Qakbot Deploys New Distribution Method
Qakbot, also tracked as QBot, is well known for its botnet distributing the credential-stealing trojan component of the malware via malicious Microsoft Office documents. In many instances, Office documents, especially Word documents, would abuse the application’s macros feature to run malicious code.
This would often involve tricking the victim into enabling macros by alerting the victim to the document containing important information that can only be viewed if the alert is agreed to.
Qakbot typically targeted enterprises crafting email campaigns that would appear like bills, invoices, and other business-related documents requiring the victim’s immediate attention.
In the past Qakbot has employed highly targeted email campaigns often described as “context aware” email campaigns. This phishing technique is a highly targeted form of phishing where the attacker will use carefully crafted decoy content customized for each target recipient.
Often the attacker will first perform a recon campaign to get information that they can then utilize to craft the customized emails that would make up the context-aware campaign.
Upon deeper analysis, the attacker will often use the intended victim's social media profiles to gain more insight or by using mass spam emails that would link to what is called a non-critical website.
Such websites are designed to harvest information and do not provide the attacker with an immediate financial reward. Another method of harvesting information is by analyzing a victim’s browsing history.
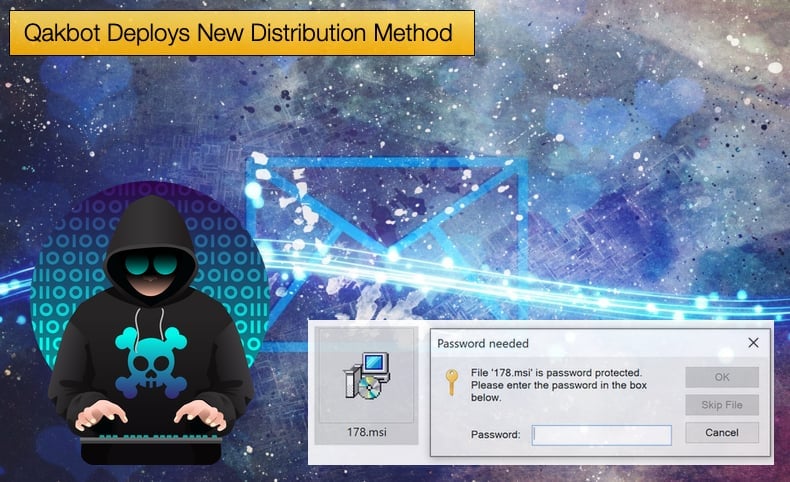
Now with Microsoft implementing new security features Qakbot’s creators are forced to find a new way to distribute their malware without using malicious office documents. Now the Qbot botnet is pushing malware payloads via phishing emails with password-protected ZIP archive attachments containing malicious MSI Windows Installer packages.
This marks a massive change in tactics by those distributing the malware. The security changes implemented by Microsoft involve plans to kill malware delivery via VBA Office macros after disabling Excel 4.0 (XLM) macros by default. Tom Gallagher, Partner Group Engineering Manager, Office Security, stated,
“A wide range of threat actors continue to target our customers by sending documents and luring them into enabling malicious macro code. Usually, the malicious code is part of a document that originates from the internet (email attachment, link, internet download, etc.). Once enabled, the malicious code gains access to the identity, documents, and network of the person who enabled it.”
As for the restriction involving Excel 4.0 macros, Microsoft notes,
“A new Excel Trust Center settings option to further restrict the usage of Excel 4.0 (XLM) macros is now generally available. Building on the recent release of AMSI integration for XLM macros, this setting enables Microsoft 365 customers to further protect themselves against the latest threats. Found in the Trust Center Macro Settings, this new checkbox setting, “Enable Excel 4.0 macros when VBA macros are enabled”, allows users to individually configure the behavior of XLM macros without impacting VBA macros.”
Qakbot’s Building Blocks
There is a fairly good argument to be made that the security changes Microsoft is implementing are due in part, at least, to their previous analysis of Qakbot. In December 2021, Microsoft’s 365 Defender Threat Intelligence Team published an in depth article looking at modern Qakbot tactics.
The malware is now well over ten years old but due to the malware’s inherent modularity could be quickly pivoted to perform new tasks.
As an example of this the malware began life as a banking trojan but can now perform several other tasks including: performing reconnaissance and lateral movement, gathering and exfiltrating data, or delivering other payloads on affected devices.
This modularity and flexibility has even been used to help distribute the Egregor ransomware. This poses a unique challenge to those tasked with defending IT infrastructure. As MIcrosoft notes,
“Qakbot’s modularity and flexibility could pose a challenge for security analysts and defenders because concurrent Qakbot campaigns could look strikingly different on each affected device, significantly impacting how these defenders respond to such attacks. Therefore, a deeper understanding of Qakbot is paramount in building a comprehensive and coordinated defense strategy against it.”
While Qakbot presents several challenges to security researchers, Microsoft security researchers have noted that Qakbot campaigns to consist of several fundamental building blocks.
These might not all be present in a campaign but can be summed done to the first building blocks being dependent on the the email mechanism used to distribute the malware payloads. While, the email mechanism might rely on a malicious document, malicious hyperlinks and embedded images have been used in the past.
Critically these must all abuse macros to deliver the malware payload. The success of of a Qakbot campaign resys on the user enabling Macros so that the malware payload can be downloaded and executed. The infection chain once Macros are enabled has been summarized by Microsoft, with researchers noting,
“If the user goes ahead and enables the macro, Excel immediately checks if there is a subprocedure predefined in the macro to run automatically once the document opens; in this case, auto_open(). The Visual Basic for Applications (VBA) code written within this subprocedure creates a new macrosheet and then writes Excel 4.0 formulas in several of its cells. Next, it jumps to one cell in this sheet by calling the Application.Run method. In this way, the VBA code starts the Excel 4.0 macro code that was just written to the macrosheet.”
It is little wonder that Microsoft’s security teams have moved to improve the security of macros through several updates including disabling macros by default.
This also means that educating staff as to the dangers of enabling macros and the various tricks employed by hackers to get users to enable the feature if disabled is a far simpler process when compared to explaining exactly how the malware operates.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion