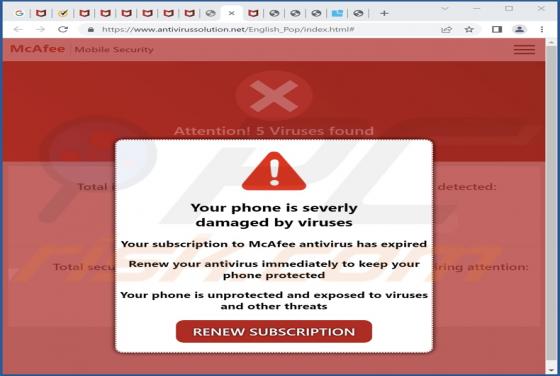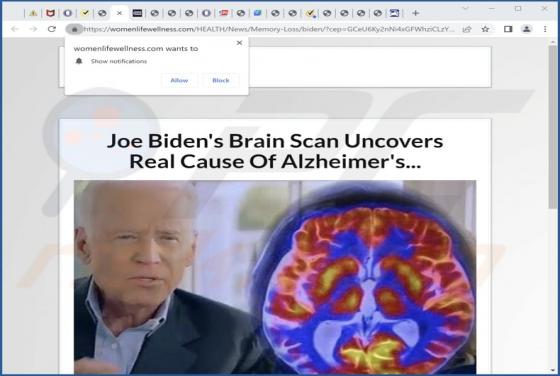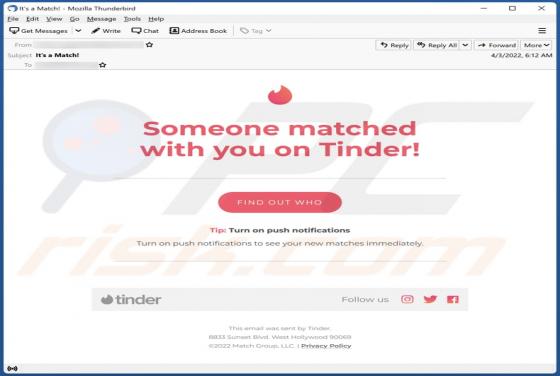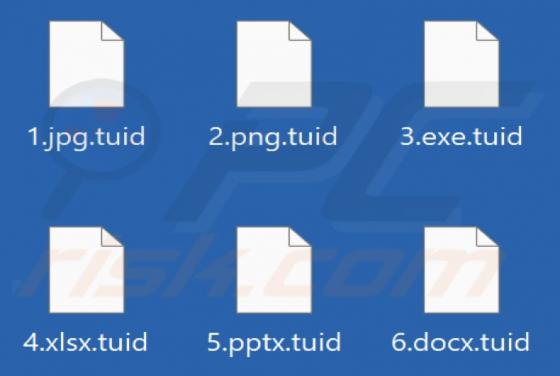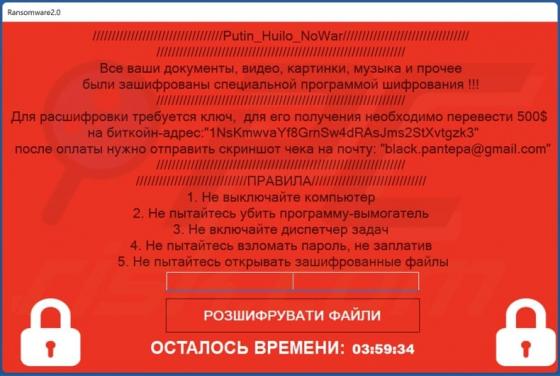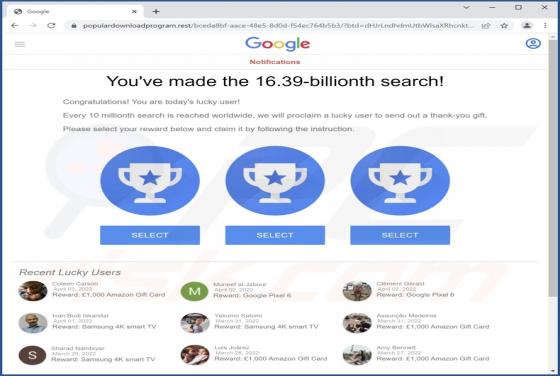
You've made the 16.39-billionth search! POP-UP Scam
During a routine inspection of shady websites, our researchers discovered the "You've made the 16.39-billionth search!" scam. It uses content (names/graphics) associated with the Google search engine, thereby implying that this reward is given or sponsored by Google LLC. In fact, this scam is in n