Superfish May Be Just the Tip of the Iceberg for Adware Privacy Concerns
Last week this blog reported a story about Lenovo, one of the world’s largest manufacturers of PCs and tablets, and how the company has been installing adware on its products at the factory. This adware, dubbed Superfish, is designed to intercept encrypted Web connections relying on SSL technology. Unfortunately, a flaw in the program design allows hackers to intercept these transmissions in the form of a man-in-the-middle attack – potentially putting the secure personal information of millions of PC users at risk. Discovery of Superfish has already landed Lenovo in hot water.
The company has already released a statement that Superfish is no longer being installed on new PCs (as of January 2015) and instructions on Lenovo’s website teach customers how to remove Superfish from existing Lenovo products. A lawsuit has already been filed against the PC manufacturer in the wake of the Superfish discovery, although it will be months (possibly even years) before a verdict is reached in that case. The point of this article, however, is not Superfish.
It seems that Superfish is one of over a dozen similar products that are being used by assorted software makers to intercept encrypted network traffic.
All of these products can be traced back to a single manufacturer who creates and sells the technology responsible for this privacy breach. That company is called Komodia. Komodia is a small IT tech firm established in 2000. Its two most popular products (both network interception tools) are known as Redirector and SSL Digestor. These products are sold to software manufacturers who embed them into software code as a way to provide custom advertisements to customers using these software products. Komodia’s products work by installing a root certificate-authority (CA) certificate on the OS which has the ability to intercept network traffic.
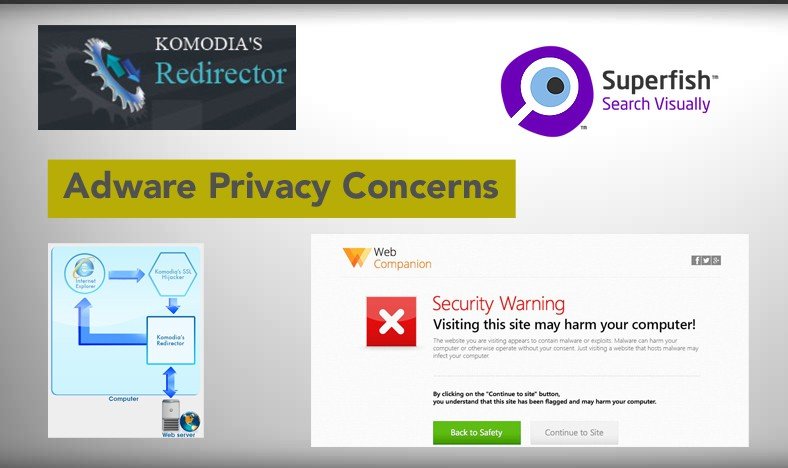
Although certainly an invasion of privacy for users of products leveraging this technology, the real problem is that the certificates used are poorly secured. This means that hackers can easily intercept the encrypted traffic and either simply view the information or even modify it as necessary to carry out cyberattacks. Although a complete list of products using Komodia technology has yet to be compiled, it is known that several parental control products, anonymizing software, and Web filtering products all contain these faulty CA certificates. Another product known to contain SSL Digestor is the popular Ad-Aware Web Companion, a product of security software company Lavasoft.
Even in Lavasoft’s most recent iteration of this product in which the company states that SSL Digestor was removed, security researchers have found trace elements of the code still present (although it is unclear at this time if these code fragments are functional).
It appears that Superfish is one of only many products that is endangering the safety of consumers for the financial gain of the software manufacturers. The only way to protect yourself from these threats is to check the operating system for unrestricted private root CA certificates. These certificates should be carefully removed from the system along with any software products associated with them to ensure the integrity of secure HTTPS sessions.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion