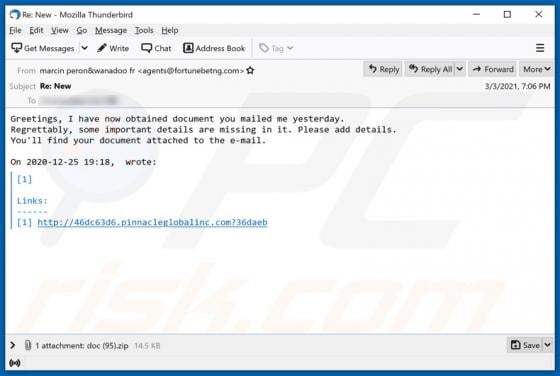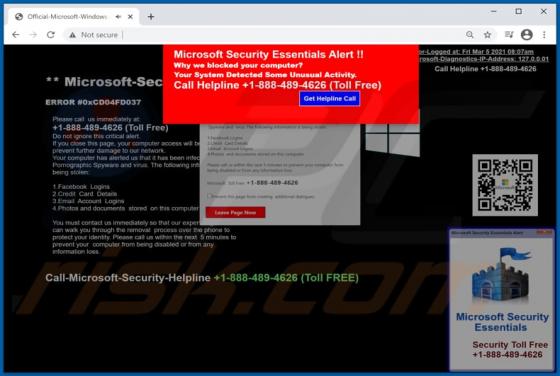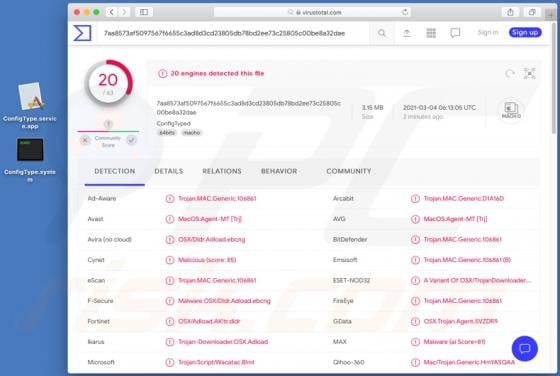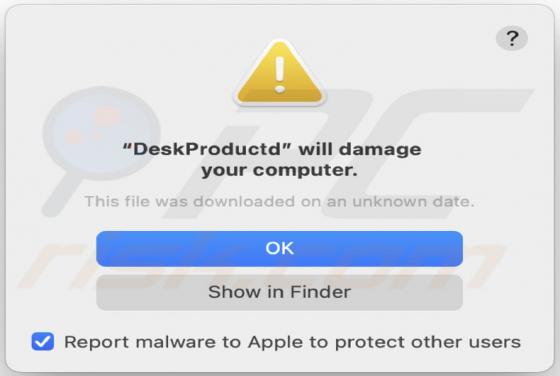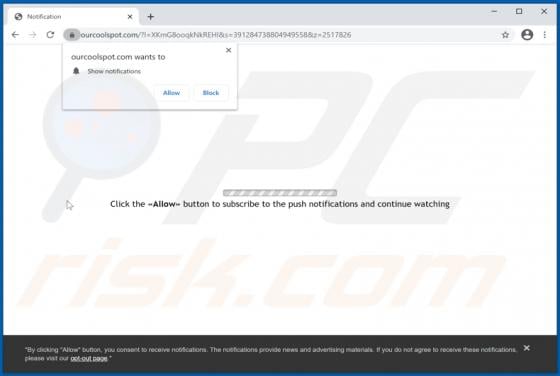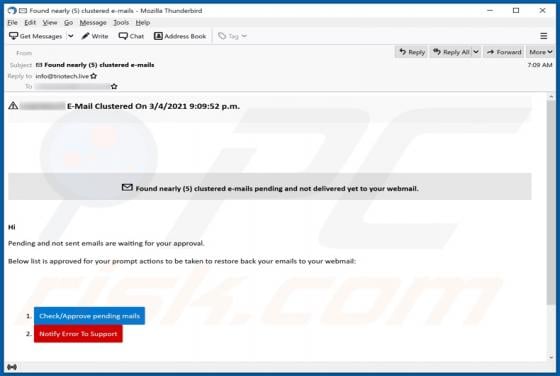
Clustered E-mails Pending Email Scam
"Clustered e-mails pending" is an excerpt from scam emails, which serves as the title for the spam campaign distributing these messages. The deceptive emails claim that recipients have messages waiting to be delivered into their inboxes. Note that the information provided by "clustered e-mails pen