Sodinokibi Blamed for JBS Ransomware Incident
Shortly after this publication posted an article detailing the JBS Incident the FBI issued a statement officially attributing the attack to the now infamous Sodinokibi ransomware gang. Sodinokibi is also tracked by several security firms as REvil. Since the release of the statement at least two high-profile ransomware incidents have been disclosed to the public and the US President’s administration has now drawn a line in the sand regarding how it and the US Department of Justice will treat ransomware attacks moving forward.
The statement released by the FBI can only be described as short and sweet. Consisting of just one paragraph the statement said,
“As the lead federal investigative agency fighting cyber threats, combating cybercrime is one of the FBI’s highest priorities. We have attributed the JBS attack to REvil and Sodinokibi and are working diligently to bring the threat actors to justice. We continue to focus our efforts on imposing risk and consequences and holding the responsible cyber actors accountable. Our private sector partnerships are essential to responding quickly when a cyber intrusion occurs and providing support to victims affected by our cyber adversaries. A cyberattack on one is an attack on us all. We encourage any entity that is the victim of a cyberattack to immediately notify the FBI through one of our 56 field offices.”
The terse nature of the statement and the line “A cyberattack on one is an attack on us all,” are key indicators of how the powers that be in the US are treating cyberattacks. Based on previous events and statements from all levels of government, organizations are aligning to read off the same playbook regarding ransomware and other cyberattacks. There has been a steep rise in ransomware attacks, particularly target infrastructure and public services in the last few months, the Colonial Pipeline Incident being the most well-known for the disruption it caused.
The attack resulted in one of the US’s largest petroleum pipelines having to be shut down, this caused shortages of several kinds of fuel to be experienced on the Eastern seaborn of the US. This further prompted a statement to be issued by President Biden outlining new measures to strengthen both the government and private industries' response to the scourge of ransomware.
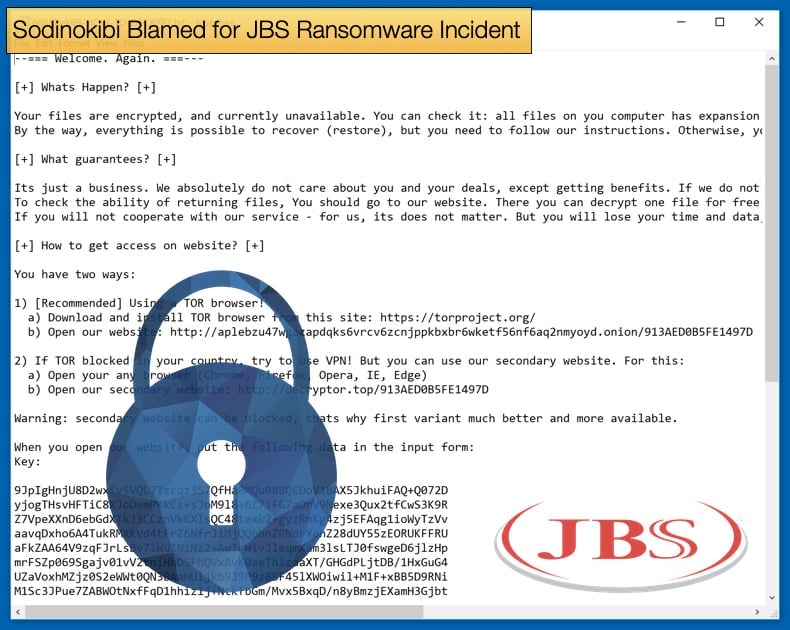
As to the Sodinokibi Ransomware, despite its prevalence and infamy, not much information has been disseminated to the public about how the malware operates or how the gang operates in distributing the malware. A few deep dives exist on the Internet, namely from the following security firms, Acronis, and Cybereason. Some of these guides are no older than a year so to say for definite how the JBS incident occurred is premature until more information becomes available.
There are a few constants across several attacks, including Acer and Travelex to name a few victims, that have been determined. Defining traits include as summarised by Acronis researchers:
- Sodinokibi is likely being distributed by attackers affiliated with those that distributed the infamous GandCrab ransomware family, which is supposed to be retired soon according to the underground forum where GandCrab first appeared.
- Sodinokibi tries to avoid infecting computers from Iran, Russia, and other countries that were formerly part of the USSR.
- Sodinokibi uses an Elliptic-curve Diffie-Hellman key exchange algorithm to generate and propagate encryption keys.
- Sodinokibi ransomware exploits an Oracle WebLogic vulnerability (CVE-2019-2725) to gain access to the victim’s machine. Once it’s in, the malware tries to execute itself with elevated user rights to access all files and resources on the system without any restriction. (Other vulnerabilities have been exploited in the past.)
- This ransomware strain uses AES and Salsa20 algorithms to encrypt user’s files, AES is used to encrypt session keys and data that is sent to the control server, user files are encrypted using Salsa20 encryption.
- Once it infiltrates a machine, it wipes out all the files in the backup folder.
Latest Victims
Following the JBS incident, there have been two more high-profile ransomware incidents that have been disclosed to the public. The first of these involves Japanese conglomerate Fujifilm who released a statement saying that the company believes it suffered a ransomware attack on June 1. No mention of which ransomware strain was used in the attack at this time. In Bleeping Computer’s coverage of the attack, Vitali Kremez notes that the corporation was infected with the QBot trojan. The trojan is also tracked as QakBot.
QBot has a long history with partnering with ransomware gangs, including Egregor. Typically, QBot is distributed via phishing email campaigns, with the malware payload used to grant initial access to the victim’s machine. Once initial access is granted a ransomware payload can be dropped onto the machine for data encryption and extortion.
The next attack disclosed involved a Hospital Group in Florida, US. Reports emerged that UF Health Central Florida suffered a reported ransomware attack that forced two hospitals to shut down portions of their IT network. The Hospital Group issued a statement saying,
“On the night of May 31, UF Health Central Florida detected unusual activity involving its computer servers. Our information technology team is collaborating with IT experts on our Gainesville and Jacksonville campuses to investigate the situation and mitigate any potential risks…In an abundance of caution, we have suspended access to some of our Central Florida systems, including email, and have implemented our backup procedures as our teams continue to work to ensure that all data and networks are secure.”
Response from the White House
The problem of ransomware seems to have reached a boiling point that has prompted a response from the current administration. Anne Neuberger, Deputy Assistant to the President and Deputy National Security Advisor for Cyber and Emerging Technology issued a statement on behalf of the White House titled, “What We Urge You To Do To Protect Against The Threat of Ransomware,” which not only advises on mitigation measures but also stated that the issue was being dealt with as a matter of top priority. The statement concluded by saying,
“Ransomware attacks have disrupted organizations around the world, from hospitals across Ireland, Germany and France, to pipelines in the United States and banks in the U.K. The threats are serious and they are increasing. We urge you to take these critical steps to protect your organizations and the American public. The U.S. Government is working with countries around the world to hold ransomware actors and the countries who harbor them accountable, but we cannot fight the threat posed by ransomware alone. The private sector has a distinct and key responsibility. The federal government stands ready to help you implement these best practices,”
Following the release of the statement, Reuters reported that the U.S. Department of Justice is elevating investigations of ransomware attacks to a similar priority as terrorism in the wake of the Colonial Pipeline incident. and mounting damage caused by cybercriminals. This change in doctrine was signaled by an internal guidance document sent to US Attorney’s offices across the US. Further, the guidance also instructed attorneys to coordinate efforts with the task team established by President Biden following the Colonial Pipeline incident. The guidance, as seen by Reuters stated,
“To ensure we can make necessary connections across national and global cases and investigations, and to allow us to develop a comprehensive picture of the national and economic security threats we face, we must enhance and centralize our internal tracking,”
The model that the internal guidance establishes is one that was previously used in cases of terrorism. This may present a significant sea change in attitudes towards ransomware that may be followed by the US’s allies soon. While many ransomware gangs operate in Russia where as long as they do not target Russians or Russian interests, they can operate with little threat of the law catching up to them. Slowly this status quo appears to be changing as more political will is been put behind efforts to stop ransomware.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion