Gdiview Virus
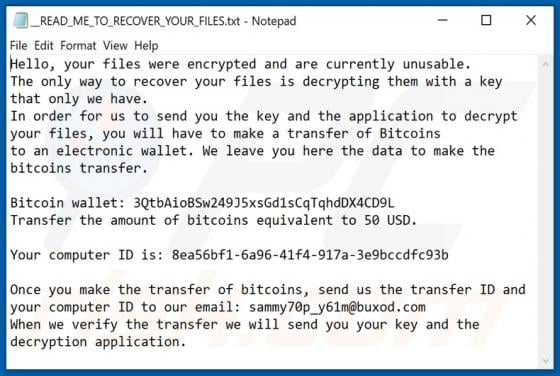
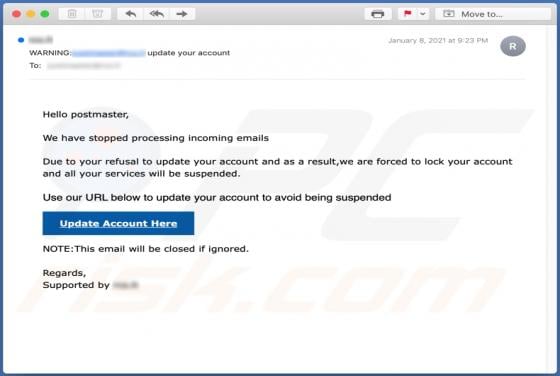
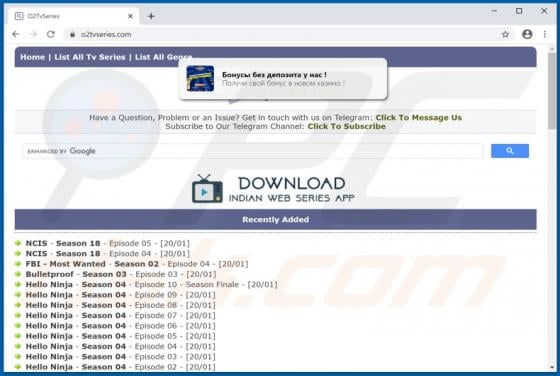
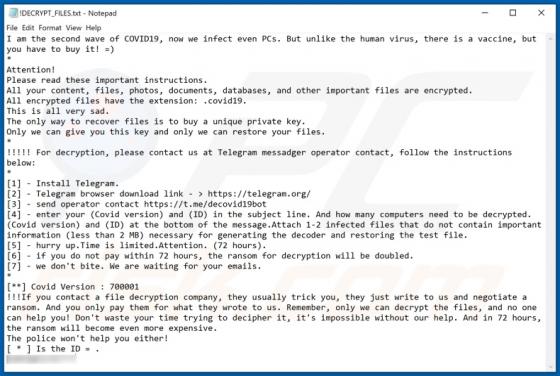
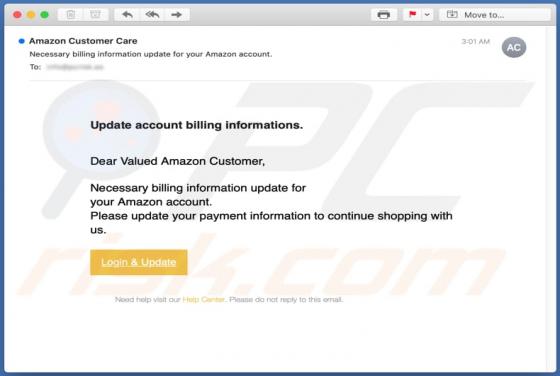
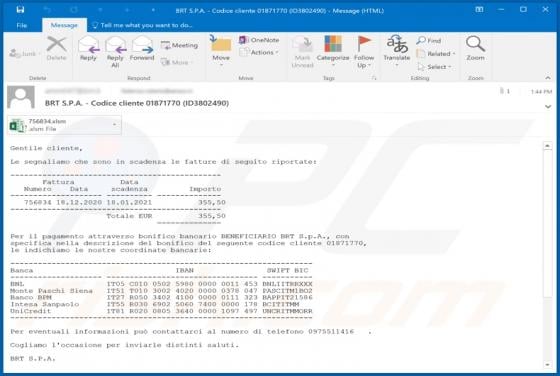
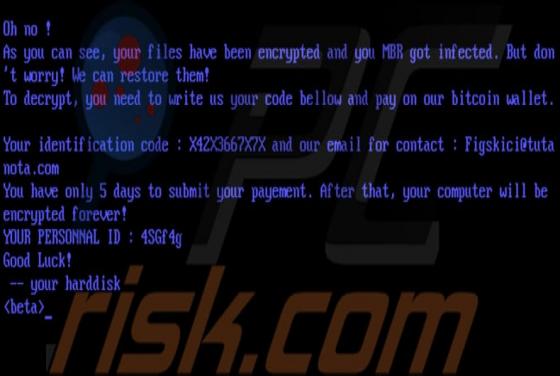
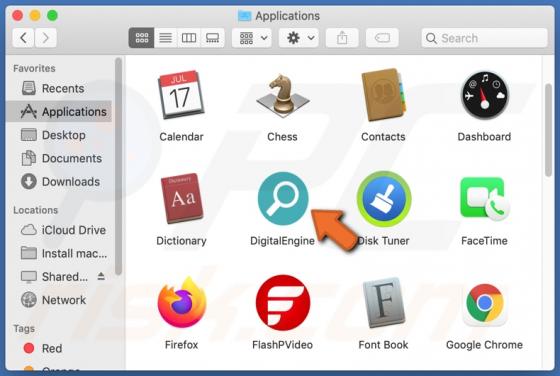
Gdiview is a potentially unwanted application (PUA) that developers distribute via a dubious web page (possibly, multiple web pages). The exact purpose of Gdiview is unknown, however, it is likely that users who install this app will also have installed adware, a browser hijacker, or other PUA. T