Is Sodinokibi Back?
Security researchers have recently discovered possible links between the relatively new Ransom Cartel and an old foe of many a researcher, Sodinokibi. The latter is also tracked as REvil, a pioneer in how ransomware gangs changed tactics to target large corporations and demand millions in ransom payments.
The gang announced their retirement in October 2021, following several high-profile attacks on Kaseya, Acer, and attempts to extort Apple.
It wasn’t so much that these attacks were failures but rather governments, helpfully led by US policy decisions to target ransomware operators, their infrastructure, and their illegally gained cryptocurrency.
The combination of high-profile attacks and increased pressure from law enforcement are the likely contributors behind the decision to retire.
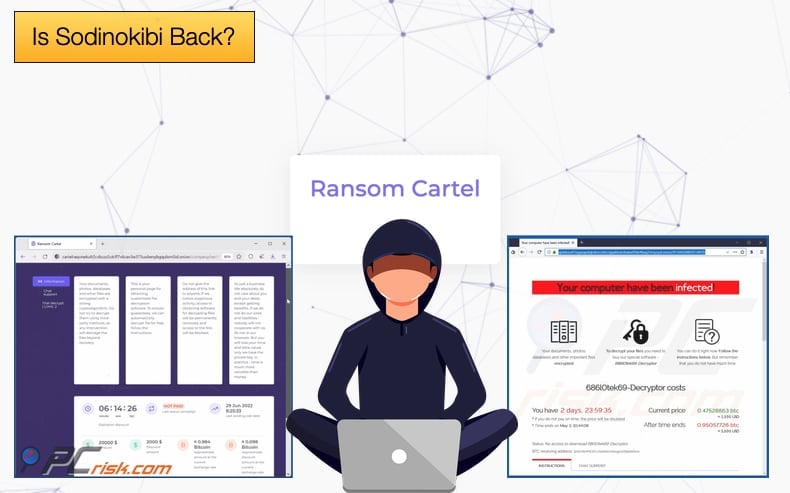
A few months after Sodinokibi’s retirement, Ransom Cartel showed up. In December 2021, security researchers discovered several similarities between Ransom Cartel and samples of Sodinokibi.
Now a new report by Palo Alto’s Unit 42 suggests that Ransom Cartel might just be a rebrand of Sodinokibi. In the report, researchers provide a brief overview of Ransom Cartel, noting,
“There are a number of theories about the origins of Ransom Cartel. One theory in the community suggests that Ransom Cartel could be the result of multiple groups merging. However, researchers at MalwareHunterTeam have put forward that one of the groups believed to have merged has denied any connection with Ransom Cartel. Additionally, Unit 42 has seen no connection between these groups and Ransom Cartel other than that many of them have connections to REvil…At this time, we believe that Ransom Cartel operators had access to earlier versions of REvil ransomware source code, but not some of the most recent developments (see our Ransom Cartel and REvil Code Comparison for more details). This suggests there was a relationship between the groups at some point, though it may not have been recent.”
Unit 42 first detected Ransom Cartel activity in January 2022, when the group began targeting organizations in the US and France. The group targeted organizations in the education, manufacturing, utilities, and energy economic sectors during this period.
Researchers noted that the group will look to gain initial access to a targeted network via compromised credentials including access credentials for external remote services, remote desktop protocol (RDP), secure shell protocol (SSH), and virtual private networks (VPNs).
All of which can be obtained by the ransomware operators through phishing operations or brute force attacks, as examples, or purchased from initial access brokers.
Initial access brokers can be defined as are actors who offer to sell compromised network access or partner with other threat actors that will deploy malware once access is granted.
Lastly, Ransom Cartel uses the double extortion tactics, now a common tactic amongst ransomware gangs, as well as encrypting both Windows and Linux VMWare ESXi servers in attacks on corporate networks.
Similarities between Sodinokibi and Ransom Cartel
The first similarity noted by Unit 42 researchers involves similarities in the configuration of the malware. Researchers noted,
“The first notable similarity between Ransom Cartel and REvil is the structure of the configuration. Examining a sample of REvil from 2019 (SHA256: 6a2bd52a5d68a7250d1de481dcce91a32f54824c1c540f0a040d05f757220cd3), the resemblance can be seen. However, the storage of the encrypted configuration is slightly different, opting to store the configuration in a separate section within the binary (.ycpc19), with an initial 32-byte RC4 key followed by the raw encrypted configuration, whereas with the Ransom Cartel samples, the configuration is stored within the .data section as a base64-encoded blob.”
Further, when both ransomware strains decrypt the configuration files they use the same JSON format to show and allow for easier data access.
However, the Ransom Cartel JSON functionality seems to lack features later Sodinokibi versions have. This could mean that either the Ransom Cartel developers removed certain functionality or they are building off of a much earlier version of Sodinokibi.
Secondly, both use an identical encryption scheme, generating multiple public and private key pairs, and creating session secrets using the same procedure found within Sodinokibi samples.
Researchers did note one important difference, stating,
“A particularly interesting difference between the two malware families is that REvil opts to obfuscate their ransomware much more heavily than the Ransom Cartel group, utilizing string encryption, API hashing, and more, while Ransom Cartel has almost no obfuscation outside of the configuration, hinting that the group may not possess the obfuscation engine used by REvil.”
It is most certainly too soon to say that the two ransomware strains are linked to the point that it is a rebrand. There are certainly strong links between the two strains, however, at this point, it would seem that Ransom Cartel has access to Sodinokibi source code.
What’s more, is that based on the evidence presented in Unit 42’s report Ransom Cartel are working off an older version of Sodinokibi than versions seen distributed before their retirement.
Does this mean that Ransom Cartel will be demanding 50 million USD in ransoms soon like their inspiration did before retiring? It is unlikely, but it is clear that threat actors see that ransomware can still be incredibly profitable.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion