Matanbuchus Malware Now Dropping Cobalt Strike Beacons
Researchers have discovered a new spam email campaign dropping the Matabuchus malware which then drops Cobalt Strike beacons. This is by far not the first time we have seen other malware strains dropping Cobalt Strike beacons, previously we have seen Emotet doing almost the same thing.
Just as a reminder, Cobalt Strike is advertised as a penetration testing tool and has been used as such by legitimate penetration testers in the past. However, the tool was quickly subverted to the wills of malicious hackers when the code was leaked.
A Cobalt Strike beacon is the term used for the malware’s main payload used to create a connection to the team server. If the beacon is used to create a fullback door on the victim's machine then the beacon can be used to drop other malware strains onto the infected device.
In the past beacons have been used to lay much of the groundwork for a ransomware attack. Matanbuchus is a malware-as-a-service that once executed can load executables directly from memory. More on Matanbuchus below.
As for the latest campaign, security researcher Brad Duncan managed to attain a sample of Matanbuchus and then mapped out how it deploys a Cobalt Strike beacon.
For a more technical write-up as well as indicators of compromise it is suggested that you read Duncan’s article published on the matter.
The phishing campaign currently uses lures that pretend to reply to previous email conversations, so they feature a 'Re:' in the subject line. The emails carry a ZIP attachment that contains an HTML file that generates a new ZIP archive.
This ultimately extracts an MSI package digitally signed with a valid certificate issued by DigiCert for "Westeast Tech Consulting, Corp."
If the MSI installer is run it will pretend to initiate an Adobe Acrobat font catalog update in an attempt to distract the user from what is happening. The update will end in an error, but what is happening behind the scenes is of real interest.
The MSI installer drops two Matanbuchus DLL payloads, named "main.dll". These are dropped in two different locations and a scheduled task is created to maintain persistence across the system if the system reboots. Lastly, communication with the command and control server is established.
Only once communication to the command and control server is established will the malware instruct the server to load the Cobalt Strike beacon, enabling far wider exploitation potential for the attack.
Interestingly in May 2022, DSCO also detected similar Cobalt Strike Beacon activity from Matanbuchus. All previous analyses of the malware were focused on the first payload. It was not until DSCO published their findings that work on the beacon payload began in earnest.
Matanbuchus
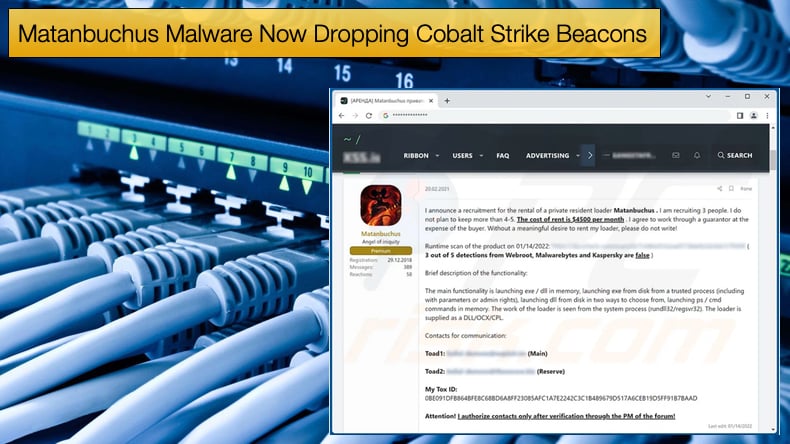
Much of the communities knowledge surrounding Matanbuchus can be attributed to the work done by Palo Alto Networks’ Unit 42. Researcher’s from the security firm noted that a user of an underground hacking forum who goes by the tag BelialDemon advertised a new malware-as-a-service (MaaS) called Matanbuchus Loader and charged an initial rental price of 2,500 USD.
Researchers noted that typically loaders are seen as malicious software that typically drops or second-stage malware from command and control infrastructures, to that extent Matanbuchus has the following features:
- The ability to launch a .exe or .dll file in memory.
- The ability to leverage schtasks.exe to add or modify task schedules.
- The ability to launch custom PowerShell commands.
- The ability to leverage a standalone executable to load the DLL if the attacker otherwise has no way of doing so.
In providing an overview of the malware researchers noted,
“Overall, Matanbuchus uses two DLLs during the malware’s run cycle. Both DLLs are packed, but it should be noted that the first DLL has an internal name of MatanbuchusDroper.dll while the second DLL is named Matanbuchus.dll. It’s not the stealthiest approach, but helpful to us nonetheless. Additionally, both DLLs are based at 0x10000000 and use hard coded addresses throughout execution.”
Further,
“The primary function of this first DLL is, as its name suggests, to drop the main Matanbuchus DLL. However, before that, it will make several API calls typically observed in anti-virtualization and anti-debugging checks, such as GetCursorPos, IsProcessorFeaturePresent, cpuid, GetSystemTimeAsFileTime, and QueryPerformanceCounter. These can profile a system to provide indicators to the malware that allow it to determine if it is running in a controlled environment (i.e. a sandbox).”
In many respects, Matanbuchus poses a threat to an organization's infrastructure. The inclusion of the ability to drop a Cobalt Strike beacon the more a possible threat is posed.
Currently, researchers are not sure in what way the beacon is leveraged but an attacker has several options from there, including data theft, credential theft, and a ransomware attack if they so wish.
Alternatively, the attacker who has now compromised the network can sell access to the compromised network to another attacker for whatever reason they deem fit.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion