Phishing-as-a-Service Platform Gets an Upgrade
Robin Banks, the popular phishing-as-a-service (PaaS) platform amongst the cybercriminal underground, has resurfaced after previously having its backend and frontend rendered useless by Cloudflare. Now the platform has found a new hosting partner based in Russia that boasts distributed-denial-of-service (DDoS) protection for customers. The hosting partner, DDOS-GUARD, has also been linked to hosting QAnon, 8Chan, and Hamas web assets.
Cloudflare’s operation to blacklist Robin Bank’s infrastructure was completed in July 2022. Up until that point the criminal service had targeted the following banking institutions: Citibank, Bank of America, Capital One, Wells Fargo, PNC, U.S. Bank, Santander, Lloyds Bank, and the Commonwealth Bank.
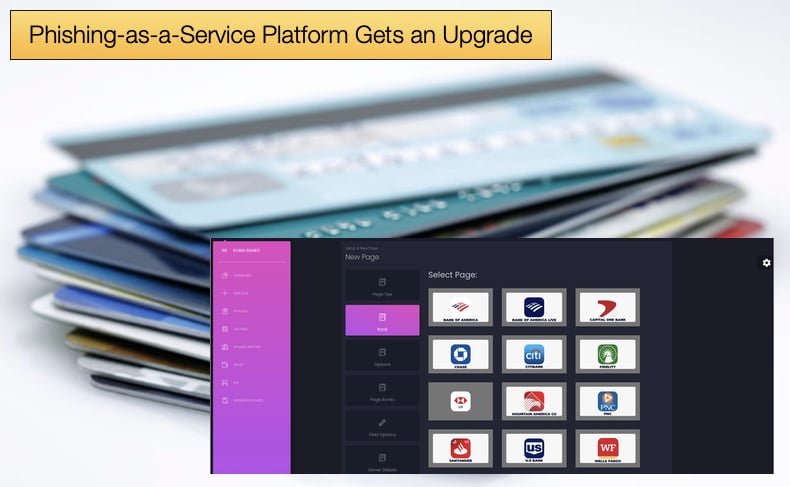
Now according to a new report by IronNet, it appears those behind the PaaS have taken new steps to keep their operation behind closed curtains and prevent researchers from uncovering the new upgrades.
Perhaps the most important new features are the added ability to bypass multi-factor authentication (MFA) and the use of a redirector to avoid detection.
Summarising both why these upgrades were done IronNet researchers noted,
“In addition to migrating its infrastructure to DDOS-GUARD, Robin Banks also started enforcing increased security on the platform, most likely out of fear someone might hack their admin interface. This included implementing and requiring two-factor authentication (2FA) in order for kit customers to view phished information via the main GUI. However, if they did not want to implement 2FA, the customers could instead opt to have the phished information sent to a Telegram bot rather than access it through the Robin Banks GUI.”
And,
“There were also attempts by Robin Banks developers to make information about the platform and its customers’ activities harder to access. In order to privatize admin conversations surrounding the platform, Robin Banks administrators moved to create a separate private Telegram channel, where IronNet analysts observed disagreements between platform admins about poaching customers from other platforms. During that disagreement, one of the admins became angered and made the private channel public, which effectively exposed their legacy Telegram communications and caused both their main and private channels to become spammed with unrelated cybercriminal content.”
As with the previous incarnations, Robin Banks is heavily reliant on open-source tools and off-the-shelf tools favored by financially motivated hackers.
One such tool is PHP Obfuscator, which is easily downloaded from Github. The tool is used to render code incredibly difficult for humans to read by adding in dummy text intended to hide the bits of the code that carry out malicious operations. This is done primarily to help prevent analysis by security researchers.
Another third-party tool used by Robin Banks is Adspect, which is advertised as a third-party cloaker, bot filter, and ad tracker. PaaS services have come to appreciate Adspect as a redirector to evade detection.
This is a far cry from the intended purpose of using artificial intelligence to detect and filter unwanted visitors in web traffic. Malicious actors discovered that Adspect could be used to redirect potential targets to malicious websites.
That is only part of the cunning scheme as web scanners used to uncover malicious traffic are then redirected to non-malicious websites making the phishing campaign harder to detect.
This is done by Robin Banks through a process known as Forward PHP integration. This technique involves placing a specific index.php file in a landing page directory or any other place accessible via HTTP.
The PHP file acts as the entry point for the website and decides the execution flow as it's linked to Adspect’s servers. Going into greater detail on how Adspect is abused by Robin Banks researchers by referring to Adspect’s website, noted,
“On its official site, Adspect also provides best practices and coaching to customers on how to drive legitimate targets to “money sites” (i.e. phishing sites) while filtering out automated scanners/bots to safe pages. The platform is very careful with wording as to not use the word phishing; however, IronNet analysts have observed their services being advertised via known phishing channels on Telegram and TOR sites.”
Credential Stealing
The biggest upgrade to Robin Banks is how it bypasses MFA to steal credentials. This is done by yet another third-party tool called Evilginx2. This tool acts as a reverse proxy to conduct adversary-in-the-middle (AiTM) attacks to steal cookies containing authentication tokens.
This is done by establishing a communication link between the victim and the real service’s server. Then login requests and credentials and captured by intercepting the session cookie in transit.
This helps the phishing actors bypass the MFA mechanism because they can use the captured cookies to log into an account as if they were the owner. Robin Banks sells this new MFA-bypassing feature separately and advertises that it works with Google, Yahoo, and Outlook.
IronNet researchers concluded that Robin Banks's reliance on third-party tools is a clear showing of how low the barrier to entering into cybercrime is.
Now even the starting of a malware-as-a-service platform can be done without the need to write masses of code and develop custom malware payloads.
Researchers also concluded that while the barrier to entry is low, the market is likely to become oversaturated, leading some malware developers to step up their game to create custom tools harder to detect to carve out a larger market share.
This will result in some operations becoming harder to detect and stop while others will fall by the wayside if they continue to rely on third-party tools that will be easier to detect.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion