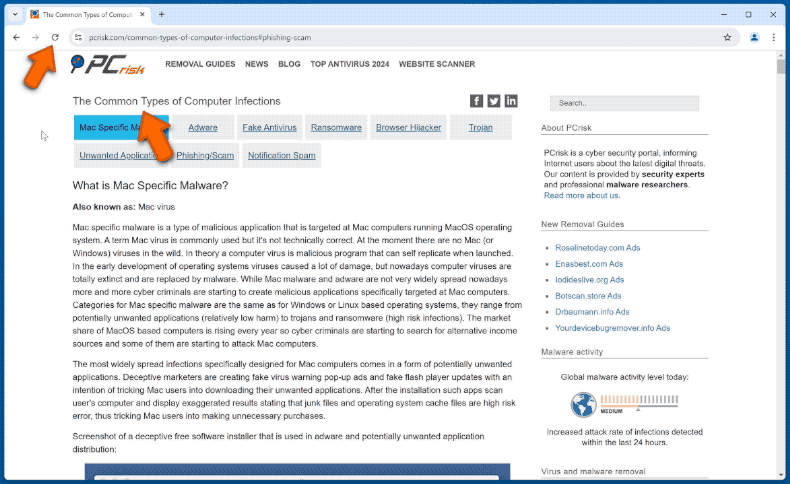
It must be emphasized that neither of the methods used by refund scammers impact victims' accounts and funds; they only create an appearance that a transfer has occurred. When cyber criminals finish creating this deception, they return the screen view to their victims and proclaim that they made a mistake when entering the amount they were entitled to receive.
Victims are confronted with their bank accounts that "confirm" this claim, and scammers beg them to return the excess. It is a play on guilt since victims are blamed for this error. Scammers can plead and state that this will get them fired from the job that they so desperately need. If the guilt-tripping does not prove effective, victims can be threatened with legal repercussions for keeping the money or otherwise intimidated into complying.
Refund scams have considerable overlap with technical support scams; they share the same risks associated with unauthorized remote access and the techniques used to obtain victims' funds. More can be read on this page in the "Technical Support Scam" section.
How to avoid becoming a victim of refund scams?
Approach incoming calls, emails, SMSes, PMs/DMs, and other messages with caution. Do not trust suspicious communications concerning purchases you have not made or services you have not subscribed to in the first place. Do not open links or attachments present in dubious/irrelevant mail.
If you have any concerns about unauthorized access to your accounts or other worries, always contact the appropriate channels found via legitimate sources (e.g., support numbers/emails/etc. provided by official websites).
Most recent Scams:
Most widespread Scams:
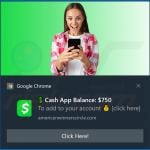
What is browser notification spam?
Also Known As: push notification ads, website notification ads
"Browser notifications" is a useful feature provided by all major Internet browser developers (Chrome, Firefox, Safari). Website owners can use this feature to show notifications about prevailing news, discounts, etc. When visiting a website, users are asked if they want to allow such notifications, and if they do so, website operators can send browser notifications to the open-in users.
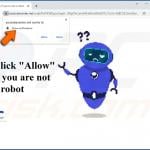
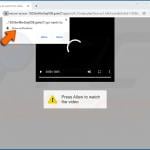
Unfortunately, cybercriminals exploit this feature to generate revenue by bombarding Internet users with spam notifications that lead to fake antivirus scams, gambling, and other shady websites. To trick Internet users into allowing browser notifications, Cybercriminals create pop-up windows with false claims, for example, "In order to access content click allow", "Click allow if you are not a robot", "Click allow to continue watching", etc.
Symptoms that you were tricked into allowing spam notifications:
Notifications ads constantly appear in the right lower corner of your desktop (Windows users). Mobile users see such notifications at the top of their screen. Mac users see notification ads in the top right corner of their desktop.
Examples of browser notification spam:
Distribution:
Deceptive marketers create lure websites that trick Internet users into allowing website notifications. When browsing the Internet, users get redirected to such sites or see pop-up ads of mentioned websites and are deceptively lured into clicking "allow".
Examples of websites used for tricking Internet users into allowing spam notifications:
How to avoid browser notification spam?
Internet users should be very skeptical when asked to allow notifications - legitimate websites don't force their users into allowing notifications. If you are asked to prove that you are not a robot by clicking allow - don't do it, it's a scam. Only allow notifications from websites that you fully trust.
Most recent Browser Notification Spam:
Most widespread Browser Notification Spam: