Maze Gang opts for Early Retirement
Maze operations began only in May 2019, with just over a year of active campaigns under their belt they are looking into early retirement, according to an article published on Bleeping Computer. The ransomware rose to prominence incredibly quickly, based on a savvy change of tactics, media relations, and a list of high-profile victims. The list includes Canon, Xerox, and LG just to name a few. It appears that the gang has taken to heart the adage of getting out when you’re on top.
This is not the first time the community has seen a gang retire seemingly at the top of their game. In the middle of 2019, the operators behind the GandCrab announced their retirement on underground forums and subsequently released decryption keys so that those still locked out of their systems could remedy the situation and decrypt files. Whether the decision to retire was made on their own volition or not can be argued as the gang had come increased pressure from the No More Ransom collective who were actively working to create decryptors for the latest versions of the ransomware at the time. GandCrab for its part had a significant impact on ransomware operations going forward. They refined the Ransomware-as-a-Service (RaaS) model, a model adopted by today’s most successful ransomware gangs, and constantly updated their malware and tactics to make defending against an infection a harder prospect.
Like GandCrab, Maze too has had a similar impact on the ransomware ecosystem. The later will be best known for adopting the double extortion tactic which involves the gang threatening to release data stolen from the victim before encryption. Not only was Maze the first to threaten but likely the first to leak stolen data to the public. The leaking of data was done by what would become known as a leak site managed by the gang. This too was to become standard practice amongst today’s top ransomware threats. Not only was the website used to leak data but make announcements as to victims as well as press releases.
This displayed a level of media savviness often lacking in other hackers and cybercrime groups. Another of Maze’s defining characteristics was the creation of a ransomware cartel with LockBit and RagnarLocker. Maze’s fame and tactics led another ransomware gang SunCrypt to claim that it had joined the cartel, however, this forced Maze to make a public statement to the contrary. Given that Maze was willing to announce new partnerships readily on their website it can be assumed SunCrypt was trying to use Maze’s success to boost its own public relations.
Affiliate Speaks Out
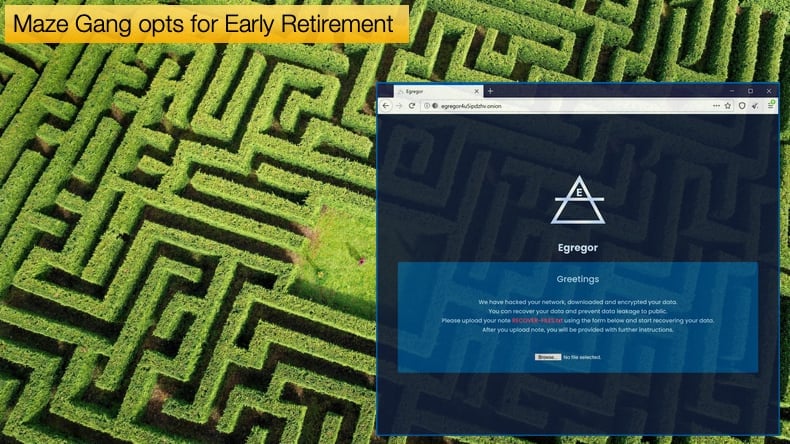
According to the Bleeping Computer articles, rumors began surfacing that Maze was winding down operations roughly six weeks ago. Much of the reported information came to Bleeping Computer via a threat actor believed to be an affiliate of Maze RaaS actions. The threat actor stated that they were involved in the recent Barnes and Noble incident believed to be associated with a new ransomware strain Egregor which is closely related to the Sekhmet ransomware strain. Much of what the threat actor said confirmed how many security researchers believed how affiliate partnerships work. This threat actor stated that they were responsible for compromising networks and stealing Windows credentials. The credentials and access to the compromised network would be handed over to another affiliate responsible for deploying the ransomware. According to the threat actor, those compromising the network, deploying the ransomware, and developing the ransomware would then equally split all ransomware payments.
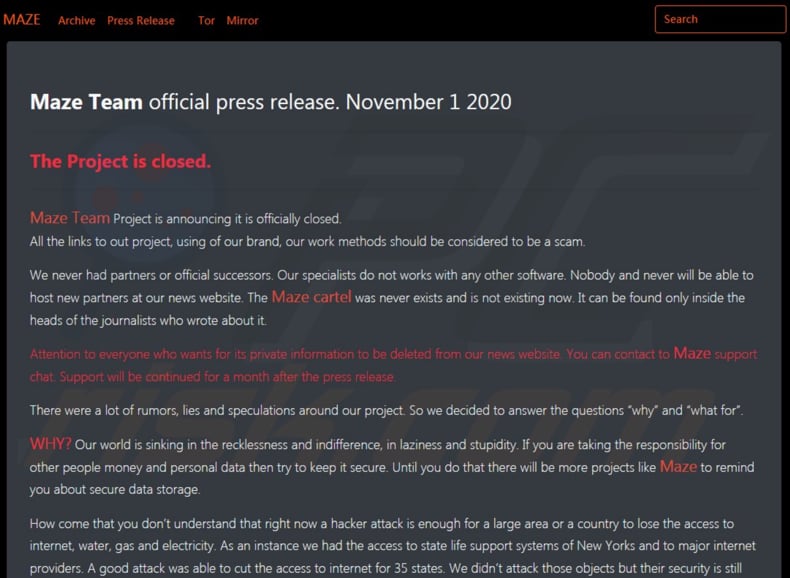
Bleeping Computer reached out to Maze for a response to the affiliate’s statement and replied simply with, “You should wait for the press release.” Several factors corroborate the affiliate's claims, the first being that Maze has started to remove victims posted to the leak site. Currently, only two victims remain on the site who have already had their data leaked for non-payment of the ransom demand. In the past, the removal of victims from a leak site has been a clear indication that operations are being shut down. If this is the case it is hoped that master decryption keys will be released so that those still impacted by the ransomware can recover encrypted data.
It is further believed that many of the Maze’s affiliates have moved to work with Egregor. When Maze operations were winding down spikes in Egregor activity were seen in September. It is also believed that Maze, Egregor, and Sekhmet are either fundamentally the same or very closely related. Further, security researcher Michael Gillespie who has been analyzing Egregor and Sekhmet discovered that victims infected by Egregor received decryptors that were titled “Sekhmet Decryptor” once they had paid the ransom.
This is perhaps an indication that while Maze’s developers are retiring those partnered with are not willing to take early retirement. Rather, they are willing to offer their skills to other malware developers for a split of the profits. Rather, than signaling an end to ransomware, which would be hopeful in the extreme, it is an indication of how well the malware tactics have evolved from encrypting end-users’ photos and files for a couple of hundred dollars in Bitcoin to know targeting massive organizations, encrypting vital network assets and demanding millions of dollars. The ecosystem has itself involved to promote affiliate interaction and partnerships, not unlike modern affiliate relations seen in legal industries. While Maze might be on its way out its developers have defined what modern ransomware is capable of.
In Steps Egregor
For little over a month Egregor has shown that it has learned all the lessons Maze has had to offer. In a little over a month, the gang has added Barnes and Noble, Ubisoft, and Crytek to its victim list. The malware’s developers have a dedicated leak site and based on recent revelations have a booming affiliate network. It will be seen shortly how successful the ransomware strain is but given its recent activity, it is little wonder that Maze affiliates see new opportunities to turn large profits. Often ransomware gangs report making tens of millions of dollars. Sodinokibi announced that it extorted over 100 million USD in one year. While the veracity of the claims can be questioned, even if the gang made a quarter of what they claim it is still a significant amount, and little wonder those with the skills to gain network access or deploy malware successfully what a piece of the pie.
Recent research suggests that a ransomware attack occurs every fourteen seconds. These attacks have the potential to cripple networks and cause significant downtime resulting in loss of earnings as many victims have discovered. This does not take into account earnings lost due to ransom payments or recovery costs associated with an infection. The rise of ransomware is at odds with the preventable nature of ransomware attacks. This may be due to there being no real silver bullet that stops a ransomware attack, rather the attack is prevented by adopting good security habits. Another measure is putting an effective backup policy in place that uses both onsite and offsite backup technologies. A good backup can be the difference between being down for a day or a couple of weeks as some victims have experienced.
The problem of ransomware is not going away, some believe it is getting worse. Maze’s retirement shows how complex the ransomware ecosystem has become and with the removal of one major player from the game, others are willing to step up to fill the void. Government authorities seem to understand the depth of the problem but are at a loss to stop it. This has resulted in calls to make paying the ransom illegal. It is hoped that this will dry up the profit generated by ransomware gangs and hopefully solve the problem. For some this feels like victims are being punished but as many ransomware incidents have been deemed to be preventable a counter argument exists to this view. The only certainty of the situation is that we will see new victims weekly for some time to come.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion