Mount Locker Ransomware Targets Tax Season
Those behind the Mount Locker ransomware are looking to ruin an already stressful time for some, the tax return season. The ransomware strain is actively looking to target file extensions used by TurboTax, a software package developed to help US users with their tax returns. Mount Locker is a relatively new ransomware strain, first spotted in July 2020. Like many of the newer ransomware strains, they have been quick to adopt human-operated ransomware tactics, that made Maze, Ryuk, and Sodinokibi so devastating. These tactics have come to include threatening, and in many cases, releasing data stolen by the attackers before encryption occurs.
Like those who have gone before Mount Locker, the ransomware’s operators have a dedicated leak site which they use to announce victims and release data if the ransom is not paid. The lasts version of the ransomware discovered by Vitali Kremez appears to target the following TurboTax file extensions, .tax, .tax2009, .tax2013, and .tax2014. Given that many are gearing up to submit tax returns due by April 2020, it is believed that by targeting these files the attackers can place increased pressure on victims to pay the ransom.
Speaking to Bleeping Computer Vitali Kremez explained that while it may seem odd to target specific tax years, like 2009 and 2014, the ransomware would target all extensions containing the string “tax”. To prevent losing all-important tax data if you are a TurboTax user it is recommended that you back up all data to a removable device like a USB drive daily. If the worst were to happen then at least late tax return fines can be avoided.
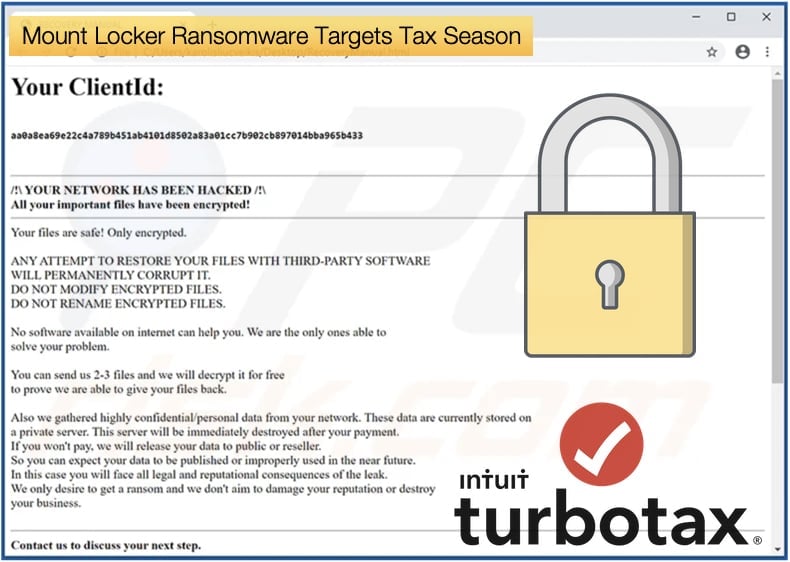
While being active since July 2020, it was only until very recently that security researchers were able to get their hands on a sample. As discovered by MalwareHunterTeam the first researcher to analyze sample appears to be Michael Gillespie. According to Michael’s analysis, the ransomware uses ChaCha20 to encrypt the files and an embedded RSA-2048 public key to encrypt the encryption key.
According to Bleeping Computer’s analysis when encrypting files, the ransomware will add an extension in the format .ReadManual.ID. In practice, the extension added will look like 1.doc.ReadManual.C77BFF8C. The ransom note is named RecoveryManual.html and contains instructions on how to access the Tor site to communicate with the ransomware operators. Unfortunately, the ransomware is secure and there is currently no way of decrypting files using a decryptor, leaving victims to restore from backups or pay the ransom.
Mount Locker demands Millions
As mentioned above Mount Locker was quick to adopt the tactics of today’s most successful ransomware strains including leak websites and targeting corporate networks. Another thing copied is ransom demands in the millions of USD. As the analysis was being done by security researchers’ victims were being added by the ransomware’s operators. From ransom notes and communication with the operators shared with several publications, ransom demands are in the millions, in one instance 2 million USD was demanded to decrypt files. The demands included the now-standard practice of threatening to leak the data if no payment is received. In one instance, 400 GB was stolen from a victim, with the attackers demanding the ransom be paid otherwise the data would be leaked to the victim’s competitors. The ransom was not paid, and the data was leaked. By the end of September, there were four victims named on the data leak site with one having their data leaked.
Since then several other companies, including health care providers have fallen victim to Mount Locker. However, perhaps one of the first victims of note occurred in August 2020 when the gang targeted Engineering and Technology giant ThyssenKrupp. The company fits the modus operandi of a human-operated ransomware gang as the company is a German multinational conglomerate and with 670 subsidiaries worldwide it is one of the world’s largest steel producers. The company is based in Duisburg and Essen. One of their subsidiaries ThyssenKrupp Marine Systems manufactures frigates, corvettes, and submarines for the German navy as well as other navies around the world. To prove their claims Mount Locker released 30 MB of data, at the time the data would be sold for 35 Bitcoin which is more than 600,000 USD at the time of writing.
Also, in August one of Sweden’s largest security firms fell victim to Mount Locker. Gunnebo AB, which is one of the leading providers of banking security solutions in Europe, including safe storage, cash management, ATMs, and entrance control systems. The company's CEO Stefan Syrén, revealed that the company suffered an attack from Mount Locker Operators. In an official statement, Syrén stated,
“Of course, we have been aware that files that originate from us are available on Darknet, and we naturally regret that this is the case. Unfortunately, this is exactly how computer criminals work… Therefore, I would like to emphasize that it has never been an alternative for Gunnebo to pay a ransom to have the files deleted. The only way to curb this kind of crime is that the affected organizations do not fall short and payout ransoms.”
According to Christopher Krebs,
“In March 2020, KrebsOnSecurity alerted Swedish security giant Gunnebo Group that hackers had broken into its network and sold the access to a criminal group which specializes in deploying ransomware. In August, Gunnebo said it had successfully thwarted a ransomware attack, but this week it emerged that the intruders stole and published online tens of thousands of sensitive documents — including schematics of client bank vaults and surveillance systems.”
It is not unheard of for companies to fall victim to ransomware attacks in quick succession, however other details suggest that the reported Mount Locker incident may date back to the March incident, meaning that the operators have been active for far longer. By corroborating evidence from official statements and Swedish new releases, Krebs concluded,
“Five months later, Gunnebo disclosed it had suffered a cyber attack targeting its IT systems that forced the shutdown of internal servers. Nevertheless, the company said its quick reaction prevented the intruders from spreading the ransomware throughout its systems, and that the overall lasting impact from the incident was minimal.”
Why is ransomware still effective?
Since the two incidents mentioned above, the Mount Locker operators have gone on to claim the scalp of Sonoma Valley Hospital in California. For many readers, this may beg the question as to why ransomware is still so effective. The answer as with all things is more complex than we give it credit for. In attempting to answer the question, the answer might lie in the pressure and security challenges faced by organizations in 2020. From COVID-19 to down-turned economies, and workers being forced to work remotely, business leaders have a lot on their plate. For those tasked to defend networks, this pressure has resulted in more security concerns, in particular, the fast adoption of remote working has left many gaps in organizations defenses.
Checkpoint reported that in the third quarter of 2020 they saw a spike of 50% in daily ransomware attacks when compared to the first half of the year. Another shocking stat was that Ryuk attacks amounted to 20 a week for the period. In looking explain what was driving the increase researchers noted,
“The current pandemic has forced organizations to make rapid changes to their business structures, often leaving gaps in their IT systems. These gaps have given cybercriminals the opportunity to exploit security flaws and infiltrate an organization's network. Hackers will encrypt hundreds of thousands of files, incapacitating users and often taking whole networks hostage. In some cases, organizations simply prefer to pay the price instead of dealing with encrypted files and recovering their IT systems. This creates a vicious cycle – the more these type of attacks “succeed” the more frequently they occur.”
Another driver of the sharp rise in activity was the development of the double-extortion tactic, that being the tactic of demanding a ransom and threatening to release data stolen before encryption. It is believed that this tactic is pushing more organizations to pay the ransom as they also fear the result of having their data leaked. Many of today's major ransomware threats have quickly adopted this tactic. In preventing falling victim to ransomware attacks the same advice still applies, make sure software is patched, educate employees, and have a robust backup policy. Despite the prevalence of these attacks, they are still preventable.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion