Emotet Raised from the Dead
Widely regarded as one of the most dangerous botnets in recent history Emotet activity stopped in May 2019. Researchers noticed that Emotet activity started picking up again in August. In less than a month, researchers have detected a new spam email campaign been distributed by the botnet. Malicious emails have been sent from the Emotet botnet have been seen spotted targeting those residing in Germany, the United Kingdom, Poland, and Italy. Further, emails have been seen sent to US individuals, businesses, and government organizations.
By June 2019 all activity on Emotet servers had ceased. On August 22, 2019, the command and control servers starting receiving requests and acting upon those requests. Researchers noticed that those behind the botnet have been actively preparing for a new spam email campaign.
This preparation involved cleaning it of fake bots, putting together new campaigns, and establishing the distribution channels including compromised websites, hacking sites, setting up web shells.
So far the following websites have been compromised to distribute Emotet spam emails:
- customernoble[.]com, a cleaning company
- taxolabs[.]com
- www.mutlukadinlarakademisi[.]com, a Turkish women's blog
- www.holyurbanhotel[.]com
- keikomimura[.]com
- charosjewellery[.]co.uk
- think1[.]com
- broadpeakdefense[.]com
- lecairtravels[.]com
- www.biyunhui[.]com
- nautcoins[.]com
Security firm Cofense Labs revealed how active the campaign has been in a relatively short period. The current campaign is targeting almost 66,000 unique emails for more than 30,000 domain names from 385 unique top-level domains. The malicious emails came from 3,362 different senders, whose credentials had been stolen. The count for the total number of unique domains reached 1,875, covering a little over 400 top-level domains. The targets also appear to be non-specific, according to researchers,
“From home users all the way up to government owned domains. The sender list includes the same dispersion as the targets. Many times we’ve seen precise targeting using a sender who’s contact list appears to have been scraped and used as the target list for that sender. This would include b2b as well as gov to gov.”
The content of the emails appears to be composed to appear financially motivated both Cofense and another security researcher James WT have been tracking the new campaign along with the spam emails sent. Many of the emails are made to look like replies to earlier conversations in an attempt to further trick end-users into downloading the malicious attachments. For emails used to target US government agencies, a special email seems to have been crafted with the intent to get the recipient to check a document sent by the operators. The details of the document are kept incredibly vague in the hope that this will further entice recipients to download the malicious document.
The Payload
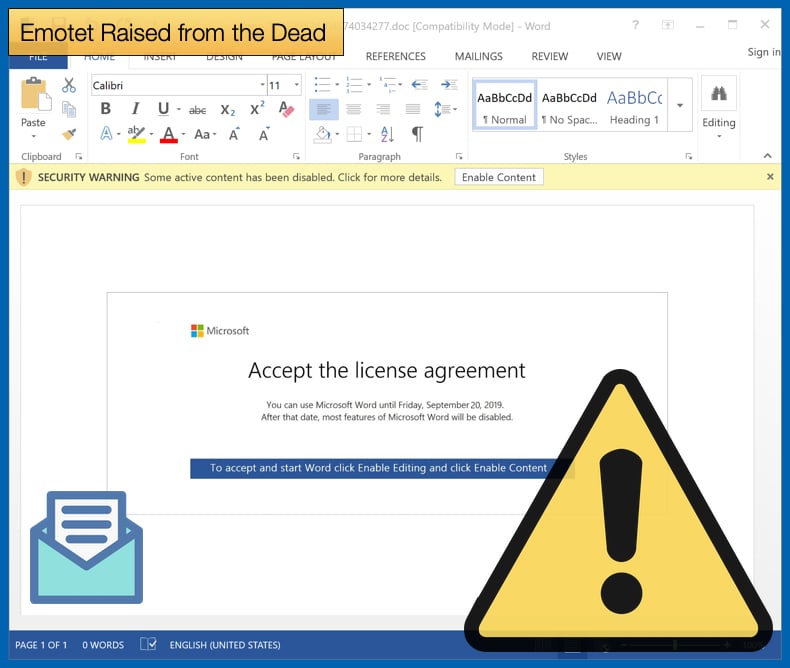
The Emotet malware which is delivered via malicious payload has often been used as a trojan so that other malware can be deployed on the victim's machine at a later date. This tactic still seems to be in place. One email seen by Bleeping Computer included malicious Microsoft Word documents. The malicious document relies on the end-user activating macros which are disabled by default in order to help prevent users falling victim to such attacks. In order to get the user to enable macros the user is presented with a fake notification asking the user to accept a Microsoft User Agreement. By agreeing to the notification the user has unwittingly enabled macros. To further try and trick the user to agree the notification states that if the agreement is not confirmed by September 20, Microsoft Word will cease to work on the machine. The notification comes complete with a Microsoft logo and does look authentic.
According to VirusTotal at the time of writing 38 out of 70 antivirus engines are now capable of detecting the malware dropped via the spam email campaign. This is a significant improvement over the earlier reported 16 detections when the new campaign was made public. Further other researchers and security firms have confirmed the campaign is active and targeting those in Poland now as well.
As mentioned above Emotet while been distributed via a botnet, the malware itself is similar to a trojan in that it is used to deliver other malware variants to victims. In the past, the Ryuk ransomware and Trickbot had been distributed in previous campaigns. Ryuk is currently, along with Dharma, the most active ransomware families on the threat landscape. It has been reported that the ransomware has netted the operators nearly four million USD. Trickbot is typically deployed as a banking trojan designed to steal banking credentials. The stolen credentials themselves are used to take over victim accounts so that funds can be fraudulently transferred to accounts under the control of the operators. It was later confirmed that Trickbot is actively been distributed in this most recent Emotet campaign.
According to researchers the use of Emotet, Trickbot, and Ryuk in recent campaigns is seen as different malware operators working together and sharing resources to get better financial returns on their actions. It has been proposed that similar to malware-as-a-service model the partnership is based on one partner gaining access to a machine or network so that another partner can exploit the backdoor created at a later time. This presents a heightened threat to both businesses and individuals as now highly organized criminal organizations can further leverage the resources of other organizations to better guarantee infections and the financial gain associated with their illegal actions. The resurgence of Emotet was expected by researchers, it was only really a matter of when would the botnet be activated.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion