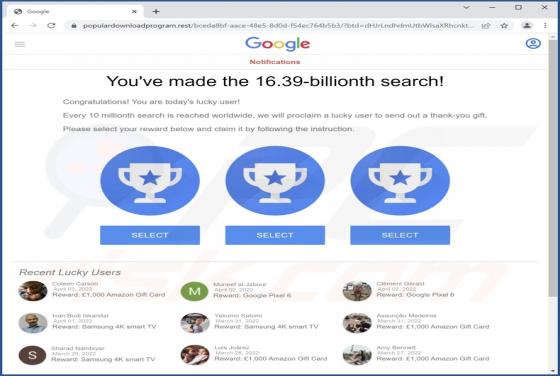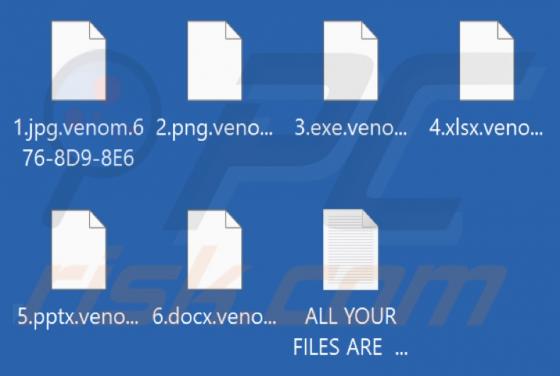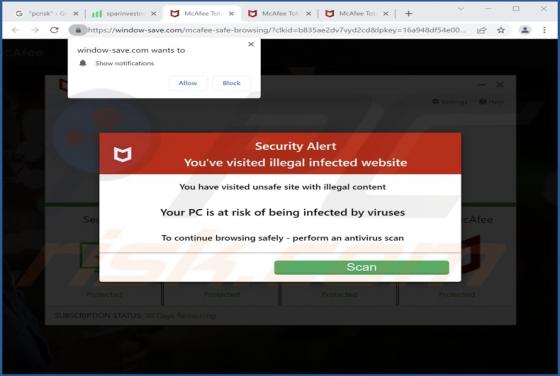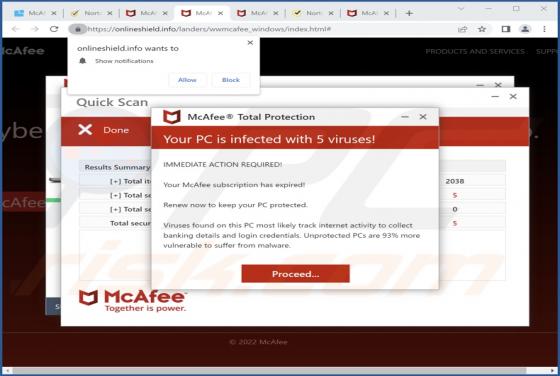
Onlineshield.info Ads
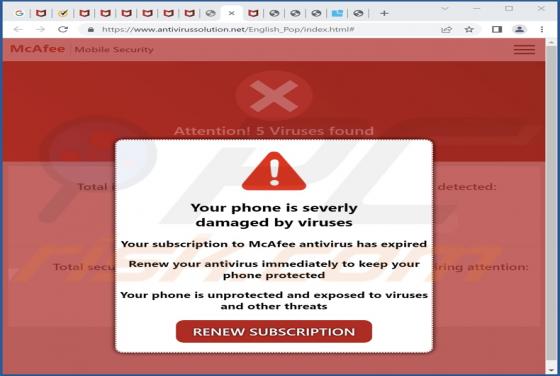
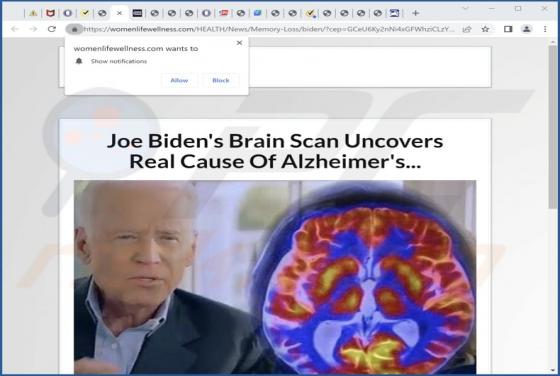
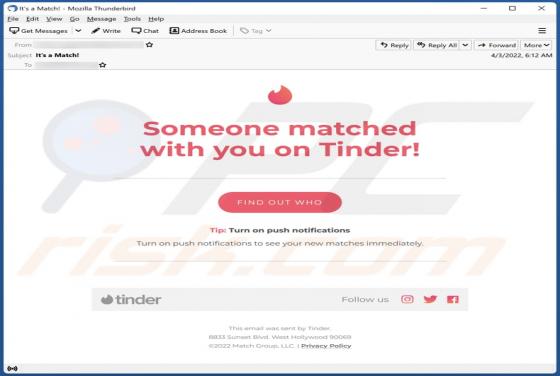
While inspecting rogue sites, our researchers discovered the onlineshield[.]info webpage. It loads deceptive content, promotes browser notification spam, and redirects visitors to other (likely dubious/malicious) pages. Onlineshield[.]info and similar websites are rarely accessed intentionally. Mo