US Treasury Department Sanctions Ukrainians for Alleged Russian Assistance
The US Treasury Department announced that the department had sanctioned four Ukrainian individuals under suspicion that they had “engaged in Russian government-directed influence activities to destabilize Ukraine”. These efforts are believed to be done with the view of assisting any military effort to control Ukrainian critical infrastructure for the benefit of Russia.
The Treasury Department's Office of Foreign Assets Control (OFAC) issued sanctions against Taras Kozak, Oleh Voloshyn, Volodymyr Oliynyk, and Vladimir Sivkovich. Those accused are either current or former Ukrainian officials ordered to gather information and spread disinformation.
Kozak and Voloshyn are both current members of the Ukrainian Parliament while Oliynyk is a former government official who fled to Russia. Sivkovich is the former Deputy Secretary of the Ukrainian National Security and Defense Council.
Ideal candidates if one needs to both gather information and sow disinformation. The sanctions imposed on the four means that any US property owned by any of the four needs to be reported to the Treasury Department's Office of Foreign Assets Control (OFAC) and the four are barred from conducting any business in the US.
It is also important to note that the sanctions were imposed with the help of Ukrainian officials and were not done unilaterally.
As to what each individual did exactly, the announcement issued by the Treasury Department was certainly not shy on details. Regarding Kozak, it was noted,
“Kozak, who controls several news channels in Ukraine, supported the FSB’s plan to denigrate senior members of Ukrainian President Volodymyr Zelenskyy’s inner circle, falsely accusing them of mismanagement of the COVID-19 pandemic. Furthermore, Kozak used his news platforms to amplify false narratives around the 2020 U.S. elections first espoused by U.S.-designated Andrii Leonidovych Derkach (Derkach). Kozak has attempted to legitimatize Derkach’s claims by rebroadcasting Derkach’s false assertions about U.S. political candidates. Throughout 2020, Kozak worked alongside FSB intelligence agents.”
And regarding Voloshyn,
“Voloshyn has worked with Russian actors to undermine Ukrainian government officials and advocate on behalf of Russia. Voloshyn also worked with U.S.-designated Konstantin Kilimnik, a Russian national with ties to Russian intelligence who was sanctioned for attempts to influence the U.S. 2020 presidential election, to coordinate passing on information to influence U.S. elections at the behest of Russia.”
Regarding the two former Ukrainian officials, Volodymyr Oliynyk and Vladimir Sivkovich, Oliynyk led Ukraine to seek refuge in Russia and is currently residing in Moscow, Russia. Olinyk is believed to have provided the FSB, Russian Intelligence, with information pertaining to Ukraine’s critical infrastructure, with the country’s energy sector proving to be particularly interesting to Russian intelligence.
As for Sivkovich the former Deputy Secretary of the Ukrainian National Security and Defense Council, it is alleged that in 2021 Sivkovich worked with a network of Russian intelligence officials to carry out influence operations intended to build support for Ukraine to officially cede Crimea to Russia in exchange for a drawdown of Russian-backed forces in the Donbas, where separatists continue to receive support from Russia.
Further, in 2020, Sivkovich coordinated with Russian intelligence services to promote a disinformation campaign against the U.S. 2020 presidential election.
The Treasury Department added that the actions of these individuals are in line with Russia’s current geopolitical agenda, stating,
“The overall strategy is designed to pull Ukraine into Russia's orbit by thwarting Ukraine's efforts at Western integration, especially with the European Union (EU) and North Atlantic Treaty Organization (NATO). [Russia] has focused on disrupting one critical infrastructure sector in particular: Ukraine's energy sector. Russia has also degraded Ukraine's access to energy products in the middle of winter. Acting through Russia's state-owned gas company Gazprom, Russia has repeatedly disrupted supplies to Ukraine -- a vital transshipment country with pipelines to other European countries -- due to purported disputes over gas pricing.”
Sanctions on the Heels of Cyberattacks
The sanctions issued by the Treasury Department follow a series of cyberattacks conducted against Ukrainian websites associated with state entities. Ukrainian law enforcement announced that more than 70 state websites were attacked and accused threat actors believed to be associated with Russian intelligence services of being behind the incident.
Ten of the websites were subject to what the authorities termed “were subjected to unauthorized interference,” while many of the others including the websites linked to the country's energy, treasury, environment, veterans, and state emergency service departments were defaced.
Law enforcement officials were quick to point out that the content on the sites was not changed, and no personal data was compromised, contrary to claims made by the threat actors responsible.
Following the announcements made by various Ukrainian state entities, Microsoft via a blog post announced,
“Microsoft Threat Intelligence Center (MSTIC) has identified evidence of a destructive malware operation targeting multiple organizations in Ukraine. This malware first appeared on victim systems in Ukraine on January 13, 2022. Microsoft is aware of the ongoing geopolitical events in Ukraine and surrounding region and encourages organizations to use the information in this post to proactively protect from any malicious activity."
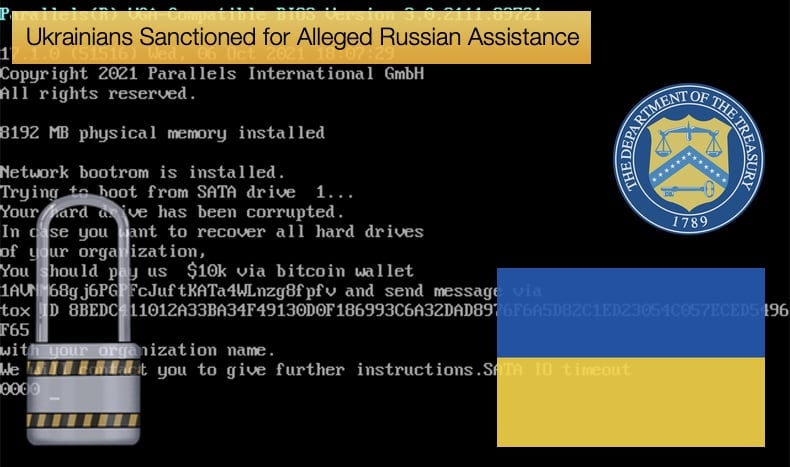
The malware was discovered on multiple governments, non-profit, and information technology organizations, all based in Ukraine. Worryingly the malware was designed to look like ransomware but lacks any of the data recovery mechanisms modern ransomware puts in place to decrypt data after encryption.
This places the discovered malware firmly in the realm of destructive malware not dissimilar to Iranian data wipers. This is not the first time malware targeting Ukrainian infrastructure has masqueraded as ransomware but is intended to be destructive in nature rather than financially rewarding. Malware strains seen to fit this bill in the past have been NotPetya, Bad Rabbit, and GoldenEye.
Microsoft notes that the malware will attempt to wipe the Master Boot Record, as past wipers have been seen to do, rendering the infected device useless. To maintain the illusion that the malware is ransomware, once the Master Boot Record (MBR) is rewritten the malware will drop a ransom note containing a Bitcoin wallet and Tox ID, which is a unique account identifier used in the Tox encrypted messaging protocol.
Rewriting the MBR is atypical of ransomware with modern ransomware strains encrypting data rather than rendering the device completely useless as rewriting the MBR offers no mechanism for data recovery.
The current stand-off between Russia and the West that is playing out in Ukraine has much of the world even more stressed than normal. Needless to say, such actions have a terrible impact on the Ukrainian people, it is hoped a diplomatic solution can be found so that no increase in cyber and military hostilities is seen.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion