Cring Ransomware seen exploiting VPN Vulnerabilities
The recent Exchange Server vulnerability and news that the flaws were being used to spread ransomware dominated many InfoSec headlines. However, Kaspersky’s recent discovery of the Cring ransomware strain using an old VPN vulnerability as the initial attack vector reminds us that ransomware operators can always dig into the old bag of tricks to pull off a successful attack.
On January 26, 2021, Swisscom CSIRT tweeted,
“CRING a new strain deployed by human operated ransomware actors. After the actors have established initial access, they drop a customized Mimikatz sample followed by #CobaltStrike. The #CRING #ransomware is then downloaded via certutill.”
While it was clear that an attack had occurred, it was unknown at the time exactly how the ransomware managed to gain a foothold on the target network then infect the target network.
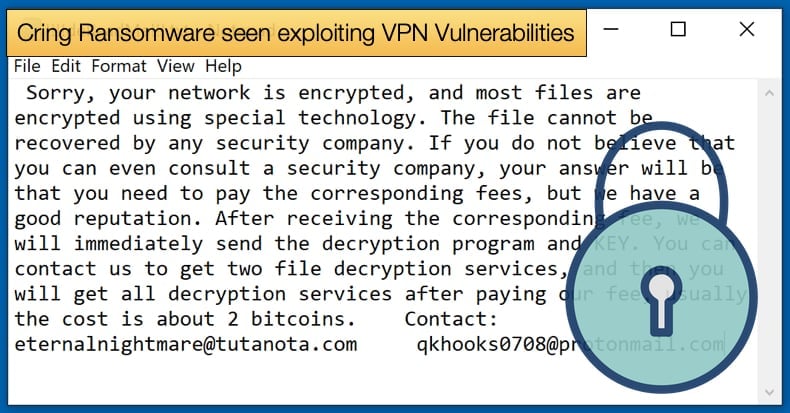
In what is a bittersweet reality, an attack occurred on an enterprise which allowed Kaspersky researchers to analyze the attack and the malware used. Victims of this campaign tended to be industrial enterprises located within Europe. In one case the attackers managed to cause a temporary shutdown of industrial processes as the attacker managed to compromise servers used in industrial control processes.
As mentioned above, the attackers did not use any new or previously unknown vulnerabilities but rather a VPN vulnerability dating back to 2018. The vulnerability, CVE-2018-13379 impacts Fortigate VPN servers. The vulnerability has been patched and Fortinet issued warnings to customers to update and patch the flaw as soon as possible.
Warnings had been issued as late as March 2020, showing that the companies were aware of unpatched systems being exploited. If unpatched, Fortiguard devices are vulnerable to what is called a directory traversal attack. These attacks will look to gain access to credentials like passwords that are stored without proper encryption somewhere within the directory. In this instance, the vulnerability if properly exploited allows the attacker to access system files on the Fortigate SSL VPN appliance. Researchers noted,
“Specifically, an unauthenticated attacker can connect to the appliance through the internet and remotely access the file “sslvpn_websession”, which contains the username and password stored in cleartext.”
To find vulnerable servers the attackers simply scanned for vulnerable IP addresses. The attackers could have also purchased a list containing vulnerable IP addresses. To support this claim, Kaspersky researchers pointed to a post on an underground hacking forum from August 2020 advertising such a list was available to purchase.
Once the vulnerability is exploited, the attackers use two freely available tools to supplement lateral movement across the network. The first of these tools is Mimikatz which has also been used recently by the Pysa ransomware gang in attacks against the education sector. Mimikatz is used in the Cring campaign to steal Windows account credentials of those who had previously logged into the now compromised system.
The second tool, and a classic one used by hackers, is CobaltStrike is advertised as a legitimate system penetration tool to help detect bugs and vulnerabilities in code. However, hackers use the tool to distribute malware. In the case analyzed by Kaspersky researchers, CobaltStrike is loaded via a malicious PowerShell script that installs CobaltStrike Beacon. This grants the attacker a backdoor into the compromised network granting the attackers remote control of the compromised system.
Cring Ransomware
Once a backdoor is installed and the attackers are granted remote control, they will drop the Cring ransomware module that is responsible for encryption. Researchers noted,
“After being installed on the system, the cmd script named execute.bat was executed. The script launched PowerShell under the name “kaspersky”. The attackers used this technique to mask the traces of the malware activity and disguise the operation of the malware as that of security solutions. A command to download a file from the internet was passed to the running PowerShell shell. The file’s URL was http://45.67.231[.]128/ip.txt.
The downloaded file was saved as C:\__output….Although the file specified in the URL had the extension .txt, it was in fact the executable file of the malware – the Cring ransomware. At the time of analyzing the malware hosting server, the file ip.txt had already been removed, but the attackers had uploaded a newer version of the Cring malware (the file NoNet.txt) to the server.”
Cring not only attempts to hide processes by labeling them as “Kaspersky'' but is also capable of detecting and deleting backups. Researchers discovered that the malware could remove backup copies and halt services for Veritas NetBackup and Microsoft SQL Server. The malware will also close programs that might hinder encryption. This is important as often files opened or in use cannot be encrypted unless closed.
To do the malware will close Microsoft Office and Oracle Database software. Lastly, before encryption begins the malware will remove backup files with the following extensions: VHD, .bac, .bak, .wbcat, .bkf, .set, .win, and .dsk. The malware can also remove a file or folder with the term “backup” in the name.
Only once these steps are completed will the malware move to encrypt files from a wide variety of file types including the usual suspects like .doc, .docx, .vdhx, and .xlx. A complete list of targeted file types for encryption can be found in Kaspersky’s published research including a comprehensive indicators of compromise list. As to how the malware encrypts data, researchers stated,
“Next, the malware started to encrypt files using strong encryption algorithms, which means that files could not be decrypted without knowing the RSA private key held by the attackers. Each file was encrypted using AES and the AES encryption key was in turn encrypted using an RSA public key hard-coded into the malicious program’s executable file. The RSA key size was 8,192 bits.”
Best Practises Ignored
In the successful attack which caused a shutdown of industrial processes, it is clear that commonly accepted best cybersecurity practices were not implemented or ignored. The exploitation of an old and patched vulnerability was the initial attack vector allowing the attackers to gain a foothold into the network. The victim had an outdated and vulnerable firmware version on the Fortigate VPN server (version 6.0.2 was used at the time of the attack) that could be exploited by attackers. This despite several warnings from Fortinet and a patch available for the vulnerable Fortigate VPN servers.
While the above-mentioned flaw was the initial vector, several other factors made the attack worse than it had to be. First, the antivirus database of the security solution found on the network was not updated in a regular or timeous fashion. This prevents the solution from detecting the intrusion and malware then subsequently blocking the threat. Researchers also noted that components of the security solution were turned off. These, if turned on, may have helped prevent the attack from going further once the vulnerability was exploited.
Second, the network infrastructure and who had access to what would be a major point of concern. In summary, there were no restrictions to access different systems on the network, anyone no matter their position within the company would have been able to access any system. For hackers who look to gain privileged access to networks to launch malware, their job is made infinitely easier when too many employees have privileged access. In the attack, this allowed the attackers to infect industrial processes they should not have been able to access with any ease.
Last, while not being discussed by Kaspersky’s researchers and might not have been an issue in this instance, it is important to have a comprehensive offline backup policy. Given that Cring will search and delete backups as well as certain file formats associated with backup software, having offline or offsite backups would prevent a lot of damage and financial loss. It is common for ransomware to target backups as this forces the victim to pay if they cannot recover data.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion