Security Researchers Discover The Fastest Known Ransomware Variant Rorschach
In a recently published report by security firm Check Point, a newly discovered ransomware is breaking new records for the fastest encryptor. That might be the headlining grabbing feature of Rorschach, but the malware’s developers have looked to use the best features from several other variants to create a frightening foe for those tasked to defend IT infrastructure.
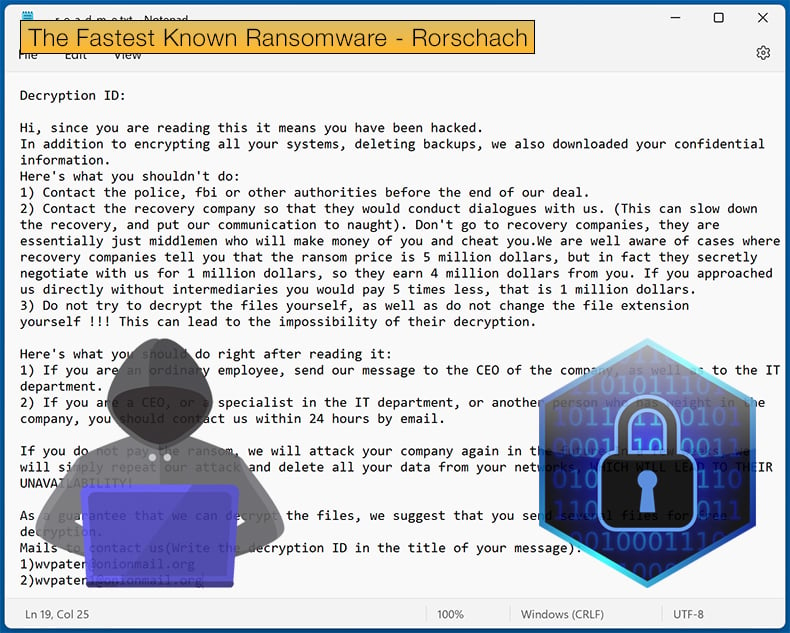
Rorschach was discovered when Check Point researchers responded to a ransomware incident that impacted a US-based company. Researchers soon determined that the threat actor did not hide behind any alias and appeared to have no affiliation with any known ransomware groups.
Which, according to Check Point, is a rarity begging for further analysis, with researchers noting,
A behavioral analysis of the new ransomware suggests it is partly autonomous, spreading itself automatically when executed on a Domain Controller (DC), while it clears the event logs of the affected machines. In addition, it’s extremely flexible, operating not only based on a built-in configuration but also on numerous optional arguments which allow it to change its behavior according to the operator’s needs. While it seems to have taken inspiration from some of the most infamous ransomware families, it also contains unique functionalities, rarely seen among ransomware, such as the use of direct syscalls.
The treat actor in the instance discovered by researchers was infected with Rorschach following the threat actor successfully leveraging a weakness in a threat detection and incident response tool.
This suggests the threat actor is experienced and understands not only how corporate networks are set up and maintained by the security tools that watch over the infrastructure as a whole.
In this specific case, researchers found that the ransomware was deployed using the DLL side-loading technique via a signed component in Cortex XDR, the extended detection and response product from Palo Alto Networks.
The Cortex XDR tool was used to side-load the Rorschach loader and injector (winutils.dll), which led to the launching of the ransomware payload, “config.ini.” The ransomware payload itself was launched via a Notepad process. Interestingly, ransomware looks to evade security solutions in a novel way.
Researchers noted that,
Although Rorschach is used solely for encrypting an environment, it incorporates an unusual technique to evade defense mechanisms. It makes direct system calls using the “syscall” instruction. While previously observed in other malware strains, it’s startling to see this in ransomware.
The procedure involves utilizing the instruction itself, and it goes as follows:
- The ransomware finds the relevant syscall numbers for NT APIs, mainly related to file manipulation.
- Rorschach then stores the numbers in a table for future use.
- When needed, it calls a stub routine that uses the number directly with the syscall instruction instead of using the NT API.
Likewise, Rorschach also employs novel self-propagation methods, with researchers noting that when executed on a Windows Domain Controller (DC), the ransomware automatically creates a Group Policy, spreading itself to other machines within the domain.
Encryption Done In Record Time
To say that Rorschach employs a highly effective encryption routine may be an understatement. The routine cleverly combines the curve25519 and eSTREAM cipher hc-128 algorithms for encryption. Ultimately, the routine is used to only encrypt a portion of the file rather than the file in its entirety.
Then the WinAPI CryptGenRandom is utilized to generate cryptographically random bytes used as a per-victim private key. Check Point researchers noted that the shared secret is calculated through curve25519, using both the generated private key and a hardcoded public key.
For those wanting more information regarding the encryption routine and want to dive deep into the minutiae, the computed SHA512 hash of the shared secret is used to construct the KEY and IV for the eSTREAM cipher hc-128.
To further improve the encryption routine’s efficiency, also a highly effective implementation of thread scheduling via I/O completion ports. Moreover, it appears that the malware developer had speed in mind in building the compiler, as optimization is prioritized for speed, with much of the code being inlined.
While the encryption routine is impressive, it is Rorschach borrowing of things that worked from other ransomware operations that can make it a hard foe to deal with.
According to the analysis done by Check Point, it was noted that the encryption routine had been borrowed from the leaked source code of Babuk ransomware. This inspiration goes as far as to inspire Rorschach’s various routines, including those responsible for stopping processes and services.
Further, inspiration has been taken from another source, LockBit 2.0, with researchers noting the list of languages used to halt the malware is the same list that was used in LockBit v2.0, this in itself is no smoking gun as many ransomware families have effectively plagiarised LockBit 2.0 exclusion list.
Researchers argue that the I/O Completion Ports method of thread scheduling during encryption is another component where Rorschach took more inspiration from LockBit 2.0.
Researchers concluded,
Our analysis of Rorschach reveals the emergence of a new ransomware strain in the crimeware landscape. Its developers implemented new anti-analysis and defense evasion techniques to avoid detection and make it more difficult for security software and researchers to analyze and mitigate its effects… The operators and developers of the Rorschach ransomware remain unknown. They do not use branding, which is relatively rare in ransomware operations.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion