Shlayer tricks Apple
Upon the release of macOS Mojave, Apple implemented another layer of security intended to protect its users. The tech giant introduced the concept of Notarization, which involves developers adhering to a number of steps to make sure their apps are malware-free. Upon the release of macOS Catalina, this process became mandatory for developers looking to release apps on the new release. In theory, the idea seems solid enough and will protect macOS users. In reality, things appear to be far more complicated. The malware developers behind the Shlayer malware seem to have subverted this process in order to authenticate the one thing the concept is meant to prevent, malware.
According to reports by both Bleeping Computer and MalwareBytes the malware’s developers successfully managed to get their malicious payloads through Apple's automated notarizing process. Before the details of how the malware developers managed to do, it is wise to look at how Apple set up the process to work in the first place. According to Apple the process became obligatory from the start of February 2020. The process itself goes hand in hand with the concept of code-signing which is a cryptographic process that enables a developer to provide authentication to their software. It both verifies who created the software and verifies the integrity of the software. By code signing an app, developers can prevent it from being modified maliciously, at least in theory that is. In practice, it makes such modifications easily detectable.
Code signing has been standard practice for several years already, however, the issue that emerged had to deal with Mac software released outside of the app store did not require code signing. Rather developers had to buy a certificate from Apple for 99 USD. This meant that malware authors could merely buy the certificate and authenticate their malware. Of course, when the malware is discovered Apple can revoke the certificate rendering the malware useless. However, malware can remain undetected for years, the FruitFly malware is just one example, and once detected the damage might already have been done.
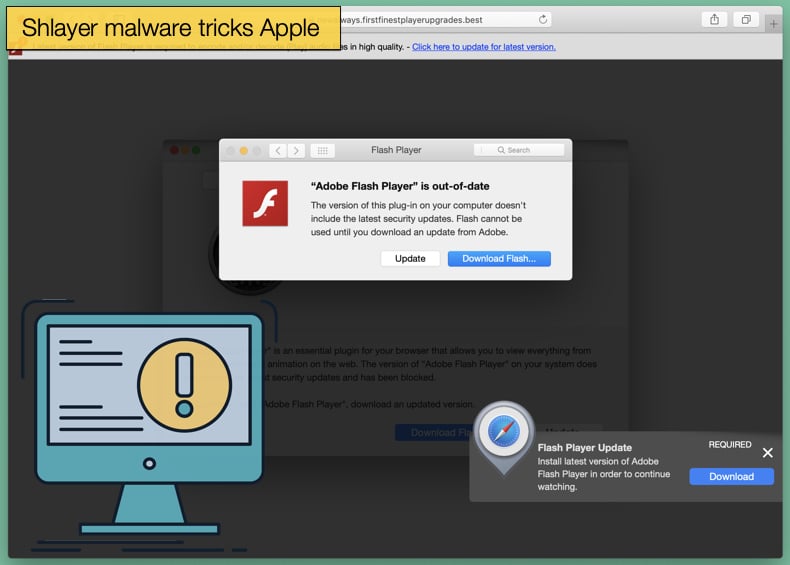
Thus another layer of security was needed to prevent the above situation from occurring time and again. Apple’s response to this was Notarization, which dictates that developers must submit their software to Apple. The exact measures employed by the tech giant to authenticate the software are not exactly known but it is assumed the software is processed through an automated verification process. Once notarized it can be opened and run by users, if the software fails the process it cannot be opened.
Questions about Effectiveness
When Patrick Wardle, a Mac security specialist, discovered samples of the Shlayer malware that had been notarized, some difficult questions need to be answered. As to the exact details on how the malware developers managed to slip malware past a process meant to prevent this from happening are thin on the ground. Thomas Reed, a security researcher with Malwarebytes, believes the malware developers had to do very little. When looking at the images pertaining to the compromised installer used to distribute the malware, there is no difference between easily discernible between notarized samples and others. The code of the notarized samples and the non-notarized samples show differences but these appear to minor at best. Reed noted,
“It’s entirely possible that something in this code, somewhere, was modified to break any detection that Apple might have had for this adware. Without knowing how (if?) Apple was detecting the older sample (shown on the right), it would be quite difficult to identify whether any changes were made to the notarized sample (on the left) that would break that detection. This leaves us facing two distinct possibilities, neither of which is particularly appealing. Either Apple was able to detect Shlayer as part of the notarization process, but breaking that detection was trivial, or Apple had nothing in the notarization process to detect Shlayer, which has been around for a couple of years at this point.”
While Apple has not revealed how it notarizes software submitted for the process, many developers can attest to the fact that the process is fast. In some instances, developers received emails stating their submissions had been notarized minutes after making the submission. This would certainly imply that there is no human intervention in the process and it is solely automated. Whether the discovery of the Shlayer samples will do anything to change this process in any discernible way in the future is in doubt. As Thomas Reed concludes,
“Apple wants you to believe that their systems are safe from malware. Although they no longer run the infamous “Macs don’t get viruses” ads, Apple never talks about malware publicly, and loves to give the impression that its systems are secure. Unfortunately, the opposite has been proven to be the case with great regularity. Macs—and iOS devices like iPhones and iPads, for that matter—are not invulnerable, and their built-in security mechanisms cannot protect users completely from infection.”
The Shlayer Trojan
In January 2020, Kaspersky Labs published a report detailing Shlayer. Researchers discovered that the malware was responsible for one in ten of our Mac security solutions encountered this malware at least once, and it accounts for almost 30% of all detections for this OS for the previous year. Researchers first discovered samples of the malware in February 2018, up until the date the report was published Kaspersky researchers had collected almost 32,000 different malicious samples of the Trojan and identified 143 command and control server domains. This information would blow any counter argument by Apple that it was unaware of the malware out of the water.
It is not only MalwareBytes and Kaspersky Labs that have encountered Shlayer. In 2019, Carbon Black discovered a new variant of the malware. The new variant would look to disable Gatekeeper’s protection mechanism in order to run numerous other payloads. According to the researchers,
“After the second stage payload is downloaded and executed, it attempts to escalate privileges with sudo using a technique invoking /usr/libexec/security_authtrampoline as discussed in Patrick Wardle’s DEFCON 2017 talk “Death by 1000 Installers”. Once the malware has elevated to root privileges, it attempts to download additional software (observed to be adware in the analyzed samples) and disables Gatekeeper for the downloaded software using spctl. This allows the allowlisted software to run without user intervention even if the system is set to disallow unknown applications downloaded from the internet. Furthermore, many of the payloads contained within the second stage download are signed with a valid developer ID…”
For the most part, the malware’s modus operandi has remained fairly static. Like numerous other malware strains that target Mac, the malware masquerades as an Adobe Flash Installer. Initially, older variants of the malware were pushed to users via torrent downloads with the malware developers looking to take advantage of users looking to download or stream popular television shows or live sport. Now, more modern variants are spread via fake update pop-ups shown to potential victims on hijacked domains or clones of legitimate sites, or as part of far-reaching malvertising campaigns on legitimate websites.
After it infects a Mac, Shlayer will install the mitmdump proxy software with a trusted certificate. This allows the malware to analyze and modify HTTPS traffic, allowing it to inject ads web pages, monitor the victims' browser traffic, as well as to inject malicious scripts into visited sites.
The malware has one more surprise for victims. Not only can the malware analyze HTTPS traffic but also encrypted traffic related to online banking and secure email applications. Besides deploying the traffic monitoring proxy on compromised machines, Shlayer's authors are currently only deploying adware as a secondary payload but they can switch payloads at any time to drop more dangerous malware strains like ransomware or wipers. This ability to drop payloads that go far beyond the annoyance of adware to financially damaging malware should have macOS users more than a little worried. Slowly the myth that Apple products were all but invulnerable to the whims of hackers is being eroded but not fast enough. It is advised, like with those using Windows, that users have a recommended macOS compatible security suite.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion