Mars Stealer Emerges as Racoon Stealer Ceases Operations
Mars Stealer appears to be rising in popularity among hackers looking to steal information without spending extended periods developing their malware. Mars Stealer first announced its presence on the malware scene in 2021 on underground hacker forums marketed as a malware-as-a-service (MaaS). A quick look at the malware’s past shows its development has taken advantage of the rise and fall of other malware strains.
Mars Stealer is fundamentally a newer variant of Oski a previous information stealer whose operations shutdown in 2020. With Oski now out of business, there was a need in the malware market for another similarly useful piece of malware capable of stealing sensitive information off victim’s machines.
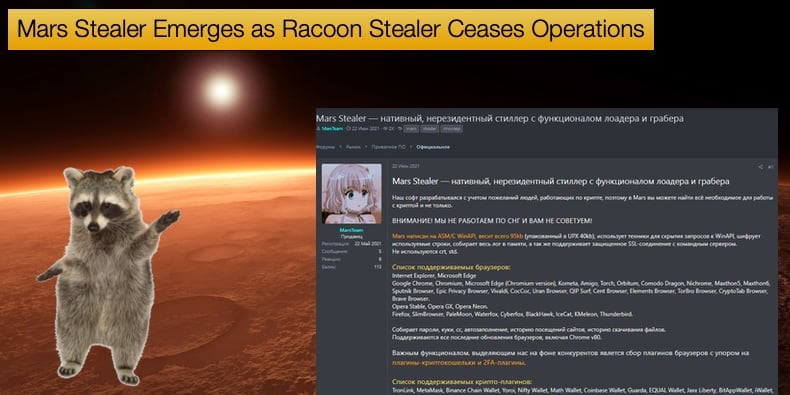
A year later Mars Stealer emerged on forums being advertised as Oski’s better in every way and affordable too. Current versions of the malware goes for 140 to 160 USD, which for some will seem like an investment in terms of potential illicit profits one can achieve from selling information.
Security researcher 3xp0rt managed to get a sample of the malware and did a deep dive into it quickly determining the malware to be built on the ground already trodden by Oski. In 3xp0rt’s analysis noted that Mars Stealer was not just a copy but an improved version of Oski.
This is due in part to the increase in the scope of sources information can be stolen from. Browsers, two-factor authentication (2FA) apps, crypto extensions, and wallets could be liable to have information siphoned off.
The following Internet browsers and apps can be targeted: Google Chrome, Internet Explorer, Microsoft Edge (Chromium Version), Kometa, Amigo, Torch, Orbitium, Comodo Dragon, Nichrome, Maxxthon5, Maxxthon6, Sputnik Browser, Epic Privacy Browser, Vivaldi, CocCoc, Uran Browser, QIP Surf, Cent Browser, Elements Browser, TorBro Browser, CryptoTab Browser, Brave, Opera Stable, Opera GX, Opera Neon, Firefox, SlimBrowser, PaleMoon, Waterfox, CyberFox, BlackHawk, IceCat, K-Meleon, Thunderbird.
Likewise 2FA apps: Authenticator, Authy, EOS Authenticator, GAuth Authenticator, Trezor Password Manager.
Crypto extensions: TronLink, MetaMask, Binance Chain Wallet, Yoroi, Nifty Wallet, Math Wallet, Coinbase Wallet, Guarda, EQUAL Wallet, Jaox Liberty, BitAppWllet, iWallet, Wombat, MEW CX, Guild Wallet, Saturn Wallet, Ronin Wallet, Neoline, Clover Wallet, Liquality Wallet, Terra Station, Keplr, Sollet, Auro Wallet, Polymesh Wallet, ICONex, Nabox Wallet, KHC, Temple, TezBox Cyano Wallet, Byone, OneKey, Leaf Wallet, DAppPlay, BitClip, Steem Keychain, Nash Extension, Hycon Lite Client, ZilPay, Coin98 Wallet.
Crypto wallets: Bitcoin Core and all derivatives (Dogecoin, Zcash, DashCore, LiteCoin, etc), Ethereum, Electrum, Electrum LTC, Exodus, Electron Cash, MultiDoge, JAXX, Atomic, Binance, Coinomi.
Mars Stealer also boasts several methods to evade detection. The malware is packaged in only 95 Kb which includes two encryption routines that hide API calls and encrypted coded strings to further hamper detection and analysis.
The information it collects is wrapped in memory, while all connections with the C2 are done with the SSL (Secure Sockets Layer) protocol, so they’re encrypted.
Moreover, the Mars Stealer code contains Sleep function intervals to perform timing checks that would result in a mismatch if a debugger is used. Lastly, the malware can delete itself after the intended user data has been exfiltrated or when the operator decides to.
Racoon Stealer Ceases Operations
The latest development that has seen the developer of Mars Stealer given an opportunity to exploit is Racoon Stealer ceasing operations. In 2021, this publication covered how Racoon Stealer had been improved to target information related to victim’s crypto assets.
A year later the malware’s developer announced that they were ceasing operations due to the war in Ukraine. The announcement was made on a Russian-speaking hacking forum with the developer stating,
“Dear Clients, unfortunately, due to the "special operation", we will have to close our project Raccoon Stealer.
The members of our team who are responsible for critical moments in the operation of the product are no longer with us.
We are disappointed to close our project, further stable operation of the stealer is physically impossible.”
Following this Mars Stealer saw, an influx of new users increased the malware’s popularity. That said the malware’s developer has taken the opportunity to improve Mars Stealers' capabilities further.
Security researchers for Morphisec discovered several Mars Stealer distribution campaigns following the increase in popularity. In one new campaign, it was found that Google-Ads are being used to distribute the malware, particularly in Canadian search results for Open Office, the popular open-source office software package.
If a victim clicks through on the ad they are redirected to a website that prompts the potential victim to download what they believe to be an Open Office package.
The reality is that it is a phony download that includes a Mars Stealer executable packed with the Babadeda crypter or the Autoit loader.
In this campaign, the stolen information produced by Mars Stealer appears to contain browser auto-fill data, browser extension data, credit cards, IP address, country code, and timezone.
As to the threat posed by Mars Stealer, Morphisec researchers concluded,
“Morphisec Labs will keep monitoring the Mars Stealer and provide updates when appropriate. Infostealers are used by a wide variety of cybercriminals, from novices to state-sponsored actors. They’re easy to acquire—and they work. Mars is currently being promoted in over 47 different underground forums, Darknet onion sites, and Telegram channels, and even has an official Telegram channel for purchasing through.”
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion