Phishing Campaign Targeting Eastern Europe Delivers Remcos RAT Malware
Security firm Sentinel One just published a report detailing how a phishing campaign used to target victims in Eastern Europe is being used to deliver the Remcos RAT and DBateLoader malware strains. As with so many malware distribution campaigns, things kick off with a phishing email campaign, in this instance a fake invoice sent from already compromised email accounts.
As for the phishing email campaign the malicious attachments included tar.lz archives that typically masquerade as financial documents, such as invoices or tender documentation.
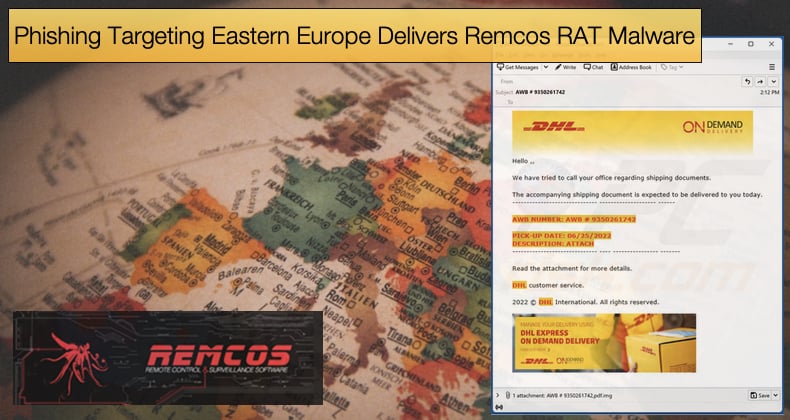
The emails were typically sent to the sales departments of targeted enterprises or the main contact email addresses that can be found easily online. Researchers further noted,
“Many of the phishing emails we observed have been sent from email accounts with top-level domains of the same country as where the target is based. These emails typically do not contain any text accompanying the malicious attachment or contain text written in the language of the target’s country. In the cases where the threat actors are not masquerading the phishing emails as originating from an institution or business organization local to the target, the emails contain text written in English.”
If the receiver of the malicious email would likely unzip the archive and open the executable contained within masquerading as an invoice. If this is done the attack chain begins the next phase of initializing the malware payloads.
As the archive file contains files masquerading as Microsoft Office, LibreOffice, or PDF documents using double extensions and/or application icons, the attackers hope the charade will lend the email enough authenticity.
Along with the fact that the email came from a compromised but possibly trusted private email account, to keep suspicion low and the chances of compromising the receiver's machine high.
If the executable is initiated DBatLoader downloads and executes an obfuscated second-stage payload data from a public Cloud location. We observed download links to Microsoft OneDrive and Google Drive sites.
These sites had varying life spans, the longest of which was more than one month, this is often done by threat actors to help secure operational security for the campaign and make detection and analysis harder. It was noted by researchers that,
“The Cloud file storage locations that were active while we investigated contained only the second-stage DBatLoader payload data and were registered to individuals. We have no knowledge at this point whether the threat actors have been using self-registered and/or compromised Microsoft OneDrive and Google Drive credentials to host DBatLoader payload.”
Mock Folder Technique
One of the more interesting aspects of the campaigns attack chain is the use of creating “mock folders” to bypass Windows User Account Control (UAC), a security feature of the operating system to help mitigate malware infections and helps to prevent malicious actors from getting administrator rights and privileges.
However, if bypassed successfully threat actors can gain those rights and privileges to drop malware on the victim’s machine. This technique, which involves a simplified process of DLL hijacking and mock directories, to gain escalated privileges without alerting the end user, was discovered in 2020.
A mock directory, or mock folder, is simply an imitation of an existing directory just with a trailing space. For example, whereas "C:\Windows\System32" is a legitimate, trusted location on Windows machines, a mock directory would look like "C:\Windows\ System32", pay careful attention to the trailing space after “Windows\”.
What makes this a dangerous precedent is that certain aspects of the operating system will treat the mock directory as a trusted and legitimate source bypassing UAC and not informing the victim that they are about to give a high-risk application elevated privileges. The elevated privileges are automatically bestowed on the application.
In the case of DBatLoader in campaigns seen in the wild, researchers noted,
“The malware then creates and executes an initial Windows batch script in the %Public%\Libraries directory. This script abuses a known method for bypassing Windows User Account Control that involves the creation of mock trusted directories, such as %SystemRoot%\System32, by using trailing spaces. This enables the attackers to conduct elevated activities without alerting users.”
Once this process of bypassing UAC is completed DBatLoader will establish persistence on the victim’s machine by copying itself into the %Public%\Libraries directory and creating an autorun registry key under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
Once persistence is achieved the malware will then look to drop the REMCOS Rat through process injection on the now thoroughly compromised machine.
To help defend against this attack campaign Sentinel One advises administrators to monitor network requests to public Cloud instances and determine if they are malicious or not.
Further, administrators are asked to monitor for suspicious file creation activities in the %Public%\Library directory and process execution activities that involve filesystem paths with trailing spaces, especially \Windows \.
Lastly, it is advised to configure Windows UAC to the “Always notify” setting. This will always alert users when a program attempts to make changes to the machine in question.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion