New Post-Exploit Kit Linked to LockBit
For many of the readers of this publication they will be aware of the heyday of exploit kits, effective toolsets to take advantage of vulnerable software packages. When Adobe’s Flash and Microsoft’s Internet Explorer had significant market dominance these toolkits were far more common and used to gain access to victims’ machines.
With advancements in browser engines and software companies improving security practices, the use of exploit kits died down. Security researchers still encounter them but their popularity has waned. However, the idea of providing hackers with a digital Swiss Army knife never went away.
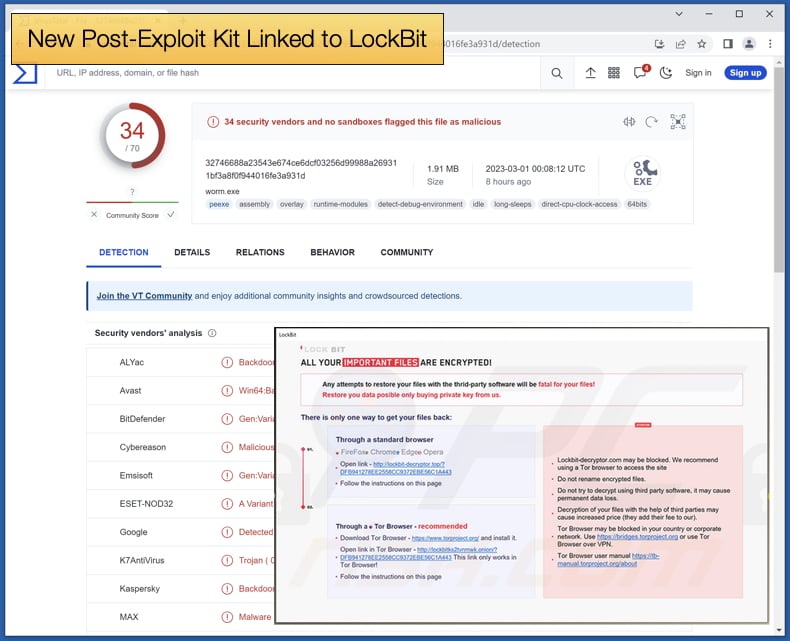
So enters the post-exploit kit, the toolkit to deploy once initial access is gained and the threat actor needs to facilitate communications between the victim’s infrastructure and the command-and-control server, look to escalate privileges, evade detection, and drop other malware payloads including ransomware. Enter Exfiltrator-22, also known as Ex-22, to provide threat actors with such a service in one neat package but for a cost.
In a recently published report by CYFIRMA, details of Exfiltrator-22 have been released to the public since its discovery in late 2022. Security researchers for the security firm discovered that the development of the post-exploit kit, or at least the first version thereof, was completed on November 27, 2022.
Soon after that, on December 7, 2022, the threat actor created a telegram channel to advertise the malware, to attract prospective buyers. At the time of the report writing, only 5 of 70 malware engines on Virus Total detected the toolkit as malware.
Commenting on the pricing structure researchers noted that,
“In January 2023, an official announcement was made on their channel to keep prospective buyers updated on the progress. It was stated that Ex22 is 87% ready for use and the payment model will be subscription based ($1000 for a month and $5000 for lifetime access). Upon purchase, the buyer would be given a login panel to access the Ex22 server, hosted on a bulletproof VPS (Virtual Private Server).”
The Virtual Private Server (VPS) allows threat actors to bypass the laws or terms regulating Internet content and used services in their geographical regions. The VPS is not just for bypassing regional laws but serves the very important function of controlling the framework's malware and issuing commands to compromised systems.
The malware developer has even created a YouTube channel to provide tutorials on how to use the malware effectively, including videos on how to use the malware for lateral movement across the victim’s network and how to deploy ransomware.
The malware has several other noteworthy features neatly summarised by Bleeping Computer, these include:
- Establish a reverse shell with elevated privileges.
- Upload files to the breached system or download files from the host to the C2.
- Activate a keylogger to capture keyboard input.
- Activate a ransomware module to encrypt files on the infected device.
- Capture a screenshot from the victim’s computer.
- Start a live VNC (Virtual Network Computing) session for real-time access on the compromised device.
- Gain higher privileges on the infected device.
- Establish persistence between system reboots.
- Activate a worm module that spreads the malware to other devices on the same network or the public internet.
- Extract data (passwords and tokens) from the LSAAS (Local Security Authority Subsystem Service).
- Generate cryptographic hashes of files on the host to help closely monitor file locations and content change events.
- Fetch the list of running processes on the infected device.
- Extract authentication tokens from the breached system.
Link to LockBit 3.0
Upon analysis of the sample attained by CYFIRMA, security researchers discovered several links to the LockBit 3.0 strain. Researchers discovered that the framework uses the same "domain fronting" technique associated with the LockBit and the TOR obfuscation plugin Meek, which helps hide malicious traffic inside legitimate HTTPS connections to reputable platforms.
Domain fronting is when threat actors use different domain names in the Server Name Indication (SNI) field of the TLS header and the Host field of the HTTP host header.
This technique also helps those in regions where the Internet is heavily censored to bypass censorship laws. Malicious threat actors use the technique to mask traffic from the command-and-control server to the victim’s machine and vice versa.
This similarity in the use of the domain fronting technique prompted researchers to dig a little deeper. It was discovered that both Exfiltrator-22 and LockBit 3.0 were using the same command-and-control infrastructure that was being used by LockBit 3.0. Researchers further concluded that
“It can be concluded with high confidence that the threat actors who created EX-22 are highly sophisticated threat actors that are likely to continue to increase the evasiveness of the malware. With continuous improvements and support, EX-22 becomes a go-to alternative for any threat actors planning to purchase tools for the post exploitation phase but do not want to go with the traditional tools due to high detection rates. "
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion