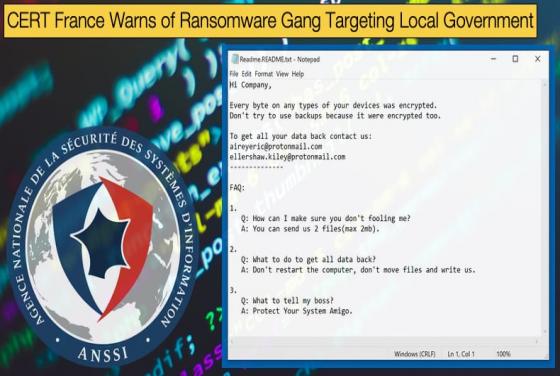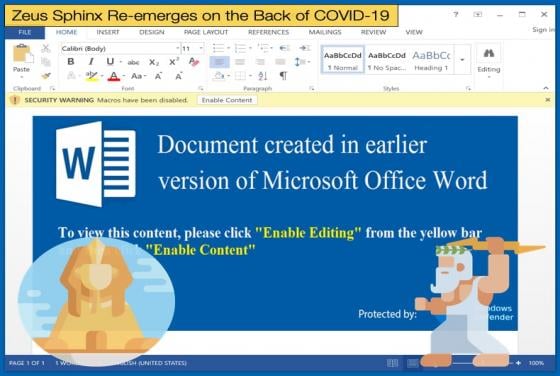

Zeus Sphinx Re-emerges on the Back of COVID-19
It is not by any means new to say that hackers are looking to exploit the COVID-19 pandemic, despite the misery and loss of human life the disease has already caused, for their own benefit. At the start of February, this publication reported on several malware campaigns exploiting the health pandemi