The Line between Legit Websites and Phishing Scams Grows Thinner
The Internet is a dangerous place and it seems like every day a new threat is discovered that could put your personal and financial data at risk. One of the most popular ways cybercriminals accomplish this is through a technique known as phishing. Phishing is a type of cyberattack whereby hackers create a fake website (known as a spoofed website) that is designed to look exactly like a legitimate online service. Popular online services such as Bank of America and PayPal are common targets for these types of attacks. When the victim unknowingly enters sensitive account information on the spoofed website, the hackers receive this information and can use it to fraudulently make wire transfers or as part of an identity theft campaign. The last few years have brought about significant changes in the way the Internet works and many of these changes are a direct response to the rising costs associated with successful phishing campaigns.
These changes have made detection of phishing websites much faster and more accurate but it still isn’t enough. As usual, the criminals behind these attacks find new ways to circumvent the protections put in place to limit the risk of phishing and one of the newest techniques to be discovered makes it even more difficult to discern a spoofed website from its legitimate counterpart. Netcraft, a UK-based network security company, recently reported that cybercriminals have started to exploit weaknesses in technology companies in an effort to make their spoofed websites look more legit.
Specifically, hackers are leveraging the power and perceived security that comes with the use of SSL/TLS certificates. These certificates are used by legitimate companies as a way to verify the domain name of the website and to encrypt the communications between the user and online service.
These certificates are indicated in most modern Web browsers using a green padlock next to the website URL and most Internet users have become accustomed to looking for this symbol before entering any sensitive information (such as a credit card number or bank account login information). The digital certificates that create that green padlock icon are issued by companies known as Certificate Authorities (CAs) and according to Netcraft, major CAs including GoDaddy, Symantec, Comodo, and CloudFlare have been issuing digital certificates to hackers attempting to make their phishing websites appear more legitimate. It’s bad enough that hackers are able to obtain these SSL/TSL certificates in the first place but according to Netcraft, the blame mostly falls on the CAs for not spending the extra time to vet potentially sketchy domains before issuing digital certificates to these cybercriminals.
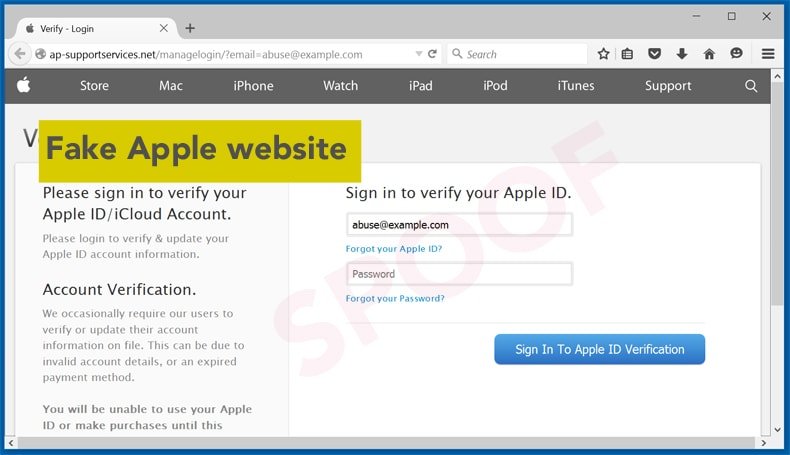
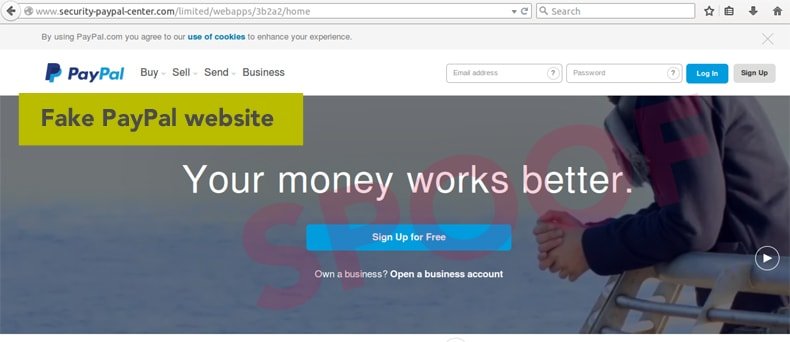
In just the last few months, domains including banskfamerica.com and emergencypaypal.net have been issued digital certificates despite the obviously deceptive domain names. When a visitor lands on one of these spoofed websites, the presence of a digital certificate may lead many people to enter personal information because aside from the domain name being a little bit different, everything else appears normal – up to and including the presence of the little green padlock in the corner. This is a problem that appears to be growing all the time. In a recent blog post by Graham Edgecombe, an Internet Services Developer with Netcraft, the problem is made quite clear.
According to Edgecombe’s research, in must one month, hundreds of digital certificates were issued to deceptive domain names used in phishing campaigns. There are multiple types of digital certificates available with the least expensive of these being a Domain Validated, or DV, certificate. DVs are often free or at most, cost less than $10 each. These certificates are issued once a CA has verified that the applicant controls the intended domain name and since these systems are mostly automated, it is the certificate that most phishing websites seek to obtain. More expensive certificates are available but these certificates require that the CA do a much more thorough investigation prior to issuing the certificate. Nonetheless, a DV still provides the website with the green padlock which is all the criminals behind these attacks are looking for in the first place.
It’s worth pointing out that CAs are supposed to perform additional verification on potentially high-risk domain names such as those listed above but the CAs aren’t actually performing these additional steps when they should be.
In many cases, the CA simply sends an email to the domain administrator on record to verify domain ownership before issuing the certificate so all a cybercriminal needs to do to validate a phishing website is respond to the verification email. While many of the CAs that are guilty of issuing certificates to rogue websites had no comment when confronted with Netcraft’s findings, Comodo CEO Melih Abdulhayoglu admitted in an emailed statement that Comodo has “the largest share of the problem” because it is the largest CA in the world. Comodo revokes rogue DV certificates once the company is made aware that the site is part of a phishing scam, but that usually means people have fallen victim to the attack before it gets reported in the first place.
To avoid the risks associated with issuing DV certificates, many CAs simply do not offer DVs at all. Entrust and DigiCert are both US-based CAs that refuse to issue DVs because of security concerns. According to Entrust’s website: "Although the domain validated certificate supports transaction encryption, the end user cannot trust the certificate to confirm who is on the other end." The morale of the story is simple: do not trust a website simply because a valid SSL certificate is present.
The best way to ensure that you always get to the legitimate website you seek is to manually type in the URL (i.e. do not follow embedded links within emails) and verify that the address displays properly in the URL bar before entering any personal information. Remember that a phishing website is designed to trick people so a rogue domain name might only be one or two letters off from the legitimate site but that’s all it takes to get caught in a phishing scam and if you’re not careful, you could put your sensitive data on a proverbial silver platter for cybercriminals who want nothing more than to take everything they can from you as quickly as possible.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion