Sodinokibi Retired...Again
In what is writing itself into its own Netflix Original movie at this point, it appears Sodinokibi, also tracked as REvil, infrastructure has been taken offline for the second time this year. The news comes following statements made on the popular hacking forum XSS. The forum posts have been shared to Twitter by Dmitry Smilyanets, a security researcher for Recorded Future. Another post was also shared by Smilyanets which further explained the decision to take the infamous ransomware’s infrastructure offline.
The posts were published by “0_neday” a known high-ranking operator behind Sodinokibi. The operator explained that along with another operator, who went by the moniker “Unknown”, were the only two individuals who had access to the ransomware’s domain keys. "Unknown" then disappeared in July, leaving the other members of the group to assume he died.
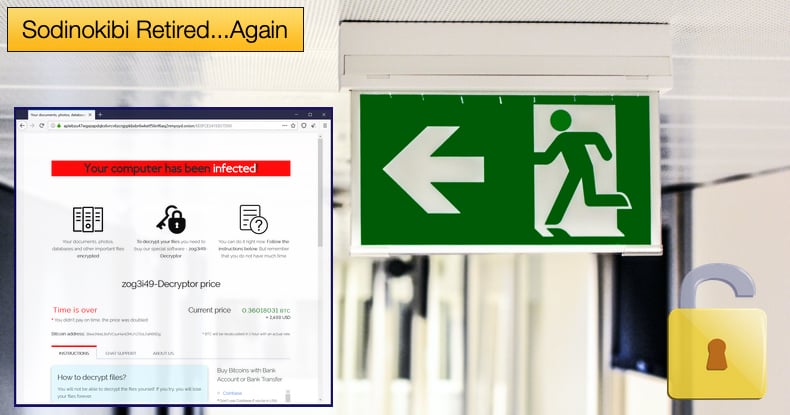
The group resumed operations in September, but this weekend, “0_neday” wrote that the Sodinokibi domain had been accessed using the keys of "Unknown." In a separate post, “0_neday” stated,
“The server was compromised, and they were looking for me. To be precise, they deleted the path to my hidden service in the torrc file and raised their own so that I would go there. I checked on others -- this was not. Good luck, everyone; I'm off.”
The first time the infrastructure was taken mysteriously offline was in the same month that “Unknown” disappeared. This was also the time when Sodinokibi operators had just struck with the Kaseya incident, where the gang demanded a massive 70 million USD in ransom. The attack further impacted hundreds of organizations that made use of Kaseya’s services.
The attack resulted in increased pressure on law enforcement agencies to crack down on ransomware gangs which in turn resulted in pressure on Sodinokibi operators to cease operations and as one theory goes, some believed law enforcement responsible for the takedown of infrastructure.
However, it emerged that Unknown allegedly stole the gang’s earnings and shut down the infrastructure. This meant that affiliates could not be paid severely impacted the reputation of the ransomware key operators and developers. Affiliates are unlikely to take the legal risks they do if the chances of being paid are slim to zero.
In September 2021, Sodinokibi operators minus the now even more mysterious “Unknown” attempted to reboot operations to what now appears to be, very limited, success, as the infrastructure has again been taken offline approximately a month later.
The reason for being taken offline now is because of the server compromise alluded to in the posts by “0_neday”. Speaking to ZDNet, Allan Liska, a ransomware expert with Recorded Future, presented two theories to help better explain the latest retirement, stating,
“Unknown (the former leader of REvil) 'returned from the dead' and was not happy that his software developers were trying to push his ransomware. The second is that a government agency managed to penetrate the server before they closed shop the first time, got Unknown's private key and decided to take these new actors down,”
And,
“Normally, I am pretty dismissive of 'law enforcement' conspiracy theories, but given that law enforcement was able to pull the keys from the Kaseya attack, it is a real possibility. The relaunch of REvil was ill-conceived from the start. Rebranding happens a lot in ransomware after a shutdown. But no one brings old infrastructure that was literally being targeted by every law enforcement operation not named Russia in the world back online. That is just dumb.”
Liska believes that the controversy surrounding Sodinokibi’s could very well be legitimate. This might be the case as there is a lot of money to be made in ransomware currently and any reason not to pay affiliates will result in drama of one sort or the other.
However, to think those involved in the ransomware’s distribution will stop looking to make money via this specific type of malware would be naive. As we have seen in the past, affiliates will offer their services to other ransomware gangs adopting the ransomware-as-a-service business model.
Also speaking to ZDNet, Sean Nikkel, Digital Shadows senior cyber threat intel analyst, provided another theory as to what helped contribute to Sodinokibi’s multiple retirements, saying,
“Reaction to the news from other forum members ranged from largely unsympathetic to bordering on conspiracy theory. The main area of debate was whether the group would rebrand for a third time, with many questioning whether the cybercriminal community would still trust REvil-related schemes...One theory doing the rounds posited that a disgruntled former team member, combined with poor password hygiene, could have resulted in the attack...The XSS representative for the LockBit ransomware group claimed to have predicted this turn of events, providing links to their 'prophetic' forum posts. They questioned the REvil representative's intention to leave the forum, opining 'if the domains have been hijacked, this is 100% proof that someone had a root on the server, which means that your database has been leaked too.' The LockBit representative even put forward the idea the new REvil forum account may, in fact, be operated by law enforcement,”
Law Enforcement’s Role
Nikkel’s information shared with ZDNet does raise some interesting questions as to the role of law enforcement or even the potential role in helping bring down Sodinokibi. While much of it can be attributed to conspiracy theory bandied about Internet forums used by hackers, it is true law enforcement was under pressure to respond to attacks.
In the fallout of the Kaseya incident, the Washington Post revealed the Federal Bureau of Investigation (FBI) was in possession of decryption keys that could be used by victims to get access to their data back but failed to distribute them. It is believed that these keys were attained by FBI agents who managed to get access to Sodinokibi’s servers.
One theory circulating the Internet is that the FBI held onto the decryption keys as they were preparing to attack Sodinokibi’s infrastructure and feared by releasing the keys the operation could be jeopardized. The US Congress demanded a briefing from the FBI as to why the keys were not released to victims to what some may see as limited success.
During the hearing FBI Director Christopher Wray laid the blame for the delay on other law enforcement agencies and allies who they said asked them not to disseminate the keys. He said he was limited in what he could share about the situation because they are still investigating what happened. Wray further noted that,
“We make the decisions as a group, not unilaterally. These are complex...decisions designed to create maximum impact, and that takes time in going against adversaries where we have to marshal resources not just around the country but all over the world. There's a lot of engineering that's required to develop a tool,”
Other information suggests that law enforcement might not have had a hand in Sodinokibi’s downfall. It was reported that Sodinokibi’s developers included a secret backdoor into the malware that could be used to scam its own affiliates.
It was proposed that the backdoor could allow developers and operators to negotiate directly with victims and restore encrypted data without the input from the affiliate who compromised the victim. If true, operators could pocket the entire ransom without having to share it with affiliates. Even if not true the fact that it might be a possibility can cause irreparable damage to the reputation of Sodinokibi’s developers.
This information further muddies the water as to what exactly caused Sodinokibi’s infrastructure to be taken offline again. The truth is we may never know but we have been provided with interesting insights as to how ransomware-as-a-service models operate and that they are susceptible to being sunk by greed or law enforcement.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion