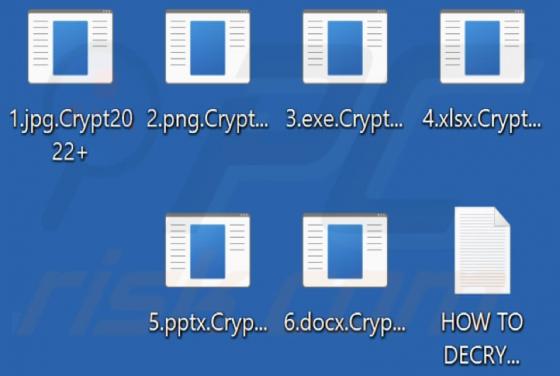
Crypt2022+ Ransomware
Crypt2022+ is ransomware that prevents victims from accessing files by encrypting them. It also appends the ".Crypt2022+" extension to filenames (for example, it renames "1.jpg" to "1.jpgCrypt2022+", "2.jpg" to "2.jpgCrypt2022+"), and creates the "HOW TO DECRYPT FILES.txt" file as its ransom note.