New Malware Strain Completely Replaces Chrome to Circumvent Improved Security
Over the last few years, malware creators have been moving away from traditional malware attacks that target the Windows OS; instead relying on malware specifically designed to infiltrate popular Web browsers. In most cases, the browsers are exploited via known vulnerabilities in common Web browser plugins including Adobe Flash Player, Microsoft Silverlight, and Java. Once a browser has been infected with malicious software, the cybercriminals behind these campaigns have almost limitless access to the PC and any future browsing sessions performed in the affected browser. In response to the increased threat presented by browser-specific malware, browser developers have had to change (radically in some cases) the way security within the browser application is handled. As hackers get better at hiding their malicious applications by using legitimate-sounding file names that have been carefully hidden in obscure directories, browser developers have discovered new ways to locate and quarantine infected code as quickly as possible. Active detection technology and providing a way for browser users to easily disable browser plugins that could put the PC at risk when not needed have made it increasingly difficult for cybercriminals to profit from these “traditional” browser-specific attack vectors. In response to the improved security of popular Web browsers, one group of hackers recently devised a new technique that specifically targets the Chrome Web browser.
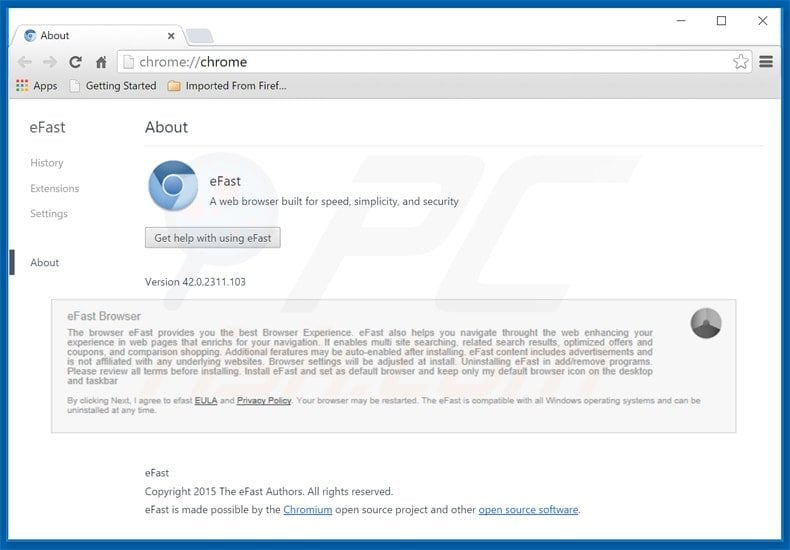
Rather than try to sneak past some of the new and robust security features of the popular Web browser, these criminals created a rogue copy of Chrome that almost looks legitimate despite a few small differences. If a victim doesn’t realize that the browser they are using is an imposter, the cybercriminals responsible for this campaign can control many aspects of a victim’s Web browsing session without detection while simultaneously tracking the victim’s movements across the Web. This new malware variant, known as eFast, is a powerful piece of malicious software that silently installs itself on the target machine and promptly replaces the legitimate Chrome browser. The malware replaces all shortcuts and links to Chrome within Windows and even tries to completely delete Chrome from the machine. The eFast browser also ensures that all Windows file extensions are changed so process and file calls to the default Web browser open the rogue instance of Chrome instead of the real browser.
The hackers behind this campaign have not yet been identified but the eFast Browser is purportedly the product of a company called Clara Labs. Whether or not Clara Labs is a legitimate business is still under investigation as a link to the company’s privacy policy does not load, instead prompting users with a malware warning message. In any event, these criminals were able to almost exactly mimic the look and feel of the Chrome browser by basing the code on the open source version of the Web browser, officially known as Chromium.
While veteran Chrome users may notice subtle differences in the browser icons that could indicate an eFast infection has occurred, most Internet surfers won’t notice the difference because the rogue version of Chrome seems the same as the legitimate version it replaced.
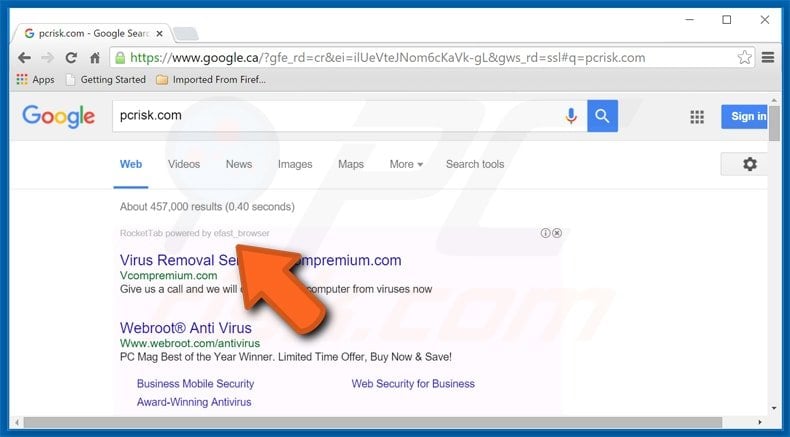
The tell-tale signs of an eFast infection, on the other hand, aren’t quite so easy to overlook. Victims infected with this malware variant will immediately begin to notice a large amount of pop-up advertisements and website redirections (this is when a victim attempts to navigate to a specific webpage but code written into eFast changes the URL to one chosen by the hackers launching this attack).
Website redirections are often used by hackers as a way to send traffic to websites hosting malicious content including banking Trojans and other dangerous forms of modern malware. If your PC begins to exhibit these behaviors, the best way to confirm infection is to open the advanced settings in the rogue version of Chrome and look for malicious extensions. If no malicious extensions are displayed but the browser continues to act in a strange manner, the PC is likely infected with this potentially dangerous malware threat and immediate action should be taken to mitigate any damages that may occur from the devious tactics that characterize the fake browser. At the time of this writing, eFast hasn’t been linked with any other noteworthy malware or spam campaigns so the exact intentions of this campaign remain unclear.
What is apparent is that a dangerous malware variant like this, capable of completely replacing one of the most popular Web browsers in the world without the knowledge or consent of the victim, could be used for any number of malicious cybercrimes ranging from identity theft, bank fraud, and DDoS attacks with very little additional effort required of the hackers.
Only time will reveal what the true purpose of eFast is and until antivirus definitions can be updated to detect eFast at the time of installation, an infected PC could be exposing the sensitive personal information of the victim to hackers in an unknown part of the world. Fortunately, the eFast threat does have a silver lining in that the rogue Web browser is relatively easy to manually remove from the infected PC once detected by the unusual behavior caused by the malware. PC users infected with eFast should navigate to the Windows Control Panel and select the option entitled “Programs and Features.” From this menu, the malware can be safely uninstalled from Windows.
In the most recent reported cases of infection, eFast was found to be properly labeled in the Applications list, making it easy to find and remove. It’s worth noting, however, that this naming convention could be changed at any time, a simple action on the part of the hackers that could make finding the rogue program much more difficult for inexperienced Windows users who are unaccustomed to Programs and Features dialog in the first place.
Once eFast has been successfully removed, a legitimate copy of the Chrome browser can be downloaded directly from Google and to prevent the potential for successive infections, the use of all Web plugins should be carefully considered as this is the primary way the eFast browser is distributed among Windows machines. While the ability to completely replace one of the most heavily used Web browsers in the world in an instant is impressive, the fact that eFast is so easy to uninstall makes this threat less ominous than it might otherwise be considered.
That said, if a user is unaware of the infection and continues to use the rogue browser despite the pop-up ads and random website redirects, hackers could potentially steal login and password credentials or obtain access to private files and folders stored on the infected machine. Always be observant of changes to your Web browser that seem odd and if the use of browser plug-ins is required, make sure these plug-ins are disabled whenever they aren’t being actively used to mitigate the risk of infection from eFast or the countless other malware threats targeting your Web browser.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion